This course id from edX, scroll down & click “Read More” for more informations.
About this course
Blockchain is a core technology in FinTech. The original design of blockchain focused on the cryptocurrency “Bitcoin”. Due to its specific characteristics, many companies and users now find blockchain very useful for applications in many areas, not limited to cybercurrencies, including finance, logistics, insurance, medicine and even music. However, the design of blockchain involves cryptographic technology, which cannot be easily understood by those who are not professionals in the area of IT and security.
In order to better understand what kinds of applications best fit blockchain and other forms of distributed ledger technology and the potentials of these emerging technologies, it is important to understand the design rationale, the basic technology, the underlying cryptographic fundamentals, and its limitations. This 6-week online coursewill walk you through the following:
- The design rationale behind blockchain and the issues for such decentralized ledger (transaction) systems.
- The underlying technology (e.g. how the fundamental algorithms – the cryptographic primitives – work together) behind and how it makes blockchain works and safe.
- The differences of the various existing blockchain platforms and what these platforms can provide (e.g. pros and cons of the major platforms).
- What kinds of applications (both traditional and emerging) best fit the blockchain technology and how blockchain technology can benefit these applications.
- Blockchain does have its limitations. We will uncover the problems and the limitations of blockchain technology to enable developers and researchers to think about how to enhance the existing blockchain technology and practitioners to better address the issues when using blockchains in their applications.
- This course will also briefly discuss the downside of blockchain with respect to the protection of criminal activities (e.g. why ransomware always ask for bitcoins as ransom, and the money laundering problem).
The course aims at targeting a wide audience: This course will provide learners a good understanding of the technological, applicability, limitations and “illegal” usage of the blockchain technology.
What you’ll learn
- Understand the design rationale behind the blockchain technology.
- Understand the technological and cryptographic components of a blockchain.
- Understand the variations and differences of existing major blockchain platforms.
- Understand what types of applications best fit the characteristics of blockchain.
- Understand the limitations and outstanding issues of existing blockchain technology.
- Understand the negative impacts of, in particular, criminal activities in the context of blockchain.
Welcome and Course Administration
Welcome to Blockchain and FinTech: Basics, Application and Limitations
- Hello everybody.
- The upcoming Blockchain and FinTech course
- will be launched in August this year.
- It will be about blockchain technology,
- blockchain platforms, applications and limitations.
- This is a course aimed for layman learners.
- Learners will be able to understand
- the fundamental and industrial jargons,
- so that you can interact with
- key players of the industry.
- I look forward to seeing you
- in the blockchain course.
- The big rise and crash in Bitcoin market
- peaked peoples interest in blockchain technology.
- But, is Bitcoin equivalent to blockchain?
- Of course not.
- Some even think that in the near future,
- this new technology can change the way we live
- and the way we do business.
- In fact, we’ll be expecting
- new business models
- and new business opportunities.
- There’ll even be new ways of
- exchanging information online.
- But do you know what blockchain actually is?
- Take a look at the following questions.
- Do you know much about these?
- Do you know what underlying technologies
- make blockchain secure and powerful?
- What kind of applications,
- both financial related or non-financial
- are best fit for blockchain?
- How do these blockchain platforms differ?
- For example, Bitcoin, Ethereum,
- Hyperledger, Chinaledger?
- Is blockchain 100% secure?
- Can it protect your privacy?
- If not, what kinds of protections are provided?
- Why do ransomware
- request Bitcoin as payment?
- Why do people perceive cyber-currencies
- as a means of money laundering?
- If you want to get more insights,
- join the Blockchain FinTech course.
Course Outline and Syllabus
Introduction to Blockchain and FinTech: Basics, Applications and Limitations – Course Outline
Introduction to Blockchain and FinTech: Basics, Applications and Limitations is a six-week six-module course. Each weekly module compiles 6-12 lesson units (or subsections). In addition to the main units of the lesson, there are also Industry use cases highlighting real world examples and applications from different industry sectors.
The major learning activities within each lesson unit include: video discussions of major aspects with peer learners, instructor and community TA, as well as continuous assessment in the form of Quick Check questions, Polling and Word Cloud activities. In addition to these, there are a range of additional resources provided, including blockchain industry news reports, studies and useful links. There is a Conclusion Quiz at the end of each module to draw out the main messages.
Please click the link to view and download the Course Syllabus.
| Module 1 Blockchain technology: Why, What, How | |
| 1.1.1 | Why Do We Need a Decentralised Ledger System? Part 1 |
| 1.1.2 | Why Do We Need a Decentralised Ledger System? Part 2 |
| 1.2 | Having a Centralised Trusted Party – Advantages and Disadvantages |
| 1.3 | Security, Integrity and Privacy Issues of a Decentralized System |
| 1.4 | Blockchain – A Technology that Makes Sense with Trust and Coordination (An Interview with Charles d’Haussy from ConsenSys) |
| 1.5 | What Are the Main Barriers to Blockchain Adoption? (Charles d’Haussy from ConsenSys) |
| 1.6 | Why Use Blockchain Technology? (Henri Arslanian from PwC) |
| Ref | Reference Videos from Introduction to FinTech |
| Introduction to FinTech Module 2.9A What is Blockchain? (Part 1) | |
| Introduction to FinTech Module 2.9B What is Blockchain? (Part 2) | |
| Module 2 Technological and Cryptographic Elements in Blockchain | |
| 2.1.1 | Cryptographic Elements: Public Key & Private Key |
| 2.1.2 | Cryptographic Elements: Digital Signature & Hash Value |
| 2.1.3 | Cryptographic Elements: Real-life Scenario Challenges |
| 2.2.1 | Cryptographic Technology: Key Questions for Blockchain |
| 2.2.2 | Cryptographic Technology: Who can Modify Transactions? |
| 2.2.3 | Cryptographic Technology: Who will Maintain Transactions? |
| 2.2.4 | Cryptographic Technology: How to Protect Our Privacy? |
| 2.2.5 | Public-key Cryptography (Prasanna Mathiannal from MaGEHold) |
| Module 3 Blockchain Platforms | |
| 3.1.1 | Classification of Blockchain Platforms (Part 1) – An Overview of the 5 Key Perspectives |
| 3.1.2 | Classification of Blockchain Platforms (Part 2) – Perspectives No. 1 and 2 |
| 3.1.3 | Classification of Blockchain Platforms (Part 3) – Perspective No. 3 |
| 3.1.4 | Classification of Blockchain Platforms (Part 4) – Perspectives No. 4 and 5 |
| 3.1.5 | Highlights of Major Blockchain Platforms |
| 3.2.1 | What is Ethereum? (Charles d’Haussy from ConsenSys) |
| 3.2.2 | What is Ethereum’s Place in Today’s FinTech Ecosystem? (Charles d’Haussy from ConsenSys) |
| 3.4.1 | Trustlessness and Immutability of Blockchain Technology (Charles d’Haussy from ConsenSys) |
| 3.4.2 | Proof of Work and Proof of Stake (Charles d’Haussy from ConsenSys) |
| 3.5.1 | Tokenizing (Charles d’Haussy from ConsenSys) |
| 3.5.2 | What is a Token? (Charles d’Haussy from ConsenSys) |
| 3.5.3 | Tokenizing Shares and Fund Raising (Charles d’Haussy from ConsenSys) |
| 3.6 | What is Hyperledger? |
| Module 4 Blockchain Applications | |
| 4.1.1 | 6 Selection Criteria for Blockchain Applications (Part 1) Key Factors 1, 2, 3 |
| 4.1.2 | 6 Selection Criteria for Blockchain Applications (Part 2) Key Factors 4, 5, 6 |
| 4.1.3 | 6 Selection Criteria for Blockchain Applications (Part 3) Best Fit Applications |
| 4.1.4 | 6 Selection Criteria for Blockchain Applications (Part 4) Decision Making |
| 4.2.0 | Blockchain and Enterprise – A Technology of Coordination (Charles d’Haussy from ConsenSys) |
| 4.3.1 | Why Permissioned Blockchains Are Used in Enterprise Network? (Dr. Paul Sin, Consulting Partner from Deloitte, China) |
| 4.3.2 | Use Case: Blockchains for Trade Finance (Dr. Paul Sin, Consulting Partner from Deloitte, China) |
| 4.3.3 | Use Case: Blockchains for Supply Chain Financing (Dr. Paul Sin, Consulting Partner from Deloitte, China) |
| 4.3.4 | Use Case: Cross Border Connectivity – Trusted Data Transfer (Dr. Paul Sin, Consulting Partner from Deloitte, China) |
| 4.4.1 | How to Deploy an Application on the Ethereum Blockchain? (Charles d’Haussy from ConsenSys) |
| 4.4.2 | Use Case: Bounties Award Ethereum for Cleaning Beaches (Charles d’Haussy from ConsenSys) |
| 4.4.3 | ConsenSys and the Ethereum Platform (Charles d’Haussy from ConsenSys) |
| 4.4.4 | ConsenSys Use Case: Project i2i (Charles d’Haussy from ConsenSys) |
| 4.5.1 | Blockchain Use Case: More on Trade Finance and Supply Chain (Anil Kudalkar from MaGESpire Partners) |
| 4.5.2 | Blockchain Use Case: Capital Markets (Anil Kudalkar from MaGESpire Partners) |
| 4.5.3 | Blockchain Use Cases on General Government Services & Sustainable Livelihood (Anil Kudalkar from MaGESpire Partners) |
| Module 5 The Limitations, Opportunities and Challenges of Blockchain | |
| 5.1.1 | 5 modules in Blockchain system |
| 5.1.2 | Limitations of Blockchains (Part 1) |
| 5.1.3 | Limitations of Blockchains (Part 2) |
| 5.2.1 | Risks and Limitations of Blockchain: Privacy (Malcolm Wright from Diginex) |
| 5.2.2 | Risks and Limitations of Blockchain: Security (Malcolm Wright from Diginex) |
| 5.2.3 | The Five Security Risks of Blockchain (Alan Cheung from Hong Kong Applied Science and Technology Research Institute (Astri)) |
| 5.3.1 | Applied Smart Contracts: Opportunities, Risks, and Applications for Enterprise (Jon Rout from Digital Asset) |
| 5.3.2 | Applied Smart Contracts (DAML): Step-by-Step Example (Jon Rout from Digital Asset) |
| 5.4.1 | Use Case: Blockchain for Health Insurance (Alan Cheung from Hong Kong Applied Science and Technology Research Institute (Astri)) |
| 5.4.2 | Use Case: Blockchain & PropTech (Alan Cheung from Hong Kong Applied Science and Technology Research Institute (Astri)) |
| 5.4.3 | What Are the Benefits of Blockchain in Banking? (Johnny Cheung from B.C. Holdings) |
| 5.4.4 | How Can Blockchain Technology Benefit the Healthcare Industry? (Johnny Cheung from B.C. Holdings) |
| 5.4.5 | Institutional Investment Opportunities in the Digital Asset Space (Henri Arslanian from PwC) |
| 5.5.1 | Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 1) (Brian Tang from Asia Capital Markets Institute (ACMI)) |
| 5.5.2 | Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 2) (Brian Tang from Asia Capital Markets Institute (ACMI)) |
| 5.5.3 | Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 3) (Brian Tang from Asia Capital Markets Institute (ACMI)) |
| 5.5.4 | Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 4) (Brian Tang from Asia Capital Markets Institute (ACMI)) |
| Module 6 The “Evil Sides” of Blockchain and Legal Regulations for Blockchain | |
| 6.1.1 | The Evil Sides of Blockchains Part 1 Ransomware |
| 6.1.2 | The Evil Sides of Blockchains Part 2: Money Laundering |
| 6.1.3 | The Evil Sides of Blockchains Part 3: Cyber Currencies |
| 6.1.4 | The Evil Sides of Blockchains Part 4 Cyber Security Exchanges |
| 6.2 | The “Dark” Side of Blockchain (Bowie Lau from MaGESPire) |
| 6.3 | Criminal Use of Payment Blockchains (Malcolm Wright from Diginex) |
| 6.4 | The Role of Financial Regulations for Blockchain (Professor Douglas Arner, Faculty of Law at the University of Hong Kong) |
| 6.5 | Does Blockchain Need Legal Regulations? (An Interview with Charles d’Haussy) |
| 6.6 | Global Digital Assets Regulatory Trends (Henri Arslanian from PwC) |
Module 1 Blockchain Technology: Why, What and How
Welcome to Module 1

Meet Module 1 Guest Speakers

Module 1 Learning Objectives
After completing Module 1, learners should be able to:
- Understand the differences between a distributed system and a decentralised system;
- Understand the advantages and disadvantages of having a centralised trusted party to process and store transaction data of an application;
- Understand the advantages and issues to be resolved of a decentralised system.
Think about this
Do you know the difference between a “decentralised” and “distributed” systems?
Why do we need a decentralised ledger?
Why Do We Need a Decentralised Ledger System? (Part 1)
- Before we start,
- there are two terms I want to clarify.
- You always see these terms in the internet.
- One is called decentralised system.
- The other is distributed system.
- Distributed system actually refers to
- a system that can store or process data
- in different locations.
- But whether it is a decentralised system,
- depends on how and where
- the decision making is made.
- Decentralised essentially means
- there’s no single point or single party
- who can make the final decision
- of how the system behaves.
- So, every party can make a decision
- for its own behaviour,
- and the resulting behaviour of the whole system
- will be the aggregate responses
- from the individual parties.
- Simply speaking, decentralised means
- that there’s no single authority
- who can control or decide what the system should do.
- In contrast, you can imagine Google search engine
- is basically a distributed system,
- but is not decentralised.
- It still relies on thousands of computers
- in different locations to check the web,
- to crawl the web
- from different locations of the world,
- but then the whole system is owned
- and controlled by Google.
- So, in other words, Google is the only organisation,
- only party who can control the whole system.
- So, that’s why it’s not qualified
- as a decentralised system.
- Now, then the immediate follow-up question is:
- Why do we need a decentralised ledger system?
- Before I talk about this,
- let’s look at the history.
- Let’s start at the very beginning.
- Why do we need banks?
- We need banks because we need a trusted organisation
- to help us to store our money.
- Otherwise, it’s really dangerous
- to keep our money at home.
- The bank, as a centralised trust party,
- will keep track of all our money accounts
- of all the customers.
- In other words, the bank will keep a centralised ledger
- for all these accounts.
- And the bank is the only one who is responsible
- for the integrity and validity,
- that is, the correctness of all the transactions
- in these accounts.
- Let me give you an example.
- If a Person A wants to transfer $100
- to a Person B, the bank will try to track
- if A has enough money in his bank account
- before allowing the transaction.
- And of course, the bank will also try to mark down
- this transaction clearly in the ledger if it’s completed.
- And both the party A and B
- will not have any worry about if the transaction is faked
- because we all trust the bank.
- Now but then, why the bank is willing to do this for us?
- The bank can actually make use of our money
- to invest and try to earn more money on their own.
- That’s why they are willing to provide this service for us.
- Now, in order to attract more customers
- to deposit the money in the bank,
- the bank will give the customers interest in return.
- So, it is basically the relationship
- between the customer and the bank.
- So far so good, right?
- The customer right now has a trusted party, the bank,
- to help handle his money account
- with the benefit of getting interest as well.
- Now, on the other hand, the bank can make use of
- the customer’s money to make more money.
- As time went by, the services or the funds
- of the bank has evolved a lot.
- If you look at the current situation,
- there’re many, many services
- provided by the bank now,
- for example, bank loans, money exchange,
- inter-bank transfer, electronic money transfer,
- auto pay or even investment.
- So, it seems like we are having
- such a centralised authority,
- it’s very good.
- However, let’s now take a closer look at this
- to see if it’s really that good
- to have a centralised party helping us
- with all these transactions.
1.1.2 Why Do We Need a Decentralised Ledger System? (Part 2)
- First, you all know that
- these services may not come for free.
- We probably have to pay transaction fees.
- For example, is some countries we need to pay charges
- when we are using ATM transactions,
- cashier’s cheques, money orders, bounced cheques
- wire transfer, safety box, investment transaction,
- or even they impose a minimum balance in the account,
- otherwise, you have to pay a charge.
- Pick the wire transfer as an example.
- If you have a son studying abroad in the U.S.,
- you want to send him some money
- from Hong Kong to the U.S.
- both the banks in Hong Kong and the U.S.
- will charge you a transaction fee.
- They may also have minimum
- or maximum requirements
- on the amount of money that can be transferred.
- Now, having a middle man,
- a trusted centralised party
- for transactions and business is not uncommon
- in the real world.
- There are many, many examples.
- Now, let’s try to look at a few.
- In China, there’s a place called Guiyang.
- They established something called
- the Global Big Data Exchange.
- This exchange has been established
- for three years already.
- It provides a centralised platform for the customer
- to trade, buy and sell the data.
- So, basically it’s a data trading centre.
- How it works, the data owners deposit their data
- into the platform just like what we do for the bank.
- We deposit the money in the bank.
- And the buyers could go to the platform
- and try to purchase the selected data from the platform,
- based on what data are provided by the data owner
- and what data will be required by the buyers.
- And the centralised party,
- the platform, will try to coordinate
- this buying and selling activities or provide services
- to help match the buyers and sellers.
- You all know it, right?
- Of course, the service is not for free.
- The platform charges a transaction fee.
- The transaction fee can be as high as
- 40% of the whole transaction amount.
- For example, if you are going to pay $1,000
- to buy and sell data,
- you are going to pay $400 to the platform.
- Now this is only one example.
- There are many, many other examples.
- Let me give you another remarkable example.
- Matchmaking service is very common now.
- You can see that the company,
- the platform providing this service,
- can be considered as our centralised trusted party,
- and of course the service is not for free.
- To use the service,
- to find the potential dating partners or candidates,
- in most cases,
- a customer has to pay membership fee
- and, if they successfully arrange a dinner
- for you and the potential candidate,
- they may even charge you another service charge.
- Think about it.
- If it’s possible to eliminate the centralised party,
- we may not need to pay this transaction fee.
- Now, in fact, having a centralised party
- to look after our transaction
- also comes with the privacy issues.
- It’s very obvious that
- the bank, the centralised party, the platform,
- is able to look at all your transactions.
- For example, to whom you want to give your money to,
- how much money you have exchanged
- for foreign currencies,
- how much money you have wired to your children,
- and of course, all of your investment via the bank.
- If you look at the love matching example,
- the privacy issue is quite obvious, right?
- Because you need to pass your personal information
- to the platform and also the criteria
- for choosing your partner, for example,
- what kind of girls you like, etc, and of the privacy,
- you totally rely on the service provider.
- And this service provider
- will have full access to the information,
- which couples have communicated
- and when and where they go for dinner
- and who want to date which one.
- And, of course, you may not even want others to know
- that you have register for this kind of service.
- And for the big data exchange example,
- there are also some privacy issues.
- The platform, because you deposit your data over there,
- so the platform has all the authority
- to look at every single piece of data,
- and there is no absolute guarantee
- that the platform will not use your data
- for other purposes.
- And, of course, the platform also know
- every single transaction of every trade,
- who buys a piece of data, who sells it, who owns it
- or for how much the data was sold.
- Sometimes, time is also a concern
- because we have to rely on the centralised party
- to process the transaction.
- In most of the cases, it will take time.
- For example, if you want do a wire transfer
- to someone in another country,
- it may take the bank days to complete the transaction.
- And the bank probably may also have other restrictions,
- for example, they may have a restriction
- on the minimum or maximum amount
- that you can transfer for one time.
- And depending on the nature of the transaction
- and/or the applications,
- some transactions may involve multiple parties
- and many steps in the procedures.
- As a simple example,
- let’s consider a mortgage loan.
- From the time you want to apply for a mortgage loan
- till you really get the mortgage loan,
- maybe you have the experience.
- It will take more than 20 days, or a few weeks, right?
- In fact, inside this process,
- there are many parties to be involved.
- For example, the borrowers need to work with
- different parties to provide proofs of his salary,
- his employment, his credit history, etc,
- And the bank may also need to work with
- many other parties, for example, surveyors
- to evaluate the property for the loan
- based on the current market price.
- And the bank may also need to
- interact with other parties,
- such as the land registry
- to verify the ownership of the property.
- Then, you can imagine that
- everything goes back to the centralised party,
- that’s the bank in our case,
- then it would become the bottleneck of the procedure.
- And, of course, if you want to look for a mortgage loan,
- you are not going to ask a single bank to do it.
- Usually we try to seek services
- or make enquiries from multiple banks.
- And of course the banks will not work together.
- They will not share information at all.
- So, it creates a lot of redundancy
- in the transactions as well.
- Now, you think about it.
- Imagine that if there’s a platform in which
- some information is given access to every bank
- if the customer agrees,
- the validation process of opening a bank account
- in different banks for the same customer
- would be a lot easier,
- and you can save a lot of time.
- But if we are having the concept
- of a centralised system,
- this platform is not easy to build
- because no one is going to trust one single authority
- who have full control of this platform
- with the exception of the government.
- In other words,
- it’s not easy to have a commonly trusted party
- to manage the operation of the system.
- If you can follow what we have discussed so far,
- you may wonder is it possible to do all these
- without a centralised party?
- For example, without a bank,
- you know, this is the reason why blockchain
- or a decentralised ledger system was proposed.
- But on the other hand,
- not all applications or systems are suitable to be a kind.
- We’ve also discussed what kind of applications
- are best fit for decentralised systems
- in the later part of the course.
Think about this

Banking transactions demand adequate security. What are the advantages and disadvantages of a centralised and decentralised system in bank services such as payment and remittance?
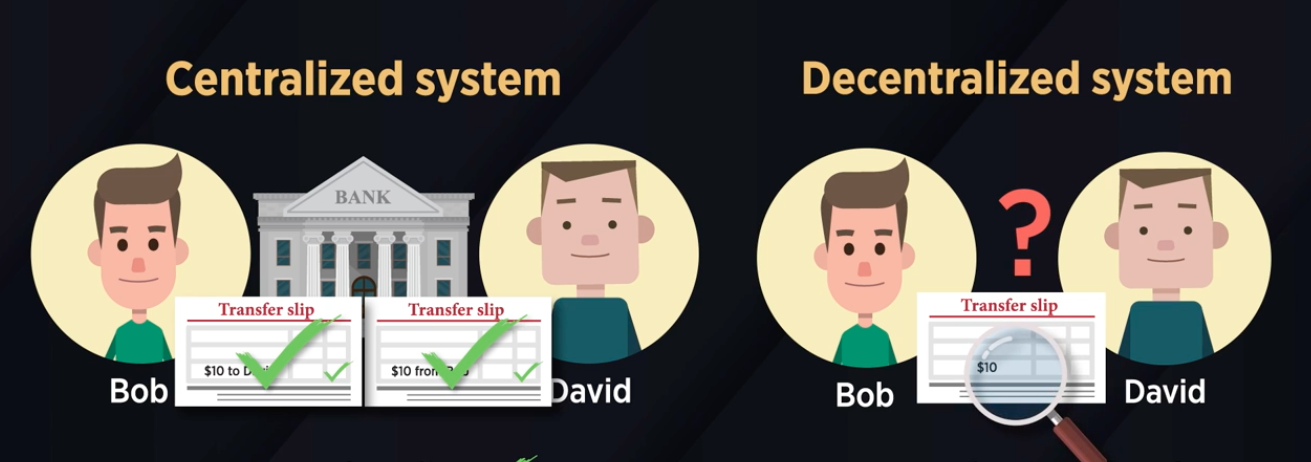
1.2 Having a Centralised Trusted Party – Advantages and Disadvantages
- I hope you are now convinced
- why we need a decentralised system.
- However, a decentralised system
- is not owned by anyone
- but by all the users who use the system,
- so in other words
- all the users of the system
- have to work together
- to maintain the whole system
- so the big question is,
- is it really feasible?
- What will be the issues there?
- To understand the issues
- of building a decentralised system
- for an application,
- let’s try to look at the bank accounts
- as an example.
- Now assume that
- we have already opened an account in a bank.
- We have mentioned that the bank can help us
- to maintain our account ledgers,
- deposit money into the account,
- withdraw money from the account
- and transfer some money from one account
- to another account.
- Now imagine that I try to deposit 15 coins
- into my own account.
- The bank provides you a deposit slip
- and the account balance is recorded.
- Now on the other hand,
- if you do not have a bank,
- how can you confirm
- that you have actually deposit 15 coins
- into the account?
- Another example.
- If Bob wants to transfer 10 coins to David
- with a bank, you can sign a transfer slip
- to authorise it and both you and Bob
- has no doubt about the transfer.
- The bank has processed it.
- However, if we don’t have a bank,
- how can one authorise the transfer?
- How can one check if the transaction is valid?
- In other words,
- how can we guarantee that Bob
- has 10 coins in the account
- so that he can transfer the coins to David?
- Now with a centralised party,
- the bank will keep track
- of all transactions for its customers
- and account balance for its customers,
- so if one person wants to transfer
- a certain amount to another account,
- the bank will verify if the person
- has enough money to do so or not,
- but then if you’re without a bank,
- without a centralised party,
- how can this be done?
- One simple solution is
- how about we just put
- all the transaction details,
- all our accounts on the internet.
- Then everybody can get a copy
- and help to check it.
- Now if A wants to transfer $60 to B,
- then everybody can see whether A has enough money
- in the account
- and whether the transfer can be done legitimately
- and of course now that the transaction has been done,
- a new record of the transaction can be written
- on the internet-based ledger as well.
- Then both A and B can see clearly the changes
- in the account and the transaction can be done
- very fast too.
- Since we put all the details
- of all the transactions and the accounts on the internet
- so everybody can check it
- and all actions are transparent, am I right?
- But the problem is in the bank,
- the bank will be responsible for all the accounts,
- all the transactions.
- More importantly the transaction details
- and the accounts are kept by the bank
- and the bank can make sure
- that nobody, no unauthorised people
- can modify the transaction
- or the account can easily be changed.
- But now the whole ledger is available
- in the internet, everybody is authorised
- has the right to download a copy,
- so can anybody modify the transaction easily?
- Do we have a mechanism to make sure
- that this is not possible?
- Or can anyone add/delete transactions easily?
- How to give the authorization
- to transfer money from your account
- to another account,
- who actually is responsible to maintain the account?
- Maintain the ledger?
- Who’s going to check the validity of a transaction?
- You see there are many, many problems.
1.3 Security, Integrity and Privacy Issues of a Decentralised System
- Now, let’s try to talk about the issues in more detail.
- To make it very simple, if it’s very easy for one
- to modify the transaction details,
- then the system becomes useless
- because we cannot trust
- the ledger that we download from the internet.
- For example, if I transfer $10 to B today,
- but then, tomorrow, I don’t want to transfer
- the money to B, so what can I do?
- I go to the internet,
- download the ledger, erase my record,
- or even say that B actually transferred $6 to me instead.
- Then, I put the ledger back in the internet.
- Then, everybody will download my new ledger
- and think that B actually transferred
- $6 to me instead of I transfer $10 to B.
- Then, you can see that the system becomes useless.
- Nobody’s going to trust it.
- So how to guarantee that only the account owner
- can initiate a transaction of his own money?
- This is actually a security issue.
- Now, if it cannot guarantee
- the transactions are error-free,
- for example, if the transaction is transferred
- even if the paying account
- does not have enough money,
- then we will think that the system is useless as well.
- Therefore, you can imagine that integrity
- is really, really a big issue.
- So whether we can trust the transaction detail
- on the internet is of question.
- Now, of course,
- you can see that with a centralised system,
- the bank can check every transaction,
- whether it’s valid or not, but in a decentralised system,
- everybody’s an owner.
- We don’t know who is going to check
- if the transaction is valid.
- This is also an integrity issue.
- Now, if the ledger is maintained
- by all users, so everybody may get a copy.
- So if some problems occur,
- which copy is the correct one?
- Which copy can we trust?
- You can see that there are many, many questions
- related to security and integrity.
- In fact, who is responsible for adding new transactions
- into this global ledger is also an issue,
- is also a problem.
- Now, if you look at it very carefully,
- there’s one more important question.
- If you put everything on the internet,
- every transaction on the internet,
- so everybody can have the authority to look
- at all the details, all the accounts, all the transactions,
- as they are all the owners of the platform,
- then it seems like the protection of privacy
- in comparison to a bank is even worse.
- You think about it.
- In case of a bank, only the bank can look
- at all the transactions for its customers,
- but in a decentralised system,
- it seems like everybody can
- go to the blockchain platform
- and look at all the transactions.
- Now, I hope you learned enough to understand that if
- we are going to have a decentralised system,
- there are many, many issues to be resolved.
- Okay, let me summarise the lecture of this module.
- Now, if we are going to have a centralised party,
- like a bank, to help us to keep our money,
- there are some disadvantages,
- such as we need to pay high transaction fee,
- the privacy concern because the bank
- can know everything about us, about the transactions,
- and also the processing time
- may depend on the centralised party,
- and if we are going for multiple parties,
- multiple service providers, you may need to repeat
- the same tedious procedures for every provider
- because they don’t share information.
- Now, on the other hand,
- if we try to go for a distributed ledger,
- the ledger is going to be maintained by all users
- and we may have other concerns
- to maintain the system,
- such as security, integrity, and a privacy issue.
- Now, in the next lecture, we’ll try to take a closer look
- at the blockchain technology
- on how these issues can be resolved.
Meet Guest Instructor Charles d’Haussy (ConsenSys)

1.4 Blockchain – A Technology that Makes Sense with Trust and Coordination (An Interview with Charles d’Haussy from ConsenSys)
- I would like to give you my definition of blockchain,
- because blockchain is a very complex technology
- and it makes it a very difficult technology
- to explain sometime.
- So, some people go in the technical explanations,
- explaining to user,
- there’s a distributed ledger infrastructure
- as information is shared.
- But when you talk to a large audience,
- it’s actually hard for the people to start to picture
- what is this flow of information.
- So the way I like to explain,
- what is blockchain technology,
- is really to explain that
- it is a technology about coordination.
- It’s a technology helping people,
- helping organisations to organise themselves
- in a trustless manner.
- And if you’re a technical person,
- we can talk about the ledger,
- as in the way the information is encrypted
- and shared between different databases.
- But the overall takeaway,
- it’s a technology which never exists before,
- and it’s a technology which main objective
- is to help coordination.
- So the worst case of blockchain
- is trying to use blockchain
- for the sake of using blockchain,
- for every use case you want to address,
- you can always execute them
- without using blockchain.
- A central database is always possible.
- But if you want start to coordinate work
- between many, many more parties,
- and you want these parties to have a platform
- which is a trust.
- So they don’t have to trust one single player,
- but they can start to trust each other,
- then blockchain start to make sense.
- So I think a blockchain which is centralising things,
- but still using the blockchain
- for distributing things
- do not capture all the value proposition
- of the blockchain technology.
- So you really want to have a use case
- where there is so many different parties
- with such a complex coordination work
- that a blockchain will actually makes sense
- because it will be easy
- for the platform to onboard them,
- and it will be also making everyone comfortable
- to work that if you claim something
- or if you owe me something
- because I deliver your work,
- the platform is actually coordinating this work,
- and I do not need to have such a high level
- of trust with you, if I deliver a work,
- if I deliver something to you,
- I knew I’m going to be paid
- because I will trust the platform itself.
- So to speak, to the idea of having a distributed ledger
- or blockchain being distributed,
- what’s decentralisation and does it matter
- if a blockchain is decentralised or not?
- So, decentralisation is one of the value proposition
- of the blockchain’s technologies, right?
- In some cases you want to decentralise
- between a short, a small group of players,
- maybe between a bank and their customers,
- maybe between different banks
- or maybe different organisations.
- In this case, you decentralise,
- but you kind of not totally decentralise.
- So it should not be an obsession.
- Decentralisation makes sense,
- but it should not be the only obsession.
- I think we always have to come back to the problem
- you want to fix.
- You want to come back
- if you design a product
- to make sure that this product has a fit
- with the market and start your kind
- of product design journey from the customer
- and not from the technology capacities.
What Are the Main Barriers to Blockchain Adoption? (Charles d’Haussy from ConsenSys)
- So what are the main barriers
- to blockchain adoption?
- The main barriers to blockchain adoption today
- would be defining
- and launching the right products.
- Everyone is experimenting a lot on this ecosystem,
- and we see some use cases
- which are getting traction.
- So the financial use cases are
- getting a lot of tractions.
- Identity use cases
- starting to have a lot of attention.
- What we find is when there is technologies,
- the technologies are way faster than people.
- If you think of the use of the internet back in the ’90s,
- people at the beginning were very scared of the internet.
- I remember people telling me
- I will never use my credit card on the internet.
- And nowadays everyone uses credit card
- on the internet,
- because the people and the habits of the people
- have been changing.
- So today the technology is here,
- the technology is ready,
- the technology is evolving and growing every day,
- but it’s kind of practised by
- a small circle of technologists.
- And step by step, we see
- more and more people using
- these technologies
- sometimes without even knowing.
- If you think about the CryptoKitties,
- the CryptoKitties users and
- fans are not all technologists.
- They’re realising there is new type of products,
- there is new type of online interactions
- and online gaming happening.
- But slowly, slowly the use of
- the blockchain products is expanding.
- So the technology is always faster than people.
- So we have to be patient and always fine-tuning
- and finding the right products
- which will drive the adoption.
Meet Guest Instructor Henry Arslanian (PcW)

1.6 Why Use Blockchain Technology? (Henri Arslanian from PwC)
- Hi there, very excited to be there.
- As most of you know, my name is Henri Arslanian
- and really my passion and my focus in life
- is the future of the financial service industry.
- Ok, now you may be wondering
- what’s happening with blockchain,
- and when it comes to institutional players.
- Well, there’s also a lot of activity there as well.
- For example, the vast majority
- of financial institutions around the world now
- are working on some kind of blockchains.
- And there’s many inherent advantages.
- For example, a lot of the benefits,
- like transparency, traceability, immutability,
- are actually very beneficial in many use cases.
- However, we are still at the early days
- when it comes to blockchain technology
- becoming mainstream.
- For example, a lot of financial institutions today
- are still at the experimentation level.
- They are doing what we call proof of concept (PoC)
- pilots potentially.
- But very few are moving it to production,
- or using blockchain inside
- their current infrastructure.
- There’s numerous use cases going on right now
- in the world that are very, very interesting.
- Not only issues like digital identity.
- Imagine if you’re able to
- put your identity on the blockchain,
- and then you can let people
- access it as you want it or not.
- Or remittance, like we discussed.
- If you want to send money back home,
- or supply chains, smart contracts, trade finance,
- the list goes on and on.
- Let me cover some of them in more detail.
- For example, let’s start with one
- that is a big problem today, supply chain.
- Think about elements like diamonds,
- or elements like, you know,
- companies like Walmart
- or other big grocery stores,
- who want to track where their food is coming.
- We’re seeing now increasingly use cases
- where people are using it for food traceability.
- For example, if you’re a young mom in Shanghai,
- who wants to go buy their milk at a grocery store,
- you want to make sure
- that it’s actually coming
- from that farm in New Zealand
- you believe it comes from.
- And blockchain actually enables us
- to these traceability opportunities.
- But also, imagine
- if you’re buying a diamond,
- for a close friend, for your future wife, or whatever.
- You want to be able to trace that diamond
- is not a blood diamond,
- that it actually had a source,
- you know where it was coming,
- there was no human trafficking involved.
- And blockchain technology enables this,
- and we’re going to see over
- the next couple of years
- a number of use cases
- when it comes to traceability.
- Another one is smart contracts.
- This has been very interesting as well.
- The beauty of a smart contracts
- within blockchain technology
- enables you to actually code a language
- inside the smart contracts,
- and whenever you have an independent event
- that is happening, you have basically
- the contract operates on its own.
- A great example of this was
- in the insurance sector.
- One of the large insurance companies in Europe,
- launched a test, AXA,
- where they did kind of a flight insurance
- on flight delays.
- All flight times, arrival times
- and take-off times are all public,
- so whenever the flight was
- delayed more than two hours,
- automatically, you can get paid for
- your insurance payment on the spot.
- And then there’s many other use cases.
- For example, we look at the remittance space.
- For me personally, it really bothers me
- to see how much fees are still paid
- every year in remittance,
- especially by those
- who cannot afford them,
- who can afford the least.
- The beauty with blockchain technology
- now is we’re really having
- more and more mainstream cases
- of how we can use blockchain technology,
- but especially digital currencies,
- in facilitating these cross border
- payments and remittances.
- But then again, we have a lot of challenges.
- Make no mistake, implementing
- blockchain technology is not easy.
- For example, in many cases it’s still
- quite costly to actually implement it.
- The other big thing is, as is often
- in many cases, still we are not seeing
- direct cost reduction or cost savings.
- One of the reasons for that
- is actually cloud offerings
- are becoming increasingly cheaper,
- and in many cases
- have a lot of security features
- that are available as well.
- Another big challenge is scalability.
- Think if you’re a large company
- that has operations in 150 or 200 countries,
- and over a billion customers.
- You need to be able to use some technology
- that is very scalable.
- And this is actually one of the challenges
- we see with some blockchains,
- is actually that they have scalability limits.
- That they are not able to process
- as many transactions every second
- as many were expected.
- The other big difficulty
- is actually regulatory uncertainty.
- You know, unless you are able to get
- some regulatory clarity,
- many traditional financial institutions
- are reluctant to get more involved,
- because they don’t know
- how regulators will react.
- A final last one,
- last trend that we are seeing
- when it comes to blockchain adoption,
- it really depends on the people
- inside your organisation.
- For example, you know, if you are
- 6 months away from retirement,
- and you don’t want to rock the boat too much
- and shake things up too much before you retire,
- you are unlikely to come and pitch for blockchain
- to be implemented inside your organisation.
- So it really depends on where people are.
- These are risky projects.
- Anybody who has done any kind of deployment
- of a new technology inside of financial institutions
- knows how difficult it is,
- and how risky it is,
- and if it goes wrong,
- normally somebody gets fired.
- So there’s been in this current environment,
- what is actually less and less banking jobs,
- that are generally quite well paid,
- a lot of people are becoming
- a bit more risk averse,
- to actually push some of these innovations
- like blockchain in it as well.
- In many cases,
- we have seen some innovation teams
- take the lead.
- But again, the problem that has been there
- is that innovation teams are often great,
- but they are great for
- public relations perspective,
- for marketing purposes,
- to do some of the initial experimentation.
- But again, when you want to
- have it deployed at scale,
- you need to have the whole
- broader organisation involved,
- from IT to compliance,
- to the management, to finance,
- to bring these things forward
- from that perspective.
- But again, a lot of exciting things
- are going on when it comes to blockchain
- in financial institutions.
- Again, a lot of activity,
- a lot of developments are going on,
- and this is one of the most exciting times
- to be in finance.
- Not only because of
- blockchain and digital assets,
- but because of all of these changes
- we’re going through right now in the world.
- That’s all, my Fam folks.
- Thank you very much.
- It was a pleasure sharing with you all.
*Reference Videos What is Blockchain? [Introduction to FinTech Video 2.9A) by Professor Douglas Arner
- Cryptocurrencies, blockchain, ICOs.
- These are three terms
- that are in the headlines daily all over the world.
- Blockchain is the underlying technology
- which came to prominence with
- the launch of Bitcoin in 2009,
- but what is blockchain?
- Blockchain combines two long-standing
- technological developments.
- On one side, distributed ledger technology,
- and on the other, cryptography.
- If we look at Bitcoin, if we look at cryptocurrencies,
- cryptocurrencies at their base
- are blockchain systems combining
- distributed ledger systems and cryptography.
- Distributed ledger system,
- what is a distributed ledger system?
- For a system like Bitcoin,
- the distributed ledger
- means that the information in the system
- are not stored in one single place.
- Rather, they exist in multiple locations,
- multiple identical ledgers
- throughout the users of the system.
- So, if we think about this idea of ledgers,
- the traditional example is to think
- of something like a bank.
- A bank is a place where
- a certain amount of money is stored,
- it is a single place,
- it is a silo, it is a single ledger.
- At the other extreme, are distributed ledgers.
- Distributed ledgers mean that there is no single place
- where the information, the valuables,
- the data are stored,
- rather they are stored
- across a variety of identical locations.
- In between these structures of
- centralised and distributed,
- we also have network-based structures
- where perhaps you have a single centralised structure
- and a variety of spokes,
- a hub and spoke structure
- whereby the individual spokes connect to the hub.
- So, distributed ledger technology
- combined with cryptography.
- Cryptography is a technology that involves
- the secure storage,
- the encryption of information.
- It has a very long history with important points
- going back to code breaking,
- particularly in the Second World War.
- If we combine distributed ledger technology
- with cryptography, we have a system
- of secure distributed ledgers
- where entries have to be proven,
- proven through the use of a variety of structures
- which then encrypt the data into blocks.
- So, transactions 1 through 50,
- packaged in a block, encrypted together.
- The next set of transactions build on that first block,
- transactions 51 through 100
- encrypted as a second block.
- This structure provides
- a number of very important attributes
- to a blockchain-based system.
- In particular, it provides for security.
- The layers of cryptography across multiple blocks
- make it very hard, but importantly not impossible,
- to necessarily break those blocks
- making blockchain potentially a highly secure system.
- Second, it’s a permanent system.
- In other words, each of those transactions
- is recorded permanently in each of those blocks.
- That means that there is always a traceable history
- of all of the financial transactions
- going back to the very beginning.
- So, with each Bitcoin,
- you can trace back the life of that Bitcoin
- from it’s creation and into each account
- that it has been transferred to over time.
- And finally, transparency.
- Transparency means that the combination of visibility
- allows you to see what is happening in the blockchain.
- This combination of security, permanence,
- transparency, makes blockchain a potentially
- very powerful platform technology
- across a number of areas.
*Reference Video What is Blockchain? [Introduction to FinTech Videos 2.9B) by Professor Douglas Arner
- Cryptocurrencies, blockchain, ICOs.
- These are three terms
- that are in the headlines daily all over the world.
- Blockchain is the underlying technology
- which came to prominence with
- the launch of Bitcoin in 2009,
- but what is blockchain?
- Blockchain combines two long-standing
- technological developments.
- On one side, distributed ledger technology,
- and on the other, cryptography.
- If we look at Bitcoin, if we look at cryptocurrencies,
- cryptocurrencies at their base
- are blockchain systems combining
- distributed ledger systems and cryptography.
- Distributed ledger system,
- what is a distributed ledger system?
- For a system like Bitcoin,
- the distributed ledger
- means that the information in the system
- are not stored in one single place.
- Rather, they exist in multiple locations,
- multiple identical ledgers
- throughout the users of the system.
- So, if we think about this idea of ledgers,
- the traditional example is to think
- of something like a bank.
- A bank is a place where
- a certain amount of money is stored,
- it is a single place,
- it is a silo, it is a single ledger.
- At the other extreme, are distributed ledgers.
- Distributed ledgers mean that there is no single place
- where the information, the valuables,
- the data are stored,
- rather they are stored
- across a variety of identical locations.
- In between these structures of
- centralised and distributed,
- we also have network-based structures
- where perhaps you have a single centralised structure
- and a variety of spokes,
- a hub and spoke structure
- whereby the individual spokes connect to the hub.
- So, distributed ledger technology
- combined with cryptography.
- Cryptography is a technology that involves
- the secure storage,
- the encryption of information.
- It has a very long history with important points
- going back to code breaking,
- particularly in the Second World War.
- If we combine distributed ledger technology
- with cryptography, we have a system
- of secure distributed ledgers
- where entries have to be proven,
- proven through the use of a variety of structures
- which then encrypt the data into blocks.
- So, transactions 1 through 50,
- packaged in a block, encrypted together.
- The next set of transactions build on that first block,
- transactions 51 through 100
- encrypted as a second block.
- This structure provides
- a number of very important attributes
- to a blockchain-based system.
- In particular, it provides for security.
- The layers of cryptography across multiple blocks
- make it very hard, but importantly not impossible,
- to necessarily break those blocks
- making blockchain potentially a highly secure system.
- Second, it’s a permanent system.
- In other words, each of those transactions
- is recorded permanently in each of those blocks.
- That means that there is always a traceable history
- of all of the financial transactions
- going back to the very beginning.
- So, with each Bitcoin,
- you can trace back the life of that Bitcoin
- from it’s creation and into each account
- that it has been transferred to over time.
- And finally, transparency.
- Transparency means that the combination of visibility
- allows you to see what is happening in the blockchain.
- This combination of security, permanence,
- transparency, makes blockchain a potentially
- very powerful platform technology
- across a number of areas.
*Reference Video What is Blockchain? [Introduction to FinTech Videos 2.9B) by Professor Douglas Arner
- Now, if we look at blockchains,
- within this general structure
- we will often have a third level added.
- So, DLT plus cryptography plus smart contracts.
- What are smart contracts?
- Smart contracts are automated systems
- that on the occurrence of pre-determined actions
- something else happens.
- If I provide A, you provide B
- we pre-agree that A and B will be added together
- to create a new C,
- and this occurs on an automatic basis,
- this is a smart contract.
- There is an old joke that smart contracts
- are neither smart nor contracts,
- they are not smart because they are automated,
- they happen automatically,
- on the occurrence of something / events.
- And they are not necessarily contracts,
- but that is a more complicated legal question for later.
- Within this idea of blockchain,
- we can also add in a second important determination.
- Blockchains can either be
- permissionless, or permissioned.
- A permissionless blockchain, like bitcoin,
- means that it is open,
- anyone can participate that downloads the software.
- You download the software, you become a node,
- you’ll have a full picture of the ledger,
- that distributed ledger is distributed to your node,
- anyone can enter.
- But, we also have what are called
- permissioned blockchains.
- A permissioned blockchain,
- involves requirements or governance structures
- or restrictions on entry.
- In other words, only individuals or organisations
- or computers or devices which have been pre-approved
- can join into the network,
- can access the information
- and can potentially contribute transactions.
- Now, when we think about blockchain,
- it may or may not involve cryptocurrencies.
- A cryptocurrency will involve a blockchain,
- but a blockchain does not necessarily
- involve a cryptocurrency.
- In other words if we think of a blockchain based system
- at its base, it is a distributed ledger
- which is encrypted, maybe with an additional layer
- of smart contracts on top.
- Those individual data entries, can be anything.
- The communications between those data entries
- do not necessarily involve any sort of currency.
- One of the most interesting and powerful applications
- for this sort of thing,
- is in production processes,
- the food market where the providence of a chicken,
- or a bottle of whiskey
- can be proven by the blockchain system
- from its creation, its history, its movements
- documented throughout that system.
- So, any eventual possessor
- can document both the origin
- as well as the lifespan of that particular chicken,
- bottle of whiskey, diamond, artwork,
- whatever it may be.
- And that is the real power of blockchain.
- To build systems
- which are potentially highly secure,
- permanent and highly transparent.
- But, blockchain is not the solution
- for every problem, why?
- Because not every blockchain is created equally.
- not every blockchain is necessarily secure.
- Big blockchain systems like Ethereum or Hyperledger
- or R3’s quarter, or bitcoin,
- these are highly secure.
- But if I create a blockchain in my basement,
- probably not that secure.
- Just because it’s a blockchain, doesn’t mean it’s secure.
- Second, from the standpoint of
- permanence and transparency,
- this raises two problems.
- One, is the garbage in, garbage out problem
- in other words if you put that information in,
- it’s in there forever, and that is a big problem
- in the context of building histories,
- building information, the permanence problem.
- And finally, privacy concerns.
- If information goes into,
- a permissionless public blockchain,
- that information may be permanently
- on public display and access,
- and this can create all sorts of problems
- in that not necessarily do we want
- every piece of information permanently on view.
- So, looking at blockchain,
- and this is something that we talk about
- a great deal throughout this course,
- and in other courses.
- Blockchain is a very important technology,
- being used across all aspects
- of the financial sector and beyond.
- But it’s not the solution for every problem,
- but it is giving us an excuse to re-look,
- to reconsider many of our existing systems
- and infrastructure to build better systems.
- (upbeat music)
Module 1 Reference Reading
References and Suggestions for Further Reading in Module 1
(1) Differences between a distributed system and a decentralized system:
- What is the difference between decentralized and distributed systems? (Industry Article)
- Difference Between Centralized, Decentralized & Distributed Systems Oversimplified (Industry Article)
(2) Advantages and disadvantages of a centralized system and a decentralized system:
Module 2 Technological and Cryptographic Elements in Blockchain
Welcome to Module 2

Dear Learners,
Welcome to Module 2 Technological and Cryptographic Elements in Blockchain.
In Module 1, learners had an overview of the advantages and disadvantages of a decentralised system and a centralised trusted party in processing, and storing transaction data and you also had a glimpse of some issues to be resolved in a decentralised system.
In Module 2, you will see how blockchain technology works. Blockchains are designed to be immutable. You will see how the cryptographic elements including public-private key pairs, digital signatures and hash values are at work to achieve the special properties of blockchain. In addition to hearing from chief instructor Dr Siu Ming Yiu, you will also meet our guest speaker Prasanna Mathiannal (Co-Founder of MaGEHold) later in the module.
Happy learning and have a great week.
HKU Blockchain and FinTech Course Team
Module 2 Learning Objectives
After completing Module 2, learners should be able to:
- understand the basic usages of three cryptographic elements, public-private key pair, digital signature, and hash value;
- understand how the three cryptographic elements are used in blockchain to guarantee the properties of blockchain, such as immutability and privacy;
- understand basically how blockchain works such as how a new transaction can be appended, how to achieve consensus of miners, and why a miner would like to help.
Video 2.1.1 Cryptographic Elements: Public Key & Private Key
- Welcome to Module 2 of our Blockchain course.
- In the last module,
- we have discussed two issues.
- The first one is why we need to have a blockchain.
- In particular, we do not want to have
- a centralised authority to handle our transactions.
- And then, the second issue is about the technical issues
- for having a blockchain, namely, the security,
- integrity, and the privacy issues.
- Now, so in this module, we start to look deeper
- into the technical elements of a blockchain
- and how these elements work
- together to form the blockchain.
- The first elements I want to talk about are the public key,
- private key, and digital signature.
- In fact, they are mainly used
- for encryption and decryptions.
- The public key and private key,
- they always go in pairs.
- So basically, each user will have a pair
- of public key and private key.
- The public key can be open to the public,
- so everybody can know your public key.
- But on the other hand,
- for the private key,
- we need to keep it secret.
- If you know one’s public key,
- you are not able to deduce his private key.
- So in other words,
- even if you can see people’s public key,
- it’s very, very difficult to deduce what his private key is.
- In encryption, how are we going to use this public key
- and private key pair?
- For example, if Alex wants to send
- an email or a document to Bob,
- so Bob is the receiver and Alex is the sender.
- Alex wants to keep the email confidential,
- so one way they can do it is:
- Alex tries to encrypt the document
- before it’s sent over through the internet.
- Now, then we try to use
- public key / private key encryption.
- Alex will use Bob’s public key to encrypt the document.
- So in other words, we are using the recipient
- or the receiver’s public key to encrypt the document.
- And once the document is encrypted,
- even if the hacker over the network can get a hold
- of your encrypted version of the document,
- he has no idea what will be the content.
- When the receiver, Bob, gets the
- encrypted message from Alex,
- he use his private key, then he’s able to decrypt
- the message to see the real content of the documents.
- So this is how the public key and private key
- can be used together in order
- to keep things confidential.
- So we try to use the receiver’s public key to encrypt
- the document and when the receiver receives
- that encrypted version of the document,
- he will use his own private key
- to decrypt the message
- inside the encrypted documents.
- And the important property is
- if you do not have the right private key,
- it’s very, very difficult to decrypt the message.
2.1.2 Cryptographic Elements: Digital Signature
- Now, the second concept, also very important
- in blockchain is called digital signature.
- Now, a digital signature basically is very similar
- to the physical signature we want to do on a document.
- But, right now, we just put it in the digital world.
- So if you’re given a digital document,
- what you can do is you can create a digital signature
- on that particular document, using your own private key.
- So when you sign a document,
- you used your own private key,
- because private keys and public keys,
- they go in pairs,
- so the corresponding public key can be used
- by others to verify your signature,
- see whether this signature is from the owner
- of the private key.
- Now, if you change even one character or just one bit
- in a document, the signature won’t match.
- So in other words, if the document has been changed,
- I can just verify the signature,
- and then the signature will tell you that
- this is not correct, it’s invalid.
- Then you know that the document has been modified
- and the signature is not correct anymore.
- So this is the second cryptographic element
- that is important for the construction of the blockchain.
- But then I want tell you an efficiency problem
- for digital signature.
- So, basically, for any document,
- you can also create a digital signature
- using your own private key.
- But, the problem is if the document is long,
- the signature that we created will be also long.
- So in other words, the longer the document is,
- the longer time to create the signature,
- and also the longer the signature will be.
- So this becomes an efficiency problem.
- If you want to send a document
- together with the signature,
- over from one side of the internet to the other side,
- then it wastes quite a lot of bandwidth
- if the document is large
- because the signature will
- become much larger in this case.
- How do people solve this problem?
- So we also have another technique,
- which is called the hash value.
- So given any digital document,
- no matter how long the document is,
- we can always generate a fingerprint of fixed length.
- For example, some of the
- common hash value generation
- will produce a 160-bit of a fingerprint for a document,
- no matter how long the document is.
- And this fingerprint, we give it a name
- called hash value, and this hash value
- has a very similar property as a digital signature.
- So if people try to change one bit, or one letter,
- in the document, the hash won’t match.
- So in other words, if I give you the document,
- together with the hash value and, actually,
- you can check whether the
- document has been changed or not.
- If the document has been
- changed the hash won’t match.
- Another key point is this hash function
- is not something secret.
- So, in other words,
- everybody knows how to calculate this hash.
- Or you can get a hold of a function
- to calculate this hash value,
- so if I give you the same document,
- everybody is going to create the same hash,
- using the same function.
- Now, so you can see that this hash value can serve
- as a fingerprint for the integrity of the document.
- So let me give you a quick example,
- so if I want to tell people that
- this is my document, D,
- and I want to tell people that
- this document, D,
- has not been changed by others.
- So what I can do is,
- I can send you the document, D,
- and then I create a hash value of D,
- and then send you the hash value as well.
- And after I send you the hash value,
- because I do not want other people
- to change the hash value,
- so I can tell people that this hash value
- is produced by me, so I can actually
- sign on the hash value.
- This gives us a very fast and safe way
- to send documents, over the internet,
- so that people cannot change it.
2.1.3 Cryptographic Elements: Real-life Scenario Challenges
- Let me give you a real example.
- If Alex is going to send a contract to a company X
- over the internet, if you just send a message,
- plain text over from Alex to the company X,
- basically the hacker has the capability
- to modify any content of the message.
- For example, they can pretend that the contract
- is not from Alex.
- They can change the name of Alex to Devil.
- And then try to send this message over to the company
- together with the contract.
- Then company X may think that
- the contract is from Devil,
- but not from Alex.
- To make sure that this won’t be able to happen,
- we can actually use the technique,
- what we have just talk about.
- Let me ask you a few questions,
- see whether you know how to answer these questions.
- If you know the answer to this question
- it means that you really understand this concept.
- So the first method is:
- So Alex tries to send over the contract C.
- And together with a hash value of the contract C.
- So do you think this is safe?
- Now if you think about it, this is not safe.
- The main reason is, if you still remember what I talked
- about, the hash value can be produced by everybody.
- So in other words, if the attacker gets a hold
- of your contract C, and the hash value of C,
- he is able to change the contract C into C-prime,
- and at the same time,
- re-compute another hash value
- for the C-prime and try to send the C-prime
- and the hash value of the C-prime
- over to the company X.
- When the company X gets a hold of
- the tampered contract C-prime
- and the hash value of C-prime,
- he has no way to discover that the
- contract has been changed.
- Because the hash of the C-prime
- will match with the tampered contact C-prime.
- So this won’t work.
- So you cannot just send the contract C
- plus the hash value over because the attacker
- is able to modify the contract and the hash
- at the same time, so that the receiver may not realise
- that the contract has been changed.
- So we need one more technique.
- Alex, should try to send three things over
- to the company X.
- First, he needs to send the contract C,
- and then the hash value of C,
- and also he has to sign on the hash value of C.
- So basically it’s the contract, the hash value,
- and the signature of the hash value.
- Now in this way, if you think about it carefully,
- even if the attacker gets a hold of these three content,
- he might be able to change the contract C to C-prime,
- and also he might be able to change the hash value of C
- into hash C-prime, but the problem is,
- he is not the owner of the private key, of the signature,
- so he is not able to sign on the hash value correctly.
- So in this case, then he is not able to change everything
- so that the receiver will not notice it.
- The receiver can verify the hash value
- and the signature to check whether the document
- has been tampered or not.
- So this is basically the way we need to make sure
- that the document has not been tampered.
- Now, let me ask you another question,
- see whether you really know how to answer it.
- Now, then how about another student may give me
- another answer saying, then how about Alex will try
- to just send a contract C
- and also sign on the contract C,
- and send the signature of the contract
- and the contract over to the company X.
- So do you think this is safe enough?
- From the security point of view, yes, it’s safe.
- Because even if the attacker
- get a hold of these two contents,
- he might be able to change the contract C to C-prime,
- but he cannot sign on it,
- because he is not the owner of the private key.
- And the receiver once can verify the signature,
- can know that the signature is not valid
- for the contract C-prime.
- So in other words, from the security point of view,
- this operation is okay, is safe.
- But I hope you still remember, if you make a signature
- directly on a document, then the size of the signature
- will be as big as the document.
- So in other words, you are wasting bandwidth
- in order to send a long contract together
- with a long signature.
REMARKS from Chief Instructor Dr SM Yiu

2.2.1 Cryptographic Technology: Key Questions for Blockchain
- Let’s focus back to blockchain.
- Now, for an easy understanding,
- let’s put blockchain in the context of bitcoins.
- Let’s talk about what is a transaction.
- As a simple example,
- a transaction is something like this.
- A person, A, tries to pass X bitcoins to B.
- For example, Alex may want to transfer 10 coins to Bob.
- Or Bob can transfer, six coins to David.
- All these – each one of them will be called a transaction.
- Now think, what’s a transaction chain?
- So it’s also very easy to understand.
- So a transaction chain is a sequence of transactions
- and they are ordered by the creation time
- of the transaction.
- Now, so at the beginning, you can assume that
- Alex has 20 coins and Bob only has one coin.
- And right now, Alex starts to transfer 10 coins to Bob,
- so this basically is one transaction.
- And after the transaction,
- then you can see that Alex will have 10 coins
- after transferring 10 coins to Bob
- then Bob will have 11 coins.
- And later on, Bob can also transfer
- six coins to David, but then for the transaction
- to be executed, usually, we need an authorization.
- For example, in a bank, we’re trying to ask Alex
- to sign on a transfer slip,
- so that the bank knows that it’s authorised by Alex
- to transfer 10 coins from Alex to Bob.
- And similarly, if Bob wants to transfer six coins to David,
- Bob also needs to sign on a transfer slip
- before the bank will try to make the transfer for Bob.
- And why do we trust the bank?
- The reason is very simple.
- Because the bank has a very comprehensive procedure
- and this procedure will be covered by the law,
- so that’s why we trust the bank to make sure that
- all the transactions are valid and correct.
- Now, but I want to remind you, in reality,
- even if the bank has a comprehensive procedure
- for every transaction, but then, some of its rules,
- basically, it still relies on the staff to follow them.
- So if the staff is cheating, in fact,
- there’s no 100% guarantee for the safety
- or the security of the transactions.
- Now, but right now, we have blockchain,
- so we do not have a bank
- and we do not have a centralised entity to do it for us.
- Now one simple solution is we can just
- put the transaction chain on the internet,
- so everybody can get a copy and everybody can check.
- Okay, so this is one simple solution.
- So instead of keeping all the transactions in the bank,
- what we do is we put all the transactions,
- the transaction chain, into the internet.
- Now, in this case, we actually have the property
- of transparency, so anybody can do the audit
- for all the transactions.
- But the problem is if everybody can get a hold
- of all the transactions, the first question we need
- to worry about is,
- can anybody modify the transactions easily?
- The second question is, in reality,
- if you are using a bank,
- the bank is the one who maintains all the transactions,
- the ledger, the transaction book.
- But right now, the transaction chain is in the internet,
- so the problem is who is going to maintain the chain?
- And if you have new transactions,
- who is going to append
- or put the new transactions into this chain?
- So these two questions are what we are going to study
- and see how the cryptographic elements
- are going to help in this blockchain construction.
Video: 2.2.2 Who can Modify Transactions?
- Now, let me recall the cryptographic elements
- we just learned.
- For example, if we want to send a contract C from Alex
- to the company X, remember, what we have to do is
- we will send the contract C, the hash of the contract C,
- together with the signature on the hash value.
- And in this case, then the
- contract C will not be tampered.
- It cannot be changed by anyone easily,
- so we try to make use of this idea
- to construct our first blockchain.
- Now, in the diagram, you can see that transaction one
- is basically A, a person, A, tries to transfer $10
- or 10 coins to B, and he also creates a hash value,
- which is called h1, and he followed exactly
- what we have learned, so he tried to sign on this h1,
- so you can see the signature is signed by A.
- So A authorised the transaction, $10 transferred to B
- and he has created a hash and signed on the hash.
- And then, the second transaction
- is B is going to transfer $5 to C.
- And at the same time, B also followed the rules,
- so B has constructed a hash value, h2,
- for transaction two and as well as signed on
- the hash value h2.
- And then, you can see the signature, basically,
- is signed by B who also authorised
- the transfer of $5 from his own pocket to C.
- And you can see the last transaction is also from A.
- So the transaction three is A tried to transfer $5 to D
- and he also creates a hash value, h3,
- for transaction three
- and also signed on the hash value, h3.
- Now, assuming that all these transactions
- are on the internet right now, so I’m one of the users.
- I can actually get this transaction chain
- and verify whether every transaction is valid or not.
- And also, I can also check the signature
- because the signature can be checked by anybody
- using the corresponding public key of the person.
- So that’s why I can see transaction one,
- whether it’s valid or not,
- or transaction two and transaction three as well.
- So this is my first construction of a blockchain.
- But if you look at this carefully,
- then you can see that actually A can do something
- on the transaction even after it’s put on the internet.
- Now if you look at the diagram,
- let’s focus on transaction three.
- Right now, A changes his mind.
- “I do not want to transfer $5 to D.”
- So what he can do is he can
- get a hold of all the transactions,
- download a copy to his own computer.
- Then what he wants to do is change transaction three
- into only transferring $1 to D.
- Now, then what can we do?
- Recall that hash can make things difficult to change.
- So once you change one bit, the hash won’t match.
- But in our problem is the text, I mean, the transaction
- and also the signature basically
- are created by the same person.
- So that’s why the same person can also change the text,
- the signature, the hash together,
- using his own private key.
- Now, so, what we want to do is I want to make sure that
- the transaction, every transaction,
- cannot be changed by a single owner.
- Now this is actually what blockchain is doing.
- Now we have a modified version.
- Transaction one stays the same.
- So A tries to transfer $10 to B
- and transaction two, the same.
- B tries to transfer $5 to C.
- The main difference is, assuming transaction one
- is the first transaction of the whole chain,
- then we will say that this is D1.
- And if you look at transaction two,
- when B tries to create a hash of transaction two,
- in the original version, the hash is only created
- on transaction two, but right now,
- if you look at my modified version,
- the hash is basically created on transaction two
- together with D1.
- So we’ll try to use the whole transaction
- in the previous block
- and into the document before you create a hash.
- Then, if A wants to change a transaction,
- for example, he wants to change transaction D3,
- then transaction four will rely on transaction three,
- so that’s why he needs to change
- all the subsequent records
- in order to make sure that all
- the hash values will stay consistent.
- So you can see that these are the key issue, key points,
- that make the blockchain immutable.
- So only people use this term, immutability,
- to describe this property of the blockchain.
- It means that the record is
- permanent and tamper-proof.
- So once a transaction is put in the blockchain,
- it cannot be altered or deleted.
- It becomes a permanent record.
- Otherwise, if you want to change
- something in a transaction,
- you need to change all the
- subsequent transactions
- together in order not to be discovered.
- Now, it’s actually a very tedious work if you really want
- to change something because
- the chain may be very long.
- Then, you are going to do a lot of changes
- in the blockchain and I will talk about how to change,
- how to create, how to append a new transactions
- into the blockchain.
- Then, you will understand
- this is a huge amount of work.
- Basically, it’s not possible.
- So you can see that, in a bank,
- we try to guarantee the
- immutability based on procedures
- and the rules and hoping that the staff
- will try to follow the rules.
- Otherwise, they may go to jail.
- But still, there’s some staff may cheat,
- so it’s not 100% guarantee.
- But on the other hand, in this blockchain,
- we try to guarantee the property
- of immutability base on the technology.
- So we are using hash and signature to guarantee
- this property, so it’s not relying on human beings,
- assuming that they will follow the rule.
- So in some sense, you can say that it’s safer
- because the factor of human beings is eliminated.
- It’s guaranteed by the technology
- you use in the blockchain.
Video: 2.2.3 Who Will Maintain Transactions?
- Now, let’s proceed to the next question.
- Then who is going to maintain the chain
- and try to append new transactions?
- Then you know that in a bank,
- the bank is going to do it.
- We try to issue a new transaction
- and the bank tries to validate our transaction,
- if it’s okay, we put it in the transaction book
- but then in blockchain, everything is in the internet,
- there’s no centralised authority
- to handle the maintenance,
- handle the chain.
- So who is going to do it?
- In fact, it’s very simple.
- Everybody joining the scheme in the network
- is able to do it.
- Okay, now, how can we do it?
- So everybody can have the authority to keep a copy
- of the whole chain and when A has a new transaction,
- he broadcasts this transaction
- to everybody on the internet.
- So everybody will receive a message
- from A saying that, “I want to transfer my $10 to B.”
- So this transaction will be seen by everybody
- on the internet, if they are one of the users
- of the blockchain.
- And everybody is able to check it,
- and if it’s valid, then he can try
- to append this new transaction to the chain.
- And the first one, usually who completes this will try
- to broadcast the new chain to the internet.
- So if I want to add a new transaction to the chain,
- I send a message to everybody
- so the first one who helps me verify the transaction,
- will try to append a new transaction
- on his own chain, and broadcast the new chain
- to the internet, so somebody else would try
- to get the new chain and work on other transactions.
- The ones who help to check the transactions
- are usually called miners in blockchain.
- Everybody can be a miner depending
- on whether you want to be a miner or not.
- But you may have a question.
- That may be chaos, right?
- Because right now the internet may have many copies
- of the blockchain, the transaction chain.
- Now, assume at the beginning,
- every miner got the same chain,
- but after a while, we may have this situation.
- Miner A appends a new transaction, and broadcasts it,
- but due to the network congestion,
- maybe B and C didn’t get it.
- So only miner A has this new copy of the chain.
- Or miner E who is not an honest person,
- he’s an adversary, attacker,
- tries to append a fake transaction
- and broadcasts it.
- And D didn’t know it, right?
- So D would try to download E’s chain
- and try to work on E’s chain.
- And even worse, F can try to double spend
- because F can initiate two transactions
- even if his account may only have like $10,
- he can say that I want to transfer $10
- to Alex and another $10 to Bob.
- And then sends out two transactions at the same time
- and broadcasts it.
- And based on the understanding that in the internet,
- you can see there are some miners
- who may get the first transaction,
- and then some miners may get
- the second transactions.
- So in some sense, it seems like it
- becomes chaos, right?
- So if you imagine the situation is something like this,
- there are many copies of the chain on the internet.
- And maybe some of them are not the same.
- The first chain is the corrent transaction chain,
- and we assume that B right now,
- the account has only $10.
- And then, B is the attacker,
- then you can see that B tried
- to append a fake transaction
- into the transaction chain.
- B tried to transfer $15 to C and created a hash as well
- and signed on a hash value as well.
- But this is fake.
- This is incorrect.
- And another situation is,
- B actually issued another transaction as well,
- so B also wants to transfer $5 to D.
- But then you know some miners
- have been working on the first transaction
- transferring $15
- to C and another miner may work
- on the transaction transferring $5 to D.
- Then you can see that on the internet,
- we may have these three chains.
- And only one chain is correct.
- So in a very complicated situation,
- you can imagine that we have many, many chains.
- Some are correct, some are incorrect,
- some are the same, some are different.
- Then how we can resolve the problem?
- In fact, blockchain, the original idea,
- you use a very simple rule.
- Everybody when they discover that there is more
- than one chain,
- everybody will believe the longest chain.
- And you may ask then why, is based on what kind
- of principle, why only the valid transaction
- can be added in this case?
- And then why everybody eventually
- will keep the correct chain?
- Now, they have a very important assumption.
- They assume that the majority of the users are honest.
- Let me give you a concrete example
- then you will understand
- why we always follow the longest chain that is correct.
- Now assuming that the existing chain
- only has one transaction, transaction one there.
- A transfers $10 to B and we are going
- to have two transactions.
- One is correct, the other is not correct.
- So transaction two is correct,
- we try to transfer $5 to C,
- and transaction Tr2’ is not correct.
- B tries to transfer $15 to C
- and you can see that if the miners try
- to have to verify these two transactions,
- most of the miners will say
- that transaction Tr2 is correct
- and transaction Tr2’ is not correct.
- So in other words, most of the miners will try
- to append Tr2 onto Tr1 instead of Tr2’.
- Now if you assume that the majority
- of the miners are honest,
- so even if there are some attackers,
- the Tr1, Tr2’ chain will only be agreed
- by very few people.
- And most of the honest miners will try
- to continue adding transactions on the Tr1 to Tr2.
- And very few attackers will take care
- of the Tr1 to Tr2′.
- Then you can imagine the correct chain
- will get longer and longer if you give it enough time.
- Because everybody knows that Tr2 is correct.
- Tr2’ is not correct.
- So nobody is going to append new transactions
- on the T2’ chain.
- So this is basically why the principle works.
- Now, after resolving this issue,
- my next question is why do people want to help?
- Why do the miners want to help you?
- Why do the miners want to validate the transaction
- for you and then try to append the transaction
- into the new blockchain?
- The main reason is in the blockchain system,
- we have this incentive for the miners.
- So in return, if the miner is the one who validates
- the transaction and appends the
- new transaction successfully
- into the blockchain,
- he can create a new coin for himself.
- He can get a bitcoin after doing the mining.
- Because everybody wants to get this reward,
- so what they want to do
- is they want to make it fair to give all the miners more
- or less an equal chance to get the reward.
- So what they do is they will try to make the checking
- of the transaction more difficult.
- In fact, they have a concept called proof of work.
- So you need to need to spend effort in it
- in order to get the reward.
- You can imagine,
- that all the miners are trying to validate the transactions,
- because after you validate
- the transactions successfully,
- you get a new bitcoin.
- The system will try to ask miners
- to compute a difficult
- mathematical question using computers.
- So in order to append a new transaction
- on an existing chain, besides checking
- whether the transaction is valid or not,
- he needs to calculate an answer
- for a mathematical question.
- Now you can see that the transactions right now
- are verified independently by multiple miners
- and the decision is made by the majority of the miners.
- There’s no centralised decision-maker in the system.
- And in fact, the one I just talked about
- is one of the many trust models used in blockchain.
- There are some others, we will also talk about them
- in the later modules of the course.
- And usually this consensus,
- this trust model will come
- with a consensus algorithm so different platforms
- may use different trust models
- and also use different consensus algorithms
- to achieve the decisions.
- Now let me summarise it first.
- So roughly speaking, in a blockchain system,
- the security and the integrity will be guaranteed
- by using the cryptographic primitive,
- like the hash, signatures, trust model,
- the consensus algorithm, plus the incentive scheme.
Video 2.2.4 Cryptographic Technology: How to Protect Our Privacy?
- And we still have one last question: privacy.
- It seems like the privacy is even worse
- than we have in the bank, because, in reality,
- we have a bank,
- then the privacy issue is limited to the bank.
- The bank can look at your transaction,
- but the others are not able to look at it.
- But right now it seems like all the users in the internet
- can see all the transactions.
- So the privacy issue becomes a major problem.
- Now, so how can blockchain handle it?
- The answer is very simple.
- Because remember how many
- cryptographic primitives we have learned?
- We have used hash, signature.
- We haven’t used the public key and private key pair.
- So basically, blockchain will not ask you to use
- real names in the transactions.
- So we are going to use the public key
- and private key to do it.
- So for example, if A wants to transfer $10 to B,
- B in order to receive this $10,
- B will try to create a pair of public key and private key.
- And everybody’s public key will be used as his name.
- So we are not trying to put the transaction
- as “A transfers $10 to B”, and instead,
- this is what happens inside a blockchain:
- Public key, basically, is only a bunch of numbers.
- So we receive an address of a random number
- transferring $10 to another account.
- So basically we only have the account numbers
- shown in the transactions without a real name.
- And people are not able to map this account number
- to the real person, because the number will be
- generated by the user himself.
- So this resolves the problem of privacy.
Meet Guest Speaker Prasanna Mathiannal (Co-Founder of MaGEHold)

2.2.5 Public-key Cryptography (Prasanna Mathiannal from MaGEhold)
- Hello, everyone.
- Hi, I’m Pras.
- I’m the co-founder of MaGEHold,
- an angel investment firm
- in the blockchain space.
- A brief about myself,
- I’m a banker by the day,
- technologist by night,
- and a philosopher during the weekend,
- but enough about me.
- Let’s dive into the hot topic, blockchain.
- In cryptography,
- there are a few unique concepts
- and the one that is actually
- most relevant for blockchain
- is actually public key cryptography,
- which is a form of asymmetric cryptography.
- Now, what does that mean?
- Let’s say you have an account,
- which is actually, in blockchain terms,
- represented by a string of characters
- and you’re going to store a certain value,
- and let us take bitcoin as an example
- for easy illustration.
- Then, you of course know that bitcoin
- in current markets actually has some value.
- Therefore, you want to be careful about
- how you operate that account
- and make sure it stays under your control.
- So what gives you the control?
- That control is given to you
- by what is called a private key.
- So you can kind of imagine
- this whole account structure
- and the private key that gives you control
- and therefore, ownership of
- that account in the same way
- as you would see steel safes,
- but with digital kind of keys
- that you can key in to open it.
- Then, how exactly does this cryptography work?
- It is very simple.
- You have a password or a secret key,
- which you then undergo a process called hashing
- and hashing just converts it
- into a fixed length kind of output
- and there’s no other easy way
- to actually replicate it
- or kind of break it down backwards
- to find out what was the password you initially use.
- That’s what is called hashing.
- So as you might have guessed,
- in controlling your account access in a blockchain,
- especially public blockchains, like bitcoin,
- private key and public key
- is where hashing comes in.
- So public key technically is a conversion /
- a form of hash of the private key.
- Second, whenever you have accounts,
- you can automatically imagine transactions happen.
- So for signing transactions
- and proving that you initiated transaction
- as a source to a destination
- is another place in blockchain where
- hashing is used.
- Third, we talked about
- securing the network by people.
- This is where concepts called nodes,
- which are actors within the blockchain network
- that actually can validate your transactions,
- pack them up into a block and then,
- keep connecting them in a chain
- as one block after another.
- And in order to perform this action
- and possibly get rewarded or incentivised,
- you can actually use
- certain consensus mechanisms,
- like Proof-of-Work or Proof-of-Stake, etc.
- So now, most public blockchains,
- any data you store, either as logs
- and databases inside the blockchain,
- is open and free for all to read.
- So blockchain is secure,
- but the data you store,
- you have to watch out
- which blockchain you’re on
- and be sure that you’re not compromised.
Module 2 Reference Reading
References and Suggestions for Further Reading in Module 2
(1) The original blockchain design paper by Satoshi Nakamoto:
- Bitcoin: A Peer-to-Peer Electronic Cash System (Source: Satoshi Nakamoto [email protected] www.bitcoin.org)
(2) Industry articles about the features of blockchain:
- 6 Key Features of Blockchain : This is what makes Blockchain so exciting! (Source: The Fintech Way)
- Key Characteristics of the Blockchain (Source: Deloitte)
Module 3 Blockchain Platforms
Welcome to Module 3

Dear Learners,
Welcome to Module 3 – Blockchain Platforms. In the last Module, you saw how cryptography works in blockchain using public-private key pairs, digital signatures and hash values.
In Module 3, we will continue to look at the technical aspects of blockchain including the characteristics of three major blockchain platforms, Bitcoin, Ethereum and Hyperledger. We will explore and compare these platforms under five perspectives including platform design objectives, public vs. private block chain, whether there’s generation of cryptocurrencies on the platform, consensus algorithms, privacy and confidentiality.
In addition to hearing from chief instructor Dr. SM Yiu, later in the module, we will also have Charles d’Haussy (Director Strategic Initiatives ConsenSys) to share his expert opinions on consensus algorithm and trustlessness and immutability of blockchain technology.
Happy learning and have a great week.
HKU Blockchain and FinTech Course Team
Module 3 Learning Objectives
After completing Module 3, learners should be able to:
- classify blockchain platforms from five perspectives;
- compare three major blockchain platforms, namely Bitcoin, Ethereum and Hyperledger, in terms of five perspectives;
- understand more about tokenization and fund raising in blockchain projects.
3.1.1: Classification of Blockchain Platforms (Part 1) – An Overview of the 5 Key Perspectives
- In the last module, we talked about
- some cryptographic elements, like the digital signature,
- public key / private key,
- and also the hash function,
- that form the basis of a blockchain.
- And we also talked about how these elements
- work together to form a basic blockchain.
- Now, the original idea of blockchain
- is to support Bitcoin.
- But in fact, Bitcoin is not the only blockchain platform.
- There are many available
- blockchain platforms right now.
- For example,
- Hyperledger, Ethereum, Ripple, Corda, etc.
- In this module, we’re going to talk about the following.
- First, we will talk about
- the different classifications of these platforms.
- And then we will try to compare three major platforms,
- namely Bitcoin, Hyperledger and Ethereum.
- Now, let’s start with
- the classifications of the blockchain platforms.
- In fact, we can look at the blockchain platforms
- from five perspectives.
- The first one is whether the platform
- is designed for generic applications or not.
- And the second perspective is whether
- the blockchain is a public blockchain or not.
- And the third perspective is, we want to talk about
- what kind of consensus models or algorithms it uses.
- I hope you still remember we talked about
- the Proof-of-Work in Module 2.
- In fact this consensus model and
- algorithm has big impact
- on the performance of the blockchain platforms.
- In particular, depending on
- what kind of consensus model or algorithm you use,
- it affects the efficiencies.
- In other words, we worry about how many transactions
- can be handled in a second by the platform,
- or how many users can use the
- platform at the same time.
- And the fourth perspective is, we want to talk about
- whether the platform provides smart contracts or not.
- We’ll talk about what are smart contracts later.
- And finally, we want to know whether
- the platform comes with a cyber token.
- So we will try to look at
- these five perspectives in detail.
Video 3.1.2: Classification of Blockchain Platforms (Part 2) – Perspectives No. 1 and 2
- The first perspective is whether the blockchain platform
- is designed for generic applications or not.
- Sometimes the design of a platform
- may only be for some particular industry
- or the design of the platform may be generic.
- In other words, you can actually use the platform
- to develop applications in any industry.
- Now let me give you some examples.
- For example, Bitcoin actually is a very specific platform
- because Bitcoin is only for the transactions,
- the processing of the transactions
- of this particular cybercurrency only.
- So you cannot use Bitcoin to do anything else.
- Or you cannot create any
- applications in other domain areas.
- If you look at Corda, basically the design of Corda
- is specially for the financial industry.
- And there are many others,
- such as Openchain,
- is basically created for digital asset management.
- If the platform is specially designed
- for a particular industry,
- they will have specific features
- only fit for that industry.
- For example, in Corda, basically, they allow you
- to write programs that you can incorporate
- some of the legal expression,
- because the financial industry worries a lot
- about whether the transactions follow the law.
- So that’s why they have
- particular features to allow users
- to write programs that you
- can embed legal expression
- into the transactions.
- But on the other hand, for the generic platforms,
- then most likely
- they will not have these kinds of features,
- and then you can use it to design and implement
- any applications in any domains.
- So we’ll try to look at whether the platform
- is a generic one or is specially designed
- for a particular industry.
- Now, for the second perspective, we want to know
- whether the blockchain is designed
- for a public blockchain or not.
- Now, if you look at the original design,
- in Bitcoin, everyone can join Bitcoin
- without being verified their identity.
- In other words, I don’t care who you are.
- As long as you want to join, I will allow you
- to join the blockchain easily.
- They say that is permissionless,
- meaning that you don’t need to get permission
- in order to get into the blockchain.
- But however, think about it,
- if blockchain is used by some big enterprises,
- what they want to do is,
- they might want to create blockchain for their business.
- Now then they may have a concern.
- If everybody in the public can join the blockchain,
- then they worry that these members may be able
- to see a lot of information about the company,
- so they don’t want to have this kind of situation
- to happen in their blockchain.
- Now so, what they want is,
- they have other requirements
- if they want to use blockchain
- in their business.
- First, they probably want
- only the trusted parties
- with certain identities can join.
- Now this is very obvious, right?
- If the parties are not trusted,
- I do not want them
- to look at the information of my company.
- Or they even want to have a better control
- on the members to let them
- see what they want to see.
- And on the other hand,
- because they want the business
- to be smooth, so that’s why usually
- they have a requirement for high scalability,
- meaning that they want the
- platform to incorporate
- a large amount of users.
- At the same time, they want the transaction speed
- to be fast enough
- to cope with the business.
- So that’s why people come up with another type
- of blockchain platform, which is called a
- permissioned blockchain.
- Now in this type of permissioned blockchain,
- the entities can only join the blockchain
- if they can pass a verification process.
- And of course, if you look at it this way,
- it means that not everybody
- can join the blockchain freely
- without any verification,
- so you can treat this kind of blockchain
- as one which is not fully decentralized.
- Let me give you an example.
- For example, if my blockchain will allow a staff
- from the insurance company to join,
- so I need to have a verification process
- to make sure that you are
- one of the insurance company,
- you are one of the staff on the authorised list
- of companies before you can join a blockchain.
- This kind of verification will be done
- in this permissioned blockchain.
- Now, so that’s the second perspective
- on how we can classify a blockchain platform.
3.1.3: Classification of Blockchain Platforms (Part 3) – Perspective No. 3
- And the third perspective is we want to look
- at what kind of consensus models or
- what kind of algorithms the
- blockchain platform is using.
- In Proof of Work, they require the miners
- to compute very hard mathematical problems
- and they also introduce randomness into this problem.
- Even if the miner has more computational power,
- they may not be able to get the answer
- faster than the other miners.
- So that creates a fairness of the system.
- In other words, we do not want some of the miners
- who have lots of computational power
- to take control of the whole blockchain.
- And of course, if you still understand
- what I talked about Module 2,
- you can see in the Bitcoin platform system
- it actually allows fake transactions to exist.
- And then what we do is, we allow the transaction
- to be put in the blockchain and then we can have
- multiple blockchains; some with the real transactions
- but some with the fake transactions.
- But finally, we’ll try to take the majority
- to rule out the fake transactions.
- And in other words, we depend
- on the length of the chain.
- We try to believe the longest chain is the correct one.
- Because the basic principle behind is
- most to the participants are honest.
- So that’s why, if most of the participants,
- most of the miners are going
- to append the transactions
- in the longest chain,
- then we would believe
- that this chain is the correct
- chain for all the transactions.
- Now if you understand this
- principle, this Proof of Work,
- then probably you can
- see some issues behind.
- First, it takes time for the
- miners to do the calculation.
- In particular, to solve
- the mathematical problem.
- Then it affects the efficiency
- of the whole blockchain
- and also it’s a waste of
- resources, of computing resources
- in order to calculate
- meaningless math problems.
- Now the second issue is at any time slot,
- there can be different
- versions of blockchains
- existing in a system.
- At any time or point, we still have
- an issue to talk about when to confirm
- if a transaction is really settled.
- Now in the real Bitcoin system,
- what they do is
- they recommend the user to
- wait a certain amount of time,
- like, say 10 minutes or 20 minutes,
- until the transactions get
- stable in the longest blockchain.
- Then they will confirm that this
- transaction is really settled.
- Otherwise, we cannot
- guarantee the transaction
- would be put in the
- blockchain at that moment.
- So you can see, this waiting also takes time
- until the chain gets stable.
- So the whole thing will slow down the performance
- of the whole blockchain platform.
- So in other words, on the blockchain platforms,
- if you are using the Proof of Work as
- the consensus model or the algorithm,
- that means that the performance
- of the platform must not be fast enough.
- Now you can see that in many applications
- this kind of performance is not acceptable.
- So in the past few years, there were many, many
- consensus models and algorithms
- proposed by different people.
- In fact, people are trying to use another concept
- to work on this consensus algorithm,
- which is called the Proof of Stake.
- Now the basic idea behind is very simple.
- Because you can see in the blockchain,
- you know some people are holding
- tokens or the cyber coins.
- So we want to let the wealthy
- people to make the decisions.
- Now the rationale behind is very simple.
- If I’m the one who holds a lot of cyber coins
- in this blockchain platform, I do not want
- to do anything illegal, I do not want the
- fake transactions to be inputted
- in the blockchain platform.
- So that’s why these kinds of
- people will try to make sure
- that the transactions are correct before
- they are appended to the blockchain.
- Now more precisely, what they are doing is
- the one who holds more coins
- will have a higher chance
- to make the decision to append
- a new block into the blockchain.
- In this kind of Proof of Stake,
- they usually will introduce
- randomness into who will be the guy
- who makes the next decision.
- But then if you more coins
- then you have a higher chance
- to make the next decision to append
- a block into the blockchain.
- There are many variations
- on this Proof of Stake.
- For example, there is one variation that
- they want to look at how long you’ve held the coins.
- So in other words, in addition to seeing
- how many coins you are holding,
- they also want to know how long
- you’ve held those coins.
- They will combine these two factors together
- in order to make a choice,
- who is the next decision-maker
- for appending a new block into the blockchain?
- Now if you look at the existing blockchain platform,
- there are many others.
- For example, Ripple basically has
- its own consensus algorithm, which they call
- a Ripple Protocol Consensus Algorithm.
- And there are some other platforms,
- they try to use voting.
- In other words, they will let the miners to vote
- which transactions to be appended to the blockchain.
- But what the main reason behind is, if you pick
- a fast enough consensus algorithm,
- actually can increase the efficiency of the platform a lot.
- We want to make sure that this consensus model
- is fair, secure, but at the same time
- we want to increase the efficiency.
3.1.4: Classification of Blockchain Platforms (Part 4) – Perspectives No. 4 and 5
- The fourth perspective is related to smart contracts.
- If you look at the original design of blockchain,
- for example, if you still remember
- what I talked about in Module 2;
- we actually talked about the original design
- of blockchain for Bitcoin.
- Now in this kind of blockchain platform,
- it’s not programmable.
- In other words, people cannot write any programs,
- any additional applications
- on top of these blockchain platforms.
- The only purpose of the blockchain
- is to process the transactions
- of the bitcoins of the users.
- Now, but then in 2013,
- smart contracts started to be proposed in Ethereum.
- People usually mark this as Blockchain 2.0.
- So from 2.0 onwards,
- then we can actually use smart contracts
- to write programs and create new applications.
- Now, so you can see that smart contracts
- are very important
- in the development of blockchain platforms
- because they open up the opportunities
- for different developers
- or different companies to
- come up with new ideas,
- to create new applications in
- different disciplines.
- Now but then having smart contracts,
- of course is good for
- application development
- then we can have the chance
- to develop different types
- of applications for different disciplines.
- But actually, it also brings
- a lot of security problems
- into the blockchain platforms.
- And lastly, some of
- the blockchain platforms
- will come with a cyber currency,
- and some of the platforms,
- they may not have a cyber currency.
- Basically, most of the cyber currencies
- are created for money raising.
- In particular the ICO we talked about.
- Cyber currencies are also used as a token
- to be spent or paid on a transaction.
- Now in other words they have a platform,
- they create a new cyber currency.
- One of the main purposes is to
- attract you to stay in the platform.
- So you just get a hold of my
- token and then the token
- can only be spent on my platform,
- so that’s why you will stay in my platform
- and try to pay for the
- transactions in my platform.
- Having this kind of token,
- they hope that the price of
- the token will be increased
- so that the owner can make more money.
- So that the people will try to invest
- in your applications more
- based on this new token.
- You can see that this cyber currency
- is not a necessary element
- in the blockchain platform.
- So not all the platforms
- will have their own cyber currencies.
- For example Hyperledger and Corda,
- they do not have their
- own cyber currencies.
- And some of them may not
- even have the capability
- for you to create a new token.
- But on the other hand,
- it doesn’t mean in this platform,
- you cannot use any of the cyber currency
- in the applications.
- Actually, they can still
- use Bitcoin, Ethereum,
- to be embedded in their applications.
3.1.5: Highlights of Major Blockchain Platforms
- Now, what I’m going to do next is try to talk about
- the comparison between these three major platforms.
- The first one of course, Bitcoin,
- which is the original proposal
- for using blockchain technology.
- The second one I want to talk about
- will be Ethereum.
- We have an Ethereum enterprise alliance
- formed by more than
- 250 members, including
- Microsoft, JP Morgan, Intel, etc.
- And then, another major platform
- for blockchain is called Hyperledger.
- In fact, Hyperledger is formed
- by the Linux foundation,
- one of the open-source foundations,
- and the aim of Hyperledger is to design
- and develop enterprise blockchain.
- So in other words,
- they want to open up a framework,
- so that different enterprises can actually create
- their own versions of blockchain.
- So let’s try to compare these three
- major blockchain platforms right now.
- Recall that, we are going to evaluate
- and compare this platforms from five perspectives.
- The first one is whether this platform is generic or not.
- The second is whether the blockchain produced
- by this platform is a public blockchain,
- namely, the permissionless blockchain
- or if it is a permissioned blockchain.
- And third dimension, is we want to know
- what kind of consensus algorithm is being used
- in the blockchain platform.
- Next, then we’ll see whether it supports
- smart-contract programming or not.
- And finally, we want to see whether there is a cyber currency
- attached to the blockchain platform or not.
- Now, if you look at the first dimension,
- whether the platform is for
- generic applications or not,
- then everybody knows that
- Bitcoin is not generic
- because in the Bitcoin platform,
- it is only tailor-made for the processing
- of the Bitcoin transactions.
- But on the other hand, Ethereum and Hyperledger,
- they both can be considered as generic blockchains
- because they are designed
- for people who want to create
- new applications, new projects
- on the blockchain platform.
- If you look at whether
- the blockchain produced
- by the platform is a permissionless
- or permissioned blockchain,
- both Bitcoin and Ethereum
- are basically public
- because they can allow users
- to join the blockchain
- without any verifications.
- But on the other hand, if you
- look at the design principle
- for Hyperledger because you
- want to help the enterprises
- to create their own blockchain
- for their applications,
- so that’s why they
- put a criteria there,
- only the trusted parties that can go through
- a verification process can be allowed
- to join the blockchain, so
- that’s why we will consider
- Hyperledger is a permissioned blockchain.
- Now in that case, then you can see that Hyperledger,
- sometimes, people will consider that
- it’s not a fully decentralised blockchain.
- If you look at the consensus algorithms or models,
- then you can see that Bitcoin will,
- of course, use the original design, proof of work,
- and Ethereum, at the beginning, they also adopted
- the proof of work as the consensus algorithm
- for their system.
- But however, they find it, right now,
- the performance, that the efficiency is not good enough.
- So right now, what they are doing is they try to move
- from proof of work to proof of stake right now.
- Hyperledger, the design principle is that they hoped to have
- a framework so that different enterprises
- can create their own blockchain systems.
- So that’s why, in this particular area,
- in Hyperledger, it’s very flexible.
- You can pump your own consensus algorithms
- into the blockchain design.
- So basically, you can use proof of work, proof of stock,
- and also, even other consensus algorithms
- you can come up with that are applicable.
- If you’re looking at smart contract,
- now Bitcoin is not designed
- for people to write new applications.
- They only process the Bitcoin transactions.
- So that’s why, in Bitcoin,
- they will not support smart contracts.
- But on the other hand, both Ethereum and Hyperledger,
- they both support smart contracts.
- And finally, if you look at the last criterium,
- then, of course, Bitcoin has the cyber currency
- as Bitcoin attached to the platform
- and Ethereum also has its own
- cyber currency called Ether.
- But now, on the other hand,
- Hyperledger does not want to stick
- to any cyber currency or cyber tokens,
- so that’s why they don’t have any
- cyber currency attached to it.
- Before we end the module,
- I want to talk about a trilemma.
- Now, you know that, actually,
- what blockchain wants to do is
- to achieve three properties:
- the decentralisation, the security,
- or people usually mentioned it
- as consistency integrity issue,
- and finally, if you want to put
- it in real applications,
- we want it to be scalable, scalability.
- If you look at these three platforms,
- then obviously, none of the platforms can achieve all
- these three properties simultaneously at the same time.
- Of course, the security or the integrity must be satisfied
- by any blockchain platform,
- otherwise it’s not usable for any applications.
- This is the original design principle for blockchain,
- so that’s why we want to make sure
- that everyone there is consistent and secure.
- If you look at Bitcoin, Ethereum, Hyperledger,
- basically, all three can achieve this property.
- If you look at the decentralisation, as I mentioned,
- only Bitcoin and Ethereum are
- permissionless blockchains.
- So in other words, they are fully decentralised.
- But on the other hand, if you look at Hyperledger,
- they try to make a verification process there in order
- to check whether the party can
- join the blockchain or not,
- so it’s not fully decentralised.
- But then, on the other hand, if you look at Bitcoin
- and Ethereum, because they
- use this proof of work to do
- the consensus algorithm, so they slow down
- the efficiency of the platform.
- Hyperledger allows you to use
- all kinds of consensus algorithms.
- I hope you start to understand the trade-off between
- a permissionless blockchain and the efficiency.
- Now, if in a permissioned blockchain,
- the parties that can join the blockchain
- are actually trusted parties, so that’s why you can see,
- in the Hyperledger platform,
- we actually can achieve a more scalable platform
- than the Bitcoin and Ethereum.
3.2.1: What is Ethereum? (with Charles d’Haussy from ConsenSys)
- Ethereum is the second generation of blockchain.
- It really helps to programme and use smart contracts
- and gets much more complex
- in value adding propositions on a shared network.
- You might have interacted on the Ethereum
- through ERC20s
- which helps to raise money
- and support and fund different projects.
- Some of you may have played with CryptoKitties,
- for example. some other people
- are using Ethereum blockchain without knowing.
- Ethereum blockchain is used to take browser
- by the United Nations
- or the World Bank to help refugees.
- The Ethereum blockchain is used for
- creating digital identity
- for people which don’t have identity.
- The Ethereum blockchain is used in financial services
- to coordinate and
- disintermediate financial services as well.
- The Ethereum blockchain is used in the gaming industry
- to play and work with different digital assets
- which are created from the the digital games.
- The Ethereum blockchain is
- the second biggest blockchain in the world
- which brings together
- more than 300,000 developers today.
- Ethereum is a shared platform, totally trustless,
- with more than 10,000 different nodes.
- More than 300,000 developers in the world
- are developing open source software
- on the open source platform, that is Ethereum.
- Being open source, the Ethereum blockchain
- allows anyone to benefit from the progress
- of the world community.
- The recipe of software on the Ethereum blockchain
- is open source.
- You can bring on your own ideas,
- you can build on the ideas of someone else,
- in a very affordable way.
- The innovation on the Ethereum blockchain
- is not only coming from one country or one city,
- It’s distributed all over the world.
- Everyone benefits from the platform
- and it’s really the benefits of the open source software.
- The Ethereum blockchain builds the Web 3.0.
- It’s an innovation for everyone, from everywhere.
- It’s not only Silicon Valley innovation
- dominating the world,
- it’s everyone from Asia, Europe, US and Africa…
- building a joint platform, a common platform
- for innovation and entrepreneurs.
3.3.1: What is Ethereum’s Place in Today’s FinTech Ecosystem? (with Charles d’Haussy from ConsenSys)
- So what is Ethereum and what is Ethereum’s place
- in today’s blockchain and FinTech ecosystems?
- The history of blockchain started more or less in 2009
- with the Bitcoin blockchain,
- which was the first experimentation
- on distributed ledgers.
- As this blockchain, Bitcoin, still exists.
- It has demonstrated good value.
- It has demonstrated long lasting performance
- and securities and a lot of value has been created
- around this Bitcoin blockchain.
- But this blockchain is also so early and so old,
- its technologies can only deliver so much.
- So back in 2013-14, there were a lot of thought leaders
- and technologies which thought
- how they could improve
- and basically go to the next step
- building on the fundamentals
- and building on the idea behind the Bitcoin blockchain
- to build something which gets smarter in a way.
- And that’s where the Ethereum blockchain
- started to arise
- from different technologies working together,
- among them, Vitalik Buterin, as well as Joseph Lubin,
- the founder of ConsenSys later on,
- and they work with different groups of people
- to basically create a distributed computer.
- And they created the first concept of “smart contracts”,
- where really, you get this technology
- of coordination getting much smarter,
- not only registering transactions.
- You gave me something,
- I put something in my wallet,
- and the money is out of your wallet and in my wallet,
- but getting something which
- gets much more capacities,
- with having some kind of a virtual machine
- within the network
- where you can really start to get “smart money”.
- You can get “smart contracts”
- and you can start to have conditions
- on all the distributions
- and all the coordination works you want to do.
- So to speak, to Ethereum’s smart contracts,
- what are some useful Ethereum smart contracts
- and actually what is a smart contract?
- So a smart contract is basically a contract,
- so it’s something which will work with
- input and output.
- If you want to have an online voting system
- and you want this voting system to be decentralised,
- you will design a contract which will
- basically identify everyone around us,
- all the people involved in this vote,
- register their vote, and depending on the votes
- which have been recorded by the smart contract
- in a trustless manner,
- the smart contract will issue the results of this vote.
- You can also decide, for example,
- that the smart contract will be
- some kind of virtual entity
- existing only on the network in a trustless manner,
- or distributed manner.
- And if we agree that I’m going to work for you
- for a couple of days and you’re going to pay me
- a couple of hundred dollars for that,
- the smart contract will be basically doing the arbitration
- and making sure that I did the work,
- so I will document to the smart contract
- I was working for you and I delivered the job.
- And then, the smart contract
- will order the money from you
- and after you receive the proof that I was working,
- the contract will give me the money,
- for example, for some work.
- It’s a kind of an escrow system, which is distributed.
- But, from this escrow use case,
- you can go with much more complex
- kind of transactions
- and much more complex kind of works.
- So today, you see people building stock exchange,
- for example, on the blockchains.
- You see people building a full set of
- contractual relationships between companies
- and individuals on the blockchain also.
- And what it brings, it’s a very low cost
- and very inclusive technology,
- and very inclusive way
- to design interactions between people and companies
- and/or companies to companies.
- So what you will see in the coming years,
- and it’s already starting,
- it’s really like a lot of the non-digitalized
- kind of relationships we have
- and a lot of non-digitalized transactions we have,
- moving in a digital world
- and a lot of these interactions
- will happen on the blockchain because it brings
- a very low cost and trustless platform
- for all these people to interact together.
- So think of a working contract,
- think of maybe the proof of you owning your apartment
- or your piece of land, thinking of your identity.
- Instead of having the data kind of owned and managed
- by some big corporations,
- you will very soon be able to own
- all the data about your identity,
- your behaviours online,
- your different habits on the new internet,
- and being able to share them with the people you want
- and possibly, also monetize them.
- So the blockchain in the context of the internet,
- the blockchain technology and the Ethereum technology
- is bringing what we call the Web 3.0.
- So it’s really an evolution
- and a new layer of technology
- on our internet experience.
- So in the future, you will see in terms of blockchain
- will not come to you in a very complex manner.
- Most probably it’s a blockchain
- and we hope very soon will be totally invisible for you.
- And the same way you send email today,
- you don’t really realise that there is so many encryptions
- being done, there is so many different
- stack of technology being used.
- The Web 3.0 will bring you more value
- and will appear to you as fairly similar
- to what you’re doing today,
- but with a very new experience.
3.4.1: Trustlessness and Immutability of Blockchain Technology (with Charles d’Haussy from ConsenSys)
- What we mean trustless technology is that,
- if a rural bank away from Manila,
- is confirming that they gave to you,
- for example, a loan,
- or they give to you a bit of cash
- because you came to visit them,
- we can basically document that
- and this transaction is written in a trustless way
- on the ledgers, which at the end of the day or every hour
- can be basically rebalancing the ledgers.
- So every transaction is documented and immutable.
- So what do you mean by immutable?
- So immutable means when you build
- a blockchain infrastructure,
- you build a coordination platform
- between different parties.
- And if one of the players, one of the bank for example
- or one of the rural bank or one of the ATM, for example,
- is claiming that $100 was given to someone,
- so there is $100 less in this office,
- the data will be recorded one time and shared
- between all the different actors so everyone will know
- that there is for example, in your branch $100 less,
- and this cannot be changed anymore.
- So there is no way for anyone to fake the information.
- There is no way for anyone to play the system,
- because the system is distributed
- and the system is trustless.
- So we share the same infrastructure.
- If there is something happening in my branch,
- it’s recorded.
- If there is something happening in your branch,
- it’s also recorded and I cannot change the records.
- The records are immutable.
- So I know exactly what has been happening
- and I will trust what you will declare to me
- because I will be able to cross check that
- with the transactions from the blockchain.
- So it’s not only about building the trust,
- but it’s all about automating all the kind of book records
- and audits and declarations between different parties.
- All of this is automated on the blockchain
- and also reports come to you automatically.
- So are there any disadvantages to trustlessness,
- to immutability on the blockchain?
- There is no disadvantage to trustless in my opinion.
- I think this is a very strong value proposition.
- If we can work and collaborate at scale,
- between so many people and entities,
- it brings value, it brings access.
- Now when they are immutable, there is always
- a question mark, do you want to have always
- on the blockchain a record of every transaction?
- In this case, you will use encryption technologies
- where we will be able to document each other
- and trust each other about
- some transactions being made
- but without having all the transparency
- about these transactions.
- Maybe you don’t want the world to know
- that you’ve been taking $100 from your bank account.
- So there is encryptions capabilities nowadays
- in the blockchain solutions we deploy,
- to allow you to still record a transaction,
- so we know there is $100 less in your bank accounts,
- but the world blockchain does not know about that.
- This is where we are coming into the game
- what we call the different layers in the blockchain.
- So you might have a backbone
- which is the Ethereum blockchain
- and you build some applications on certain layers
- on the top of this base layer
- where you’re going to run transactions.
- And in case of any problem, you’re going to come back
- to the main net, is what we call the main net,
- the backbone of the blockchain
- to basically do the arbitration and realise,
- was there transactions happening?
- Yes or no?
- But all of these transactions can happen
- on what we call sidechain or layer two chains,
- where you don’t have to document to the world
- about everything in your life.
- So is everything on the main net public,
- publicly accessible?
- All the data is publicly accessible,
- but you can treat this data also.
- So you can possibly, for example, we can share
- on the main net a hash about one transaction.
- So we know the transaction is there,
- but only you and me
- we’ll be able to understand
- what is this transaction about.
- For the rest of the network, people will just see a series
- of encrypted numbers which are meaningless to them.
3.4.2: Proof of Work and Proof Stake (with Charles d’Haussy from ConsenSys)
- When we talk about the Ethereum blockchain,
- what is meant by it runs on a “proof of work” protocol?
- So that’s a very good question.
- So Ethereum blockchain was launched in 2015, right?
- And the way as a security of the network was designed
- was by using some miners, which were basically
- scanning all the transactions
- and bringing them in blocks after blocks,
- so this is why we call them a blockchain.
- And this activity of scanning
- and proving all of those different transactions
- and putting them into blocks is called mining today,
- and it’s called a proof of work.
- The Ethereum, what we call the Ethereum 2.0,
- is around the corner.
- This is being delivered right now.
- And there will be a transition from proof of work,
- where you’re gonna use machine
- and computers to look at all as the transactions
- and validate these transactions on the network.
- We got to move from machines doing it
- to purely software
- using a bonding system where people will be basically
- using software to validate and
- build validated transactions
- and build the blocks,
- and using a bond or so to make sure
- that these don’t validate the right transactions
- or start to play with the system.
- They might be losing their bond.
- So we are moving from a proof of work system
- to a proof of stake system, staking being a bond
- and you put a little bit of Ether as a poof,
- as a kind of a bond,
- to guarantee that you will do a proper job.
- So what happens when you don’t do a proper job?
- You lose your bond.
- So you’re incentivized to do a proper job.
- And there is also a system that the job is being made
- by different people at the same time
- and the people are checking the job of each other,
- so I cannot claim you’re not doing a good job alone.
- Different people need to basically, look at your work
- and say, okay, he has been
- basically faking the transactions
- and a certain number of people all agree
- that you are faking your transaction.
- So the system will basically grab your bond
- and you’re losing your bond.
- So who makes that distinction?
- Who says user X is making bad transactions?
- There will be thousands of miners
- and thousands of validator in the new system,
- so we will not call them miners anymore, but validators.
- And these thousands of validators
- have a system in place
- where they’re cross-checking each other
- and it’s purely mathematical
- and purely organized by the network itself.
- So everyone checks the work of everyone
- and when there is certain number of people flagging
- misbehaviors from someone, then there will be
- an automated system where the bond
- of this person will be just burned.
- So instead of using thousands of computers,
- you’re using thousands of validators
- which are much less impacting the environment.
- So yes, it’s beneficial.
3.5.1: Tokenizing (with Charles d’Haussy from ConsenSys)
- So tokenizing is one of the
- value propositions of blockchain.
- And today, many people are looking at this way
- to basically create digital shares
- of many illiquid assets.
- That’s what tokenization is.
- So if you think of a building,
- today if you want to buy a building, you buy a building.
- And you buy the full building.
- And this can be very costly, and the building is a building
- and there is one proof of ownership of this building.
- If you want to digitalize this building,
- how are you going to create shares?
- And how will these digital shares
- of the building be issued?
- And what is the most efficient way to do it?
- Some people are doing this for many, many years
- by creating a very expensive fund,
- using a lot of lawyers to create a fund,
- which he presents a building, and then selling shares
- of the fund which owns the building.
- And this process is actually very paper-intensive
- and extremely costly,
- and not really affordable for many people,
- and not easy to distribute after that.
- So this movement of tokenization is thinking
- all these illiquid assets which we are surrounded by,
- should it be a real estate,
- should it be company shares of non-listed companies.
- So before an IPO company shares exist.
- Maybe, your bakery is a company down the street,
- and you can be a shareholder of this bakery.
- Or you can be a shareholder of a project
- which will be happening for a few weeks
- and then fade out.
- So when you go through the process of tokenization,
- you create digital shares of something
- which is not liquid,
- or something which is not adding avenues to be exchanged.
3.5.2: What is a Token? (with Charles d’Haussy from ConsenSys)
- What is a token?
- So a token is a vehicle built on the blockchain
- to create values
- or to have some kind of specifications, right?
- So the first token you’ve seen
- on the Ethereum blockchain was the ERC-20.
- So the ERC-20 was able to hold values,
- to move value from one place to another,
- from one contract to another,
- from one user to another,
- and just bring the whole value in it.
- Since then, the technology keeps making progress,
- so you’ve seen many different type of ERCs.
- So you can think of many different kind of vehicle
- and wrap you can put on this Ethereum blockchain.
- So you have, nowadays, ERC-721, you’ve got ERC-1400,
- you’ve got ERC, you’ve got plenty of ERCs,
- which will all have very specific features
- towards very specific properties.
- So some ERCs, for example, as the 721,
- is a type of ERC which cannot be cut.
- So they exist in a very limited numbers of units
- and you cannot cut an ERC-2071.
- So if you think of an ERC-20, for example,
- they are called fungible.
- So fungible tokens means if I give you one token
- and you want to share half of it with someone,
- you can basically cut it in two and send 0.1 Ether,
- for example, to someone and send 0.3 to someone else.
- So they have the same, I will say, specificities as money.
- Some of the tokens will be called non-fungible tokens.
- So if I give you one non-fungible token,
- it’s one token only and this is the only one.
- And then, it creates many different properties
- and it brings many different use case for this one token.
- Some other tokens will have properties that they will be
- only exchangeable between accredited people.
- So for example, if I want to sell company shares,
- for example, you and me can exchange company shares
- because we are adults
- and because we qualify to buy and sell shares.
- But maybe these shares should not be
- in the hands of kids
- or should not be in the hands of people
- which are living in another country
- with other regulations.
- So we can start to really create some kind
- of programmable money and programmable vehicles.
- A token is a vehicle which moves in the blockchain
- between the smart contracts
- and lives in the blockchain.
- You can own it, you can share it, and all of these vehicle
- will have different specifications,
- and these specifications gives them different properties
- for different type of use.
- So the most popular is the ERC-20,
- but since the birth of the ERC-20,
- there is probably hundreds of different type of tokens,
- which comes with all different specifications.
- So think of a token of a car, like a car.
- Some cars are designed to transport families,
- some cars are designed to be extremely fast,
- some cars are designed to deliver mails and parcels.
- Some cars are designed to move food all around the city.
- So think of a blockchain of a big infrastructure
- and you need to have different tokens for different uses.
- And that’s what a token is.
3.5.3 [Industry Guest Speaker] Tokenizing Shares and Fund Raising (with Charles d’Haussy from ConsenSys)
- What do you think about the state of the ICO?
- Is the ICO dead or is it still a valid way
- to raise money for a blockchain project?
- So when the ERC-20 and the Ethereum was launched,
- many people realized that there were many ways
- to use this technology.
- And one use of this technology
- was raising funds for projects,
- what we call an ICO.
- So a project would at the time create a token
- which will be sold to investors
- to basically fund them and help them
- to start to bring people together
- and build the product.
- So this ICO phenomena has been very popular back
- in 2017 and 2018, and then now has kind of faded out
- because many of these projects
- have not always been delivering
- what they were promising.
- Some of them have been doing fantastic,
- some them have been doing poorly
- and I think the market has been kind of maturing.
- So you will probably not see as many ICOs as before.
- You will see them much more structured,
- maybe they will not be named ICOs,
- but the mechanism of funding projects
- using the blockchain will remain,
- but will come in different ways now using
- more complex types of tokens or complex types
- of relationships or mechanism of raising funds,
- which will give more guarantee to the investors
- and also more guarantees to the people raising money.
- But there is always a need to raise money,
- there is always a need to digitalize things around us.
- So the new mechanism are coming up.
- Maybe not they will not be called ICO anymore,
- maybe STOs there are many different ways to use
- and benefit from the technology to fund projects.
3.6 What is Hyperledger?
- Before we start, let’s talk about one important point
- about the differences between
- Ethereum and Hyperledger.
- Basically, Ethereum and Bitcoin are very similar.
- They are designed as a single platform,
- but on the other hand,
- Hyperledger basically is a family
- of multiple platforms developed for different types
- of applications for enterprises.
- In fact, these platforms are very flexible
- and they have different characteristics,
- they can fit into different types
- of applications for the enterprises.
- So therefore it is more flexible for the developer
- to develop appropriate applications
- using different platforms.
- The audience, if you are interested in Hyperledger,
- can try to learn more on the
- differences of these platforms,
- so that you can always pick the right platform
- to develop your own applications.
- Now let’s start to compare Hyperledger and Ethereum.
- Now basically all these five categories,
- or five perspectives, are interrelated.
- So we need to first look at their design objectives first.
- For Hyperledger, it’s mainly designed for enterprise,
- so mainly for B2B applications,
- but on the other hand,
- for Ethereum, they aim at B2C applications.
- Now in this case, then you can see that Ethereum
- will allow users to join the chain on their own.
- So therefore, Ethereum will provide a public chain
- for the applications.
- But on the other hand,
- because Hyperledger aims at enterprises applications,
- though they are supposed to
- be a permissioned blockchain
- so only registered or permitted users are allowed
- to join the chain, the blockchain.
- Now if you understand this,
- I hope you still remember the differences
- between a public chain and a permissioned chain.
- Now for public chain,
- we actually require some incentives
- for miners to work on the chain.
- So therefore,
- in Ethereum, we need to give
- the miners incentive rewards
- in order for the miners to work on it.
- But on the other hand,
- a permissioned chain of the Hyperledger
- is basically for the consortium.
- So basically they are willing to contribute
- to the blockchain and they are registered users.
- So in other words, we do not really need
- to give them incentives for the miners to work on it.
- Now this also explains why,
- if you look at the built-in cryptocurrency,
- then Ethereum has its own Ether.
- But on the other hand, actually,
- Hyperledger does not require such a cryptocurrency,
- for the reward of the miners.
- Now, if you look at it carefully
- and you understand everything I just talked about,
- then you can see that Ethereum will allow users
- to join the chain freely.
- But on the other hand,
- Hyperledger has more restrictions
- on who can join the chain.
- Basically all the users, alone users or registered users.
- So in other words, the behaviour
- of the users in Hyperledger
- are in a controlled manner.
- But on the other hand for Ethereum,
- because the platform may not know
- the real identity of the user,
- so the behaviour of the users
- is more difficult to control.
- Now this also explains why,
- when we look at the consensus algorithm,
- then Ethereum basically is using the proof of work
- in order to guarantee the security of the whole system
- and therefore you will take a longer time
- in order to process each transaction.
- But on the other hand for Hyperledger,
- then the user or the developer can have a choice,
- more flexible to choose an
- appropriate consensus algorithm
- for their applications.
- In other words,
- the consensus algorithm
- used by the Hyperledger,
- can run faster and require
- less resources, less storage
- and can be more flexible.
- And in fact Hyperledger
- even has an option for you
- to pick that you do not
- require a consensus algorithm
- to work on the chain.
- And so if you really understand this,
- then you can quickly imply
- that Hyperledger is more scalable.
- And if you look at the number
- of transactions per second,
- actually Hyperledger can go up
- to thousands while Ethereum,
- at most is like 15 to 20
- transactions per second.
- So you can see the differences.
- Basically it’s because of
- the consensus algorithm
- and also Hyperledger is under
- a controlled envoronment,
- but on the other hand, Ethereum is not.
- Then we come to the final perspective.
- How about privacy and confidentiality?
- For Ethereum, it’s similar to Bitcoin.
- For the identity,
- we basically use the public key
- as the address of the of your account.
- So, in other words, we
- are using the pseudonyms
- and therefore, the identity
- off the sender or the receiver
- may be hidden.
- But on the other hand, as
- we talked about before,
- the transaction may still be traceable.
- And in the basic design, of course,
- for the transaction content,
- everybody can see the actual content,
- so it’s publicly viewable.
- Now if you look at Hyperledger,
- for example, one of the platforms is called Fabric,
- the identity is basically
- anonymous and only the authority,
- when they do the registration,
- can reveal the real identity of the sender
- and the receiver.
- Otherwise, you know the identity is protected.
- And for the transaction content,
- in Hyperledger, they have better access control.
- so that transaction content can be encrypted.
- And the access control can be applied
- to allow some of the users to look at it,
- while the others may not be able
- to access the transaction details.
- Now this is actually one of the characteristics
- decided in Hyperledger.
- The main reason is that,
- they enable the company to do business
- with different partners.
- Even for the same product,
- they can have different discounts or different prices.
- So only some of the users can see these transactions,
- while the others may only see their own transactions.
- So let me summarise.
- One thing I talked about,
- Hyperledger is not for the public.
- It’s mainly for consortium.
- And Hyperledger has well controlled users
- and fly-granted access control for transactions.
- So therefore there’s no need
- to have a very secure consensus protocol
- and the trade-off is we can have a faster
- and lighter consensus algorithm.
- So that’s why Hyperledger can actually run faster
- and can be more scalable.
3.7.1 Hyperledger Blockchain Technologies (An Interview with Brian Behlendorf from The Linux Foundation)
- How about we start with, “What is Hyperledger?”
- To talk about Hyperledger,
- first I want to talk about the Linux Foundation
- and the Linux Foundation is a non-profit consortium
- of over a thousand different companies
- started about 17 years ago to help figure out
- how do we make open source projects sustainable.
- And how do you build
- a vibrant, healthy commercial
- technology ecosystem around things
- like the Linux operating system, initially.
- And the trick there was to figure out
- the right balancing act between organizing
- and supporting all of the open-source developers
- who want to contribute code to a common platform,
- but also, giving their employers
- and other companies in that space enough room
- and enough support to build commercial activities
- on top of the common code.
- So having both that developer hat and a company hat,
- and organizing the companies to help support
- kind of a small team of funded staff
- at the Linux Foundation
- to coordinate those efforts,
- kind of like an air traffic control tower.
- They figured out how to make that work
- for the Linux operating system.
- And then, it quickly became
- clear that you could apply
- that model to other technology domains,
- things that are immediately adjacent
- to the operating system, such as using Linux
- inside of telco hardware or inside of automobiles,
- things like security libraries, like OpenSSO,
- and then, two-cloud computing,
- like the Cloud Native Computing Foundation,
- which is the home for Kubernetes,
- and all of these additional projects the model was,
- companies that are members
- of the Linux Foundation also
- become members of these
- projects and contribute funds
- and help those kinds of projects take off.
- And so, in December 2015, the Hyperledger project
- was announced with 30 initial members.
- And some of those were the
- names that you would expect,
- like IBM and Intel.
- Others were unusual, like J.P. Morgan
- and a company called Digital Asset,
- who you’d not heard of in an
- open-source context before,
- but it was really a coming together of companies
- who realised there was something interesting about
- distributed ledgers, about blockchain technology,
- that was distinct from all the
- cryptocurrency applications,
- that really deserved a place
- to be able to be explored,
- to develop some underlying technology,
- explore those use cases,
- and figure out, can we grow these technologies
- to be production-ready and enterprise-ready?
- So I joined in June of 2016 as Executive Director.
- I used the term “nerd diplomat”
- to, kind of, better describe what I do.
- I am a Linux Foundation employee,
- as are 10 of my staff report, as well as four people
- based here in Hong Kong, actually.
- We do two different things.
- We help organize the open-source developers.
- We don’t write the code ourselves.
- We just try to make sure that there is enough process,
- enough structure, enough common elements,
- like the same open source licence
- is used across all the code,
- which is the Apache Licence, but really,
- helping them figure out how
- do they focus their efforts
- on what is a portfolio of technology projects.
- Some that you’ve heard, like Fabric, Hyperledger Fabric,
- which is very widely used,
- and some of them brand-new projects,
- like Hyperledger Transact or Besu,
- which I can talk about in a bit.
- But really, the idea is that there’s this conveyor belt
- that we put software projects on
- to get them to the point where
- enterprises can use them.
- And then, the second thing we do at Hyperledger
- is help encourage companies
- to build on top of this code
- and help them understand how to build
- support models around it or incorporate it
- into their products or services,
- or simply be more effective end users of the technology.
- And that’s really the main benefit we give to companies
- that pay money to support it,
- is helping them with marketing, doing events.
- But there are things we do that really will help
- even the broader ecosystem,
- even people who aren’t members of ours,
- so that’s kind of, in a nutshell, what Hyperledger does.
What Are the Differences Between Hyperledger and Other Blockchain Technologies? (Brian Behlendorf from The Linux Foundation)
- So, what do you think are
- the differences between Hyperledger
- and other platforms,
- other blockchain platforms?
- What the major difference is?
- So, we have a number of platforms, actually,
- within the Hyperledger greenhouse,
- as we call it.
- And we use the greenhouse metaphor to try
- to help people understand we have some technologies
- that are very mature, some technologies
- that are still starting out,
- but they share the same oxygen,
- the same airspace.
- They sometimes will cross pollinate each other.
- And so, to talk specifically about
- some of the frameworks that
- we have, Hyperledger Fabric
- was designed to be a high-performance
- distributed ledger system that is highly programmable.
- So you can use it for digital assets.
- You can use it for tracing of supply chain processes.
- You can use it for all sorts
- of complex business orchestration purposes.
- It was certainly built for enterprise use cases,
- which means it has a lot of power.
- It also has a lot of complexity to it at times,
- but it’s now running on every
- major cloud provider in the world.
- It offers Fabric as a service and lots
- and lots of companies are providing products
- that incorporate it and provide support for it.
- One of the differences between it
- and say, some of the public ledger technologies,
- one of those is performance.
- In the lab, it can do 3,000 transactions a second,
- kind of under ideal conditions, admittedly,
- but that’s a much better number
- than you’ll see in most others
- and there’s work underway
- to get that up to 20,000 transactions per second.
- There are lots of parameters that you can tune
- when different things are important to you,
- like supporting a larger
- network might be more important
- than a higher transaction rate,
- so you can adjust certain things about it.
- And really, it’s the standard now out there
- in the financial services space
- in supply chain traceability.
- Its deployment is pretty widespread at this point.
- Hyperledger Sawtooth was kind of our second project
- and it’s a little bit more of an experimental platform.
- It in some ways is more true to Nakamoto Consensus
- of kinda probabilistic finality.
- And it has some novel consensus mechanisms,
- like proof of elapsed time,
- and it has better abstraction layer between
- the smart contract layer
- and the ledger layer that has made it easier
- to bring in other smart contract languages,
- like Ethereum or Solidity or DAML,
- which is the Digital Assets Markup Language,
- and support those kind of on top of Sawtooth.
- And what we find actually is the nature of competition
- in an open-source space isn’t
- the same as Beta versus VHS.
- The nature of competition in open-source,
- especially when they’re under the same roof,
- like they are at Hyperledger,
- is people want to learn from each other.
- They wanna understand what have you built
- that is cooler than what I’ve got.
- And we can bring down a bit of the ego
- and certainly, bring down kind of the financial incentives
- for parties to split.
- And in fact, there’s one part of Sawtooth
- that has been broken out
- and is being put over to Fabric,
- which is that ability to run
- different smart contract systems.
The Rapid Growth of Blockchain in Meeting Industry Demand in Asia Pacific Region (Julian Gordon from The Linux Foundation)
- Hyperledger is the blockchain project
- of the Linux Foundation.
- We are open-source with over
- 270 companies around the world
- as our members and a thriving open-source community
- of developers working together
- on blockchain applications for business.
- So, we are very well placed to see
- and to nurture the rapid growth of blockchain
- in meeting industry demand in Asia Pacific
- and around the world.
- It is exciting times
- in the world of blockchain for business.
- Blockchain applications are evolving from pilots
- to real world platforms,
- and we see a lot of interest and development
- in Asia Pacific markets,
- from Australia to India, Japan,
- Singapore, Thailand, all across the region
- and most especially I would say in China.
- Projects are going into production in many industries
- and bringing benefits including
- substantial cost reductions,
- dramatic increases in efficiency, transparency,
- and security, and the development
- of new business models and opportunities.
- At Hyperledger, we host a greenhouse
- for blockchain projects.
- We provide expertise, infrastructure,
- and support so that developers and companies
- can collaborate in an open-source environment
- on blockchain technologies for business.
- Our projects have
- a broad collaborative software community around them.
- Everyone is welcome to participate.
- Some are in incubation,
- and others are active being used in hundreds of POCs
- and implementations globally.
- Six of the projects are distributed ledgers.
- They are in different stages of development.
- Hyperledger Fabric, Hyperledger Sawtooth,
- Hyperledger Row and Indy,
- which is for self-sovereign identity,
- are already active being used
- in live business applications globally today.
- Hyperledger Besu is an Ethereum client
- that runs on both private networks
- and the Ethereum public network.
- We have four software libraries
- including Hyperledger Quilt
- for blockchain interoperability and Ursa,
- which is a cryptography library.
- We have tools such as Hyperledger Calliper,
- which is a benchmarking tool for blockchains.
- We have also domain specific projects
- such as Hyperledger Grid,
- which is for supply chain applications.
- So, what are the main industries
- where we see blockchain having a real business impact
- in Asia Pacific?
- Hyperledger technologies are being developed
- for business solutions across virtually all industries,
- including energy, manufacturing, telecom, education,
- transport, and in the public sector.
- But in Asia Pacific and globally,
- we see the most activity
- in financial services, supply chain, and healthcare.
- In these industries, we already
- see Hyperledger platforms
- being used in live real world solutions.
- In financial services, in areas such as capital markets,
- equity trading, mortgage underwriting,
- KYC, and anti-money laundering, corporate banking,
- insurance, and particularly in trade finance.
- For supply chain, we have areas
- such as provenance tracking,
- cutting bureaucracy at ports and customs,
- IoT devices to detect poor shipping conditions
- and title tracking for high value goods.
- For healthcare, we have areas
- including provider directories
- and certification, patient-driven healthcare records,
- insurance claims processes,
- and the whole pharmaceutical supply chain.
Module 3 Reference Reading
References and Suggestions for Further Reading in Module 3
NOTE: We may come across information about comparisons of different blockchain platforms (note that those may not be based on the same 5 perspectives discussed in Module 3. Quite often we’ll consider the comparisons from the domain of applications.
(1) Academic paper for reference
- Blockchain platforms: A compendium (Chinmay Saraf et al.)
- A comprehensive reference model for blockchain-based distributed ledger technology (Andreas Ellervee et al.)
- Taxonomy development of blockchain platforms: Information systems perspectives (Shehu M. Sarkintudu et al.)
- Comparison of blockchain platforms: a systematic review and healthcare examples (Tsung-Ting Kuo et al.)
- BLOCKBENCH: A framework for analyzing private blockchains (Tien Tuan Anh Dinh et al.)
(2) Information of some popular blockchain platforms
- Ethereum platform: https://www.ethereum.org
- Hyperledger platform: https://www.hyperledger.org
- Bitcoin: https://bitcoin.org/en/
- Corda: https://www.corda.net
- Ripple: https://www.ripple.com
(3) Industry articles and information on: tokenization, fund raising, and differences of ICO and STO
Will Asset Tokenization Revolutionize Fundraising and IPOs?
The Difference Between ICO and STO
Module 4 Blockchain Applications
Welcome to Module 4

Dear Learners,
Welcome to Module 4 – Blockchain Applications. In the last Module, we looked at the characteristics of three major blockchain platforms, Bitcoin, Ethereum and Hyperledger.
In Module 4, you will first be introduced to key selection criteria for blockchain applications by chief instructor Dr. SM Yiu. Then you will hear from our guest speakers, Dr. Paul Sin (Consulting Partner from Deloitte, China) and Anil Kudalkar (MD, MaGESpire Partners) who will share with us some real world use cases in enterprise blockchain including: trade finance, supply chain financing, cross-border connectivity, capital markets and government services.
Furthermore, our guest speaker Charles d’Haussy (Director Strategic Initiatives ConsenSys) will talk about how to deploy an application on Ethereum and some interesting use cases of ConsenSys on Ethereum.
Happy learning.
HKU Blockchain and FinTech Course Team
Module 4 Learning Objectives
After completing Module 4, learners should be able to:
- understand the selection criteria for using blockchain for an application;
- list some use cases in real applications that use blockchain and why these use cases are good fits for the blockchain platform.
4.1.1 Selection Criteria for Blockchain Applications (Part 1) Key Factors 1, 2, 3
- Welcome to Module 4 of our Blockchain course.
- Now in this module,
- what we are going to do is,
- we want to look at Blockchain
- from the application point of view.
- So we want to look at what applications
- can make the model of Blockchain better.
- Okay, let’s review:
- what are the characteristics of Blockchain?
- Basically, Blockchain is a ledger.
- A ledger means that it’s a database of transactions.
- So it’s trying to store the transactions into the database.
- And the second characteristic
- is decentralised properties.
- In other words we do not have a centralised
- trust authority for the whole system.
- And the third characteristic is immutable,
- meaning if you put a transaction in the Blockchain,
- you can never change or even delete it.
- And of course it’s transparent,
- so that all the users can see the transactions.
- Now all these are the good points of Blockchain
- but Blockchain does have some limitations,
- we also talked about in earlier sections.
- For example, the scalability and
- also the complicated trust or
- decision-making model
- based on some kind of assumptions.
- So these are the characteristics
- of a Blockchain system.
- And on the other hand,
- I also want to review with you
- the limitation of having a centralised ledger,
- meaning that we do have a trusted authority
- to handle the system.
- And we do have at least three disadvantages.
- First of all, it might incur high transaction fee,
- and the privacy issue because the trust authority
- is able to look at all the transactions of yours
- and of course the last one is the processing time.
- When we talk about transaction processing time,
- we refer to the case that maybe we need to involve
- multiple parties in the transaction.
- For example,
- if you want to transfer money from one bank
- to another bank overseas,
- then you might involve
- at least two banks or sometimes intermediary parties.
- Or for similar tasks,
- for example, if you want to open
- a bank account in different banks,
- or try to locate a product from multiple suppliers,
- then we need to repeat the same procedures for
- multiple times so it incurs a long processing time for it.
- Now, we understand the advantages and disadvantages
- of a decentralized and centralized ledger.
- Then based on these pros and cons,
- we want to make a good decision,
- to see whether the application is good
- for Blockchain platforms.
- Now I hope you still remember the first characteristic of Blockchain:
- Blockchain basically is a ledger.
- Now, so the first question you should ask yourself is,
- does your application require the system to
- store, retrieve, or process transactions?
- In other words,
- does your application require a database?
- Now if the answer is no, it means that you don’t actually
- need to store a database, then in this case, usually,
- we will not go for Blockchain.
- Okay, let me give you some examples,
- then you will understand what I’m talking about.
- For example, a bank may want to provide a service
- to help the customer to calculate the interest
- for a mortgage loan.
- This service usually is anonymous, right?
- Because they do not want to
- remember or store any details
- of the input given by their customers
- and usually, their service is free.
- Then, in that case, we do not need to store anything,
- and the service just wants to calculate the interest
- for a particular mortgage loan.
- Then in that case,
- we usually will not use Blockchain.
- There are many, many similar examples.
- For example, the audit department may want to provide
- free services for people to calculate the tax,
- or you can provide a website to help students
- or professionals to calculate the answer
- for some math problems, etc.
- All these cases you are not going to
- store all the transactions.
- You just provide a service for calculations.
- Then, in that case, we will not go for Blockchain.
- So, first of all, you need to ask yourself
- whether you need a database in the application.
- Okay, the second one, also, we refer to
- a characteristic of Blockchain.
- You should ask yourself, do you have
- a trusted centralized authority?
- In other words, in the whole application,
- do you have a party that you trust,
- and he can actually control the system for you?
- Now, if your answer is yes, then again,
- you don’t need to use Blockchain.
- Let me give you a common example.
- I think we all trust the immigration department
- or the government, to maintain our traveling records
- for going in and out of the country.
- And also, they actually have
- the authority to know about it
- and in this case, you can see that the privacy issue
- is not a major concern,
- and in fact, we will believe that the authority
- will handle it properly.
- So in that case, we do have a trusted authority
- that can handle our records.
- Then, in that case, we do not need to use Blockchain.
- There are many other examples, for example,
- if we are talking about the
- ownership information of properties,
- the purchase records of the apartments,
- we always trust the government,
- and all this information
- will be stored in the government database.
- In that case, we do have a trust authority
- to handle the information.
- In other words,
- there’s no need for us to go for Blockchain.
- Now the third question you should ask yourself
- is about the transaction fees.
- Now even though you might have a trusted authority,
- for example the bank, who can handle
- the transaction for you, but if the transaction fee
- is too high, then you need to think about whether
- you should go for Blockchain platform or not.
- Okay, let me give you some examples.
- If you want to transfer the money between banks
- or you try to trade data, buy and sell data,
- or you try to rent the apartment,
- you will see that the agent in between
- may charge you a high transactions fee.
- Then, in that case, you may think about whether
- we can go for Blockchain platform
- in order to eliminate the centralized authority
- to handle all these transactions
- so that you can enjoy a lower transaction fee.
- Now of course, usually the trust authority
- will try to provide additional services
- or add on services to you in this kind of services.
- So you need to evaluate whether this service is worth
- the high transaction fees, or will this service
- be so critical that a Blockchain platform
- may not be able to provide a similar service to you.
4.1.2 Selection Criteria for Blockchain Applications (Part 2) Key Factors 4, 5, 6
- Question number four,
- you also need to consider
- whether your application
- will involve multiple parties.
- When I say multiple parties
- I mean that the number
- of parties is at least three.
- Now, if the number of parties involved in the application
- is less than three, then in that case,
- we also do not recommend you to use blockchain.
- Now, a major characteristic of blockchain
- is this decentralised trust model.
- In other words, we try to let the entities
- who participate in the blockchain to make the decision.
- But if the application only involves two companies
- or even one company,
- then if you try to use blockchain,
- then you need to go for
- a more complicated trust model.
- Then, I think this is not necessary.
- Okay, now let me give you another example.
- Now, if two companies, they decide to join forces
- to market a product, it’s easy for them to compromise
- how to store the transaction,
- how to handle all the transaction process
- for the transaction.
- Then, in that case, I don’t think we need to go
- for the complicated trust model in the blockchain,
- but I want to make a remark here.
- When I say company,
- I just used this term to refer to an entity.
- Sometimes, even in one company,
- they might try to put some
- of the applications into blockchain.
- If the company actually involves many departments
- and the departments, they don’t trust each other
- or they do not want others to looks at their data easily,
- then in that case,
- we still consider this case a multiple-entity case.
- Then, sometimes, we still try to
- use blockchain to implement
- some of the application in just one company.
- For example, if a company has different branches,
- one in Hong Kong, one in UK, one in US,
- maybe they want to combine
- their data to do something,
- then, in that case,
- they might not want others
- to look at their data,
- but they want to compile their data
- to do some, for example, marketing purpose.
- Then, in that case, they may try to put the application
- on the blockchain.
- And then, the next question
- you should ask yourself is,
- does your application involve
- high frequency of transactions?
- Now, if your answer is yes,
- then again,
- we do not recommend you to use blockchain.
- The main reason is,
- if you still remember our earlier sections,
- we talk about the transaction rate of blockchain.
- Now, the slowest blockchain transaction rate is like this.
- They can only handle seven or
- eight transactions per second.
- Now, for comparison, if you look at Visa,
- basically, they can handle
- 2,000 transaction per seconds.
- Now, then, in this case, if you try to put an application
- with a very high frequency
- of transactions into blockchain,
- basically, blockchain cannot handle this kind of volume.
- Then, it would be a disaster.
- If you look at the internet,
- people start to talk about new design of blockchain
- and some of the blockchain platforms
- that they claim that
- they are able to handle 1,000
- to 2,000 transactions per second.
- Now, that may be the case,
- but we do need more evaluation
- in order to confirm whether
- the performance is that good.
- In other words, at this moment, I still think that
- if your applications involve
- high frequency of transactions,
- maybe you need to think twice
- before you go for the blockchain platform.
- So, another example is if you’re talking about
- high frequency trading in stock market.
- Basically, they are talking about almost a million
- transactions per second, then definitely,
- you are not able to use blockchain platform
- to handle this kind of transaction volume.
- The last question you need to ask yourself
- before you really go for blockchain,
- you need to think about whether you have
- enough entities to maintain the blockchain.
- In particular, one type of blockchain
- is called permissionless.
- Basically, it’s a public blockchain,
- so everybody can join the blockchain.
- In this kind of blockchain, the trust scheme,
- for example, if you’re talking about proof of work,
- actually requires quite a number of entities
- to help to maintain the fairness of the decisions.
- Otherwise, someone maybe able to cheat.
- I give you a very simple example;
- if your blockchain has a voting system to vote on,
- which chain we wouldn’t want to follow.
- Now, if your chain only has 10 entities,
- if six of them actually collude together
- and then, they are able to, so in that case,
- if you are not sure whether you
- have enough users or entities
- to maintain the blockchain,
- then you also need to think carefully
- before you actually move
- to the blockchain platform.
Selection Criteria for Blockchain Applications (Part 3) Best Fit Applications
- Now, on the other hand,
- there are other characteristics
- of the applications that fit very well
- in a blockchain platform.
- Now, let me try to illustrate some of them.
- Now, the first one is
- if the application will emphasize
- on the chain of custody alone.
- For example, I worry about
- the origin of the medicine,
- the food, or the wine, etc.,
- then you know that
- one of the big characteristics
- of blockchain is once you
- certify or verify something
- and then, you put it in the blockchain
- then, people cannot modify or change it,
- so that integrity can be maintained.
- So basically, what they are doing right now
- is they will try to keep this chain of custody
- in the blockchain platform,
- so whenever the customer tries to buy a product,
- they may just use the QR code.
- Then, they can retrieve the whole chain of custody
- of the product and then, they see
- where the medicines come from
- or the food comes from.
- So this is one of the good characteristics
- of the applications that will try
- to use blockchain as one of the platforms.
- The second characteristic is if the application
- actually involves tedious procedures.
- For example, they might involve repeated renovation.
- For example, if you need to do job hunting,
- then you know that the company usually asks
- for your graduation certificate
- or if you go for further study, they will again ask
- for your certified graduate certificates.
- And then, right now, what people are doing
- is they will try to apply to the university
- and pay the money and then, wait for the university
- to send a certified copy to the companies
- or to the universities
- in order to verify your qualifications.
- Or, for example, if you’re trying to open a bank account,
- then you need to show your identity proof,
- address proof, in order to open a bank account.
- If you go to another bank,
- you have to repeat the same procedures.
- Usually, it always takes time.
- Now, think about it.
- If we try to put all these in the blockchain,
- for example, if the universities basically
- will try to certify your certificate
- and the certified certificate is already
- put on the blockchain system
- and then, what you need to do is
- you just need to inform the university
- that you’re going to apply for this job
- or apply to another university.
- And the company can actually
- get the certificate information
- directly from the blockchain without any delay
- as long as you pay for it of course.
- And the payment actually can also
- be done in the blockchain as well,
- based on the smart contract procedure
- we talked about in earlier sections.
- So in this case, this kind of application,
- if they involve tedious procedures, repeated validation,
- is also very good for blockchain platforms.
- My final example is about the applications that involve
- multiple suppliers and multiple buyers,
- kind of like many-to-many relationship.
- For example, if you’re looking for a product
- from multiple suppliers or the love matching example
- I used in an earlier section,
- so if we do not have blockchain,
- so what we need to do is
- we need to register yourself
- to every company separately
- and then, pay the membership fees separately.
- And then, you need to look at all the results
- from the individual companies.
- Then, it is basically a waste of time
- and you need to look for these kind of suppliers yourself.
- Now, on the other hand,
- if we can create a common marketplace
- or a better data trading place using blockchain platform,
- then what we need to do is
- we just can issue one request
- for a particular product
- and the suppliers in the
- blockchain platform can basically
- provide you all the information you require,
- and then, you just pay for what you want.
- So this is basically the three particular characteristics
- of an application that fits very well
- into the blockchain systems.
- Now, finally, there is another key issue.
- Now, if the application involves multiple parties
- to join to participate in the blockchain system,
- now you need to make sure that almost all the entities
- will join the blockchain system.
- Otherwise, for example, in a supply chain management
- or in a mortgage loan evaluation,
- if some party, they do not join the blockchain,
- then this party will become
- the bottleneck of the procedure.
- Or basically, they will break the chain of custody.
- In other words, you cannot retrieve everything instantly
- from the blockchain
- and then, it will delay the whole procedure.
Selection Criteria for Blockchain Applications (Part 4) Decision Making
- What I’m talking about today
- is kind of like a guideline for you to consider
- whether an application should go for blockchain or not.
- Now, before I end my section.
- Now let me go through this flowchart.
- After doing this flowchart you should be able
- to give some indication
- whether you need to consider blockchain
- as the platform for your application or not.
- The first question is whether you need a database
- in the application?
- Now if you don’t need a database,
- basically, we do not need a blockchain.
- Now, if your answer is yes,
- then your next question is,
- do you have a trusted authority in the application?
- For example, will the government handle the data
- that you trust the government?
- Now if yes, then you still need to ask another question,
- whether the transaction fee is too high.
- Now, if the transaction fee is not high,
- it’s acceptable to you and
- you do have a trusted authority
- to maintain the database
- and to handle the transaction for you,
- then again, don’t go for blockchain.
- Now, then, on the other hand,
- if you do not have a trusted party,
- trusted authority, or even if you have a trusted authority
- like the bank but the transaction fee is too high,
- then you may still consider using blockchain
- for your application.
- Then the next question you should ask yourself
- is whether the application
- involves more than two entities.
- If the answer is no
- because there are only two entities
- then in the application
- you can actually compromise everything easily.
- Then, in that case, we do not use blockchain.
- But if your answer is yes,
- in other words, we need a database,
- we do not have a trusted authority or
- the transaction fee is too high,
- and the application actually involves more
- than two entities.
- Then you need to ask another question,
- will all the entities join the blockchain platform?
- You need to have an understanding
- whether these parties are willing to work together
- in the blockchain platform.
- If your answer is no, I’m not sure maybe only a few
- of the entities will join the blockchain platform.
- Now in that case, maybe you still consider not
- to use blockchain because otherwise,
- as I mentioned before then these entities
- will become the bottleneck of the whole procedure.
- Only in the case when you are quite sure
- that the majority or even all of the entities
- will try to join the blockchain platform,
- then you start to consider
- whether the blockchain platform
- is a good infrastructure
- for the application.
- Then the next question you should ask
- is whether the application involves
- high-frequency transactions.
- At the time of the course actually most
- of the platform might not be able to deal
- with high-frequency transactions.
- If your answer is yes,
- my application involves high-frequencies transactions,
- then in that case I also recommend you
- not to use the blockchain platform.
- But on the other hand, if the answer is no,
- you have a database to maintain
- but you do not have a trusted party,
- trusted central authority or the transaction fee
- is too high and the transaction involves more
- than two entities and you know that most
- of the entities or all the entities
- will join the blockchain platform
- and the application will not involve
- very high-frequency transactions,
- then, in that case, we can actually consider
- using blockchain as your platform.
- But then you still need to
- evaluate one more characteristic
- because after all, we will need to see
- whether the blockchain can
- actually helps you to save money,
- save time, etc.
- In other words, I will need to look at the characteristics
- of the application to see if they actually emphasize
- the chain of custody,
- or will the blockchain platform help you
- to save the processing time
- or will the blockchain platform help you
- to locate the product or service you like
- in a many-to-many relationship?
- Now that in that case,
- I think we should go for the blockchain.
- I hope the flow chart is clear enough
- for you to have a brief idea
- when you have tried to consider an application,
- whether it’s good for blockchain or not.
- My final remark is that, even if you think
- that your application should go for blockchain,
- I hope you still remember in the earlier section
- we talked about how we can also classify blockchain
- into public blockchain, private blockchain
- or even you can in the middle
- have a hybrid blockchain.
- If that’s the case,
- then we still need to choose what type of blockchain
- you’re going to implement for your application.
- Now, which type of blockchain you need to pick,
- actually, depends on two factors.
- Now, because public blockchain relies on all the entities
- in the blockchain to make the final decision
- of the blockchain,
- so the trust model will rely on all the entities
- and these entities are allowed to freely
- to join the blockchain
- without any verifications, validations or authentications.
- In other words, if you use a public blockchain
- you need to trust the entity who will make
- the fair decisions.
- Now on the other hand, if you do not trust all the users
- in the blockchain, you may go for a private blockchain.
- In other words, the user will be authenticated
- before you allow them to use your blockchain,
- or you can pick a middle model.
- For example, the miners are all the authenticated users
- but the other users can freely join the blockchain,
- so this will be the hybrid model we talked about.
- So which blockchain you need to pick depends
- on how much you trust the entities
- and to what level you want your application
- to release the decision-making to the entities.
4.2.0 Blockchain and Enterprise – A Technology of Coordination (Charles d’Haussy from ConsenSys)
- So when it comes to enterprise blockchain,
- it really comes back to this first definition
- we shared earlier on, that blockchain offers
- a technology stack to coordinate things.
- And the way enterprises identify value
- in the blockchain’s value proposition is
- that many companies are working
- with many different stakeholders.
- So think, for example, of the supply chain industry.
- In the supply chain industry, your job is basically
- to pick up goods, which are ready out of a factory,
- put them on the trucks, the truck goes to the boats,
- the boats go to the other side of the world
- and it involves so many different players,
- so many different actors.
- And that’s where the technology of coordination
- that is blockchain really helps to build
- an infrastructure where you can coordinate
- the work for all these people
- and you don’t depend only on one player.
- So this is one of the core value propositions
- of blockchain enterprise.
- Where we find a lot of traction right now is
- in financial services again
- because the financial services
- industry is a very big industry involving
- a lot of different players and a lot
- of different actors, which work together
- and blockchain is a way for them to work
- together much more efficiently.
- So if you think, for example, of the way
- you distribute today a financial product,
- there is usually an issuer of an insurance,
- for example, and then there is insurance workers
- and then there is insurance agents.
- And all this work and all this information
- they share together by promoting, selling,
- distributing insurance contracts involve
- a lot of information to be
- shared in a very trusted manner
- because if you lose information on the way,
- you put some people life at stake basically.
- So in a way, you want to disintermediate.
- But the way to disintermediate if you don’t have
- the right technologies, not every company is ready
- to take over the job of intermediaries, right,
- unless you’ve got the right technologies.
- And this is where people are building
- a lot of blockchain enterprise solutions
- to get more direct access with their customers
- in a very organised way, and very transparent way,
- and automated way using smart contracts
- and using blockchain infrastructure.
- Another way enterprises, I will say have as a benefit
- of blockchain is by building consortiums.
- So if you think of different banks
- or if you think about different actors
- of any stock market, there is many different actors,
- in a way they are happy to transact together
- but they are also competing, maybe, in some ways.
- Or they don’t always give so much trust
- to each other for some reason.
- So in this case, you want to build a consortium.
- A consortium is basically a
- group of companies bringing
- together, they are working on the same market
- on different part of this market for different industries
- and they create a consortium to decide,
- we want to build together, what infrastructure,
- which would be trustless, which would help us
- to coordinate things.
- And this infrastructure, we don’t want it to be
- kind of managed, or led, by a single party.
- We want to have this platform,
- built and co-managed by everyone, so we all trust
- and we know it’s not a platform belonging
- to one player only.
- So we don’t have to trust one player only,
- anyone can take, I would say the leadership
- or decision on this platform.
- And the way to design today consortiums
- around one technology using
- blockchains really makes sense
- because all these players build a consortium,
- builds the rules of how they want to interact together,
- and basically apply these rules on blockchain
- and then they all co-own the infrastructure.
- They all cooperate in this infrastructure.
- And the technology of blockchain has been designed
- exactly for that, so it’s a very excellent way
- for enterprise to work together using
- the technology which has been designed for them
4.3.1: Why Permissioned Blockchains are used in Enterprise Network? (Dr. Paul Sin, Consulting Partner from Deloitte, China)
- Hello everyone, I am Paul Sin.
- I am the FinTech partner for Deloitte
- as well as the leader
- of the Asia Pacific Blockchain Lab in Deloitte.
- In Deloitte, we have three blockchain centers,
- one in Hong Kong looking after Asia Pacific,
- one in Dublin look after EMEA,
- and one in New York looking after America
- and we work very closely together.
- So today, what I’m going to do is
- to share some of the use cases,
- especially global use cases,
- which we have deployed not just as a proof of concept,
- but also in production environment,
- and they are already serving
- real business problems and scenarios.
- So maybe I will start with defining
- what is enterprise grade blockchain?
- A lot of people associate blockchain with Bitcoins,
- and/or Ether or other crypto assets.
- But in a lot of enterprise applications,
- we do not use that kind of blockchain.
- Those blockchains are called public blockchains.
- And in public blockchains, all the users are anonymous.
- And we’re trying to create an immutable ledger
- for anonymous user to transact with each other.
- While we are–
- While this is a very idealistic platform,
- it has some limitations that enterprise find it difficult
- to put in real application.
- One of them is the
- the slow performance.
- For example, in Bitcoin, it takes maybe 10 minutes
- to complete a transaction.
- Ethereum, maybe a few seconds to 12 seconds.
- This kind of network is far from sufficient
- to support all these enterprise application.
- There is also another reason
- why we do not use public blockchain,
- because it consumes a lot of computing power.
- So, if I need to install supercomputers
- to have the network up and running,
- it will be too costly for enterprise.
- What we use in enterprise environment
- is usually permissioned blockchains.
- In permissioned blockchains,
- we do not have anonymous users.
- All the people that are using the blockchain
- have gone through an onboarding process.
- And they are issued with digital signatures,
- so we know who these people are
- and when they are committing a transaction,
- we can trace it back
- to the original initiator of the transaction.
- So, there will be no risk of like money laundering
- in this kind of network.
- And the performance is very fast
- because I do not need anonymous users to do mining
- to prove that they are legitimate users.
- They already have a digital signature.
- So we know these guys are legitimate users already.
- Because of that, the transaction speed is very fast.
- Usually we can have few thousands
- like five to six thousands transactions per second.
- Some networks that are running today
- in production can go up to
- 20,000 transaction per second.
- And this is the speed we need
- for enterprise applications.
- Now, when we come back to the use cases,
- why do we need blockchain?
- Blockchain is a data layer in technology.
- And we have technology for
- sharing data since the beginning
- of the computer science technology.
- So in the past, if I need to share data, for example,
- within an organisation across different departments,
- I can create a centralised database
- and everyone put their data in,
- and we can share the data effectively.
- And those systems now become
- the ERP system for traders
- and corporates or maybe core
- banking system for banks.
- But when we are exchanging data,
- real-time between corporations or between businesses,
- then this kind of technology will not be applicable.
- If I’m a bank, for example,
- and I want to exchange the customer information
- with the insurance company,
- I’m not going to open the insurance company system
- and enter the customer information in their system.
- Vice versa, the insurance company will not use
- the bank system to enter the
- data in my core banking system.
- And because of that,
- we need another way to exchange data effectively
- between two enterprises,
- who both own large enterprise systems already
- in their own environment.
- We develop something called API,
- application programme interface,
- which connect these two systems together,
- and these two systems can then
- exchange data automatically
- real-time without human intervention.
- API works very well,
- except that when we are transferring
- sensitive customer information
- across organization boundaries.
- Then we are going to violate a lot of data privacy laws.
- Like, in Hong Kong, we have PDPO.
- In China, we have Cyber Security Law,
- and a lot of these kinds of law.
- And globally, we have GDPR,
- and this law will forbid us from
- exchanging sensitive customer information.
- This is one of the reasons why we use blockchain,
- or to be more precise, distributed ledger technology.
- There is also another reason why we need blockchain.
- If in an ecosystem, there’s only one data producer.
- Let’s say, if I’m a credit rating agency,
- I provide credit rating of different enterprises
- to the financial institute.
- And in that scenario, there’s only one data producer.
- All the people in the ecosystem are data consumers.
- And in that case, we can use OpenAPI,
- and we call that utility model.
- So as a credit agency,
- I let people subscribe my API
- to obtain credit ratings,
- and that is an effective model.
- The other way around,
- if there are many data producers
- and only one data consumer, like a regulator,
- a regulator will collect all these regulator reports
- from all the financial institutes in the ecosystem.
- And in that case, I can also use OpenAPI,
- I can ask all the financial institutes
- to submit their regulatory reporting through OpenAPI.
- And that also works very effectively.
- The only situation where API does not work well is
- when everyone can be a data producer and consumer.
- So let’s say if this is a KYC network,
- Know Your Customer network,
- and I am a bank,
- if a customer come to my bank to open an account,
- they may probably spend like
- one or two hours to go through
- all these customer due diligence process.
- And after they have done all that
- and I open an account for him or her,
- when this customer go to another bank,
- they need to spend another one and two hours
- to do the same thing.
- So it doesn’t make a lot of sense for the ecosystem
- because every bank will follow the same procedure
- to do this customer due diligence.
- Why do we need to repeat that again and again?
- So, a better way to do that is,
- if the first bank have already done the KYC process,
- I will put that results on a network
- where the result will be
- synchronised to all the other banks
- in the ecosystem.
- And when the customer go to another bank,
- then immediately within a few minutes,
- they can open account for this customer.
- And that sounds very perfect,
- except that there are data privacy issues
- on sharing KYC information.
- So, due to the hashing algorithm and encryption engine
- in distributor ledger or blockchain,
- we can now synchronise this
- sensitive customer information
- without violating the privacy ordinance.
- That’s for the first thing.
- Second is that, in this ecosystem,
- every bank is a data producer and data consumer.
- And if I use API to do this,
- I need to create point to point integration among all
- the combination of these banks.
- That means, if I have like seven banks,
- I may have 42 integration points.
- And that is very hard to build and maintain.
- If one bank changes their API interface,
- six other banks will need to re-build their interface again
- and test the whole thing again.
- So this is not a very effective way to distribute data
- and synchronise data.
- Blockchain provide a mechanism
- which all this KYC information will then be broadcast
- to everyone and without exposing the identity
- of the customer.
- Only when the customer goes to
- another bank, give consent,
- and then provide their identity,
- the second bank can then retrieve the KYC information
- from this KYC network.
- And this is exactly how we apply
- distributor ledger or blockchain.
- So, this just illustrates why we use blockchain
- instead of traditional data base
- and the OpenAPI technology.
- If you are trying to solve a problem,
- what we define as real-time,
- secured B2B synchronisation
- of data, especially sensitive data.
- In an ecosystem with multiple
- data producers and consumers
- then distributor ledger will be
- the best technology available at the moment
- for you to solve that business problem.
4.3.2 Use Case: Blockchains for Trade Finance (Dr. Paul Sin, Consulting Partner from Deloitte, China)
- Let me give you a simple example.
- If I am a bicycle manufacturer in China
- and I am exporting bicycles overseas.
- One day I suddenly receive a purchase order
- from the States as an ordering of a thousand bicycle.
- If I can get the bank to finance me
- in working capital and produce those bicycles,
- I can produce those bicycles, ship it over,
- collect the payment, pay the bank back
- with the principal and the interest.
- And the bank makes money, I make money,
- the customer is happy so this is a perfect scenario.
- The challenge is, at the moment,
- a bicycle manufacturer like me,
- goes to a bank to apply for financing.
- Four out of five cases will be rejected.
- And there are three reasons why
- the bank does not finance me.
- The first is that they know me
- but they do not know the buyer in the States.
- So if they finance me, they don’t know whether
- even if I deliver the bicycles, they don’t know
- whether the buyer’s going to pay the invoice or not.
- Secondly, they are afraid that the P.O. has been tampered.
- So if the U.S. buyer is maybe like ordering 100 bicycles
- but then I add a zero and become 1000 and get
- a much larger amount of financing,
- the bank cannot tell.
- The third issue is duplicate financing
- and which is very common.
- Banks can lose like 200 million U.S. in one transaction
- because of duplicate financing.
- The idea is like this, if I am the bicycle producer
- I can take that purchase order,
- go to 10 different banks and apply for financing.
- And the bank will not know that they
- are the competitor or the other bank
- has already financed this SME.
- So everyone of them will finance me based on that P.O.
- That piece of paper and there’s no way
- we can detect duplication.
- If you want to solve that with traditional technology,
- what you can do is you put,
- ask all the bank to put all the purchase order
- they received as a collateral
- in a centralised database and
- de-duplicate all of this P.O.
- But this will expose all the bank’s customer information
- as well as their sensitive business
- turnover information, etc.
- So no bank is willing to do that and therefore
- in the past centuries, said trade finances
- has a lot of fraud which we cannot resolve.
- Now, with the blockchain technology, we can scramble
- all the data of the purchase order and all these trade
- documents, bill of lending, invoice, etc.
- And put in their – in every bank’s own data centre
- what we call a data node.
- And this data node will then synchronise
- all the data with all the other bank’s data nodes.
- And these data cannot be reverse-engineered
- in the original data form.
- But when the same P.O. is presented
- to two different banks,
- the way blockchain scrambles the data,
- we call that hash algorithm.
- The way we hash the same P.O. are the same.
- So the resulting hash will always be the same.
- And when we compare these two hashes,
- we know there is a duplicate financing.
- Similarly, when I provide the buyer’s identity
- and the Hong Kong or the Chinese banks
- do not know whether this buyer exists or not,
- they can check the KYC hash
- created by the American bank.
- And if the hash is the same as the hash I created
- based on the buyer ID the seller provided,
- then I know this buyer is a legitimate buyer
- based in the US and with the bank I can
- go on for all the KYC of the US bank
- and they have good credibility.
- So this is very important and that allows
- the whole ecosystem payers to
- share this sensitive information
- without worrying about breaching data privacy.
- And with that, people like the buyers, sellers,
- the shipping companies, the banks,
- the insurance companies,
- they all feel comfortable
- using the data on blockchain as a trusted source
- of trade information that allows them to do,
- reduce the risk of the whole ecosystem.
- There’s no duplicate financing risk for the bank.
- There’s no forged document
- risk in the financing process.
- There’s no forged document for the insurance.
4.3.3 Use Case: Blockchains for Supply Chain Financing (Dr. Paul Sin, Consulting Partner from Deloitte, China)
- If you think about financial services,
- what they do in essence is to price risk.
- If the risk of an ecosystem is lower,
- then the financial charge and the financial cost
- of doing business will be lower also.
- I was told that when insurers
- insure a container of goods,
- being in transit,
- they actually do not know what is contained
- in the container.
- You can ship a container of
- glass or a container of diamonds.
- They will charge the same premium,
- because they don’t have the information.
- With Blockchain you have transparency
- of all this information.
- And insurance can charge you
- a much more reasonable premium.
- And that also means a lower cost for SMEs.
- With all this transparency,
- SME will have a much higher financing rate.
- With that they will have a higher
- production capacity.
- SMEs represent almost 70 to 80 percent
- of the GDP of developing countries.
- That’s why governments are very keen
- to adopt, issue with ledger,
- to help SME to obtain financial services.
- So that a whole economy can thrive better.
- So this… Some of the top use cases of
- Blockchain in the world now
- are trade finance and supply chain financing.
- The second biggest use case is
- supply chain traceability.
- So traceability has two angles.
- One angle is fighting counterfeit products.
- The other one is to prove that your products
- are sustainable.
- Or from sustainable sources.
- At the moment, there are a lot of
- counterfeit products everywhere in the world.
- Official statistics are like seven percent
- of the global trade are counterfeit products.
- But in some developing countries
- this figure is much higher.
- There is a lot of effort in trying to trace
- the product back to the origin.
- One of the famous cases will be diamond.
- We do not want diamonds from the conflict zones,
- what we call black diamond,
- to be circulated in the economy.
- Because of that,
- we want to know where those diamonds come from.
- If I can have the miner, the polisher, the wholesaler,
- the retail, everyone to put the record on the Blockchain,
- then we can trace the diamond
- from the hands of the customer
- all the way back to the mine.
- We can feel pretty assured that this diamond
- is not a blood diamond.
- And also with that,
- you can also prove diamonds are not stolen
- or from gangsters or criminals.
- You can then obtain financing, insurance,
- and other kinds of financial services
- around your product.
- So this becomes a very important use case.
- We have seen people tracing
- not just diamonds but wine.
- A lot of wines are fake wines at the moment.
- People trace Wagyu beef,
- because those are luxurious products.
- People trace palm oil.
- Because we want to know whether the palm oil
- is coming from deforestated area.
- Otherwise we cannot import any into Europe.
- We also want to see
- if some of the vaccines are from
- real pharmaceutical companies
- or they are fake vaccines.
- You probably have heard that there are
- food-safety centers established
- by large supermarkets
- to make sure all the food are safe
- when they are being put on the shelf.
- This is probably the second biggest use case
- in Blockchain applications.
Use Case: Cross Border Connectivity – Trusted Data Transfer (Dr. Paul Sin, Consulting Partner from Deloitte, China)
- There are many other kinds of blockchain applications.
- I will mention the last one
- which explains the value of blockchain.
- So at the moment, there are a lot of discussions
- about Greater Bay Area in south China.
- And compared to all the other bay areas
- like San Francisco or Tokyo,
- our Chinese greater bay area is quite special.
- Because we are talking about one country, two systems,
- three jurisdictions and three different currencies,
- and also controls on people flow and capital flow, etc.
- So one thing we need to solve is if we want to facilitate
- products, people and capital flowing cross-border,
- we need to allow information to flow first.
- Let’s say if a citizen wants to move from Hong Kong
- and to China and work there.
- Then you need to move all the employment records,
- pension records, your identity information,
- tax equalisation information.
- There is a lot of information we need to synchronize.
- Before we can let that person settle down
- smoothly in a new place.
- So in order to do that we need a way to send
- sensitive customer information,
- sensitive individual information cross-border.
- And this is something a lot of people are working on.
- In the financial services world we see that people
- like credit bureaus trying to synchronise credit reports.
- So that if I’m an SME in Hong Kong,
- I have a good credit report,
- I can go to China to do business and I can borrow
- from the bank in China who is inquiring
- the credit bureau in China to see my credit report,
- which is already synchronized
- from Hong Kong to China.
- We also see that in the past
- when insurance companies in China try to sell
- their product through the bank in Hong Kong or Macau.
- And the policy information
- cannot be synchronised cross-border.
- And because of that there are a lot of inefficiencies.
- So for example, if I am a insurance customer.
- I bought the insurance policy from a bank in Macau,
- but the insurance provider is in China.
- And I go to the branch to pay the premium.
- The bank actually does not know
- how much premium is outstanding.
- So they will accept whatever I pay them.
- They ship the premium back to China.
- They do the reconciliation and then they find discrepancies.
- They inform the bank, the bank calls the customer
- chase for the discrepancy.
- And then they will settle all these payments
- like 20 days later.
- So this is a very inefficient process.
- With the ability to synchronise the data cross-border,
- we can shorten all these turnaround times and reduce
- manual efforts and also the errors in the process.
- All the processes in this kind of collaboration,
- we call that bank assurance partnership,
- can be streamlined through a distributed ledger.
- And we find that almost 86% of manual efforts
- can be reduced in this kind of partnership.
- So if you have a B2B partnership
- and you have a lot of these sensitive
- customer information being synchronised.
- Blockchain will be a very effective tool to do that.
- Looking forward with all these successful cases
- already in production,
- I would say that we are already way past
- the proof-of-concept stage,
- which is what people have been doing back in 2016.
- So 2016, 2017 are the years of proof-of-concept.
- A lot of press releases on different kind of POC.
- But in 2018 we start to see a lot of platforms
- going to production.
- You probably heard of the
- Hong Kong Monetary Authority
- with 12 banks, they have eTradeConnect in production
- announced in Fintech Week.
- We have we.trade in Europe now based
- in Dublin launched in production.
- We have Voltron, Marco Polo…
- There’re a lot of trade finance platforms
- now being launched in production.
How to Deploy an Application on the Ethereum Blockchain? (Charles D’Haussy from ConSenSys)
- So if I want to deploy a smart contract
- or an application on the Ethereum blockchain,
- what do I need?
- Do I need an account on
- let’s say, Google platform or something like that?
- How do I actually build something
- on the Ethereum blockchain?
- The Ethereum blockchain is an open-source blockchain.
- So a lot of the tools to interact with the blockchain
- and build on the Ethereum blockchains
- are available free of charge.
- So you will start by creating yourself an account
- on Ethereum which is something
- which is totally free of charge,
- and then you will get yourself familiar
- with how we code smart contracts, for example,
- and you’re going to be able to basically launch
- and host your contract on the Ethereum platform.
- Then when you want to run this program
- there will be a few costs involved such as gas,
- what we call gas, is a little bit like the same way
- you put gasoline in your car,
- there is gas also to basically run your program
- on the blockchain.
- So the same way
- if you host your website on a server for your blog,
- for example, you will need to pay every month
- a monthly fee to basically rent this space on a server.
- You will also rent some space on the blockchain,
- on the Ethereum blockchain to run your program.
- So once it’s up on the Ethereum blockchain,
- once a program is up on the Ethereum blockchain,
- could ConsenSys or could Ethereum just decide
- to take something down?
- The beauty of the blockchain
- and the beauty of Ethereum
- are that things happening on the blockchain
- are totally transparent and they are immutable.
- So every single transaction, every single activity
- is recorded by the whole network itself.
- So today you find about 10,000+ different nodes
- within the Ethereum blockchains
- which really guarantees you
- that it’s recording in a very distributed way
- and also an immutable way.
- So it’s a platform which belongs to everyone
- and everyone can build on it and no one has the right
- or the capacity to remove something.
- So a lot of people know about CryptoKitties,
- a very famous Ethereum decentralized application.
- Besides CryptoKitties,
- are there any Ethereum applications
- that have reached mainstream adoption?
- So it’s still early for the Ethereum ecosystem.
- But we see some very strong signals that the growth
- of the ecosystem is really coming very strong.
- So you have for example, in Switzerland, parts
- and certain cities in Switzerland such as the city
- of Zug, which is I think an online identity,
- blockchain identity system
- and blockchain-based voting system for their citizens.
- You see a lot of use cases which are live
- in production right now,
- which involves the supply chains.
- So when you want to basically record the journey
- of goods and journey of raw materials
- to really understand where they are coming from
- and how they bring together a product.
- If you really want to understand the provenance
- and the product journey.
- There are many use cases
- which relate to payment, for example.
- So instead of using the traditional legacy system
- to send money cross border,
- you’re going to use the blockchain
- to basically move money
- between one country to another.
- And this can be done with Crypto money
- or this can be done also with a Crypto Vacuum
- for traditional Fiat money.
- So there are many use cases happening right now.
- This is the beauty of this technology
- and why so many people are excited
- about the Ethereum blockchain is,
- it’s an ecosystem of talents.
- It’s an ecosystem of more than 300,000 developers,
- all building their own products,
- their own infrastructure on the core layer
- that is the Ethereum blockchain.
- So it’s really, I would say, a very large playground
- for technologists, for creators,
- for entrepreneurs to build
- use cases related to identity,
- related to a change of money cross border,
- for example, on the supply chain side,
- whenever you want to document
- or get your online identity and
- give ownership to the users,
- this is a playground which is really fantastic.
4.4.2 Use Case: Bounties Award Ethereum for Cleaning Beaches (Charles D’Haussy from ConSenSys)
- One use case of blockchain which really illustrates
- this coordination capability
- of the blockchain technology,
- there is one initiative
- which is called Ethereum Bounties.
- So you can basically coordinate an action from a group
- of people in a decentralized manner
- and decide to give rewards to
- people for doing something.
- So for example, one very concrete and
- very original example here in Asia, a few weeks ago
- in the Philippines, some people volunteer
- to clean up a beach.
- And they said we are really
- happy to clean up this beach,
- but we would love to have some rewards to organize
- as a logistics for us for these
- 50 people to go to the beach
- and to basically bring back, also, all the waste
- they collect from the beach back to a proper place.
- So they wanted also to find
- some reward enough for a day job
- for some people who are ready to do these activities.
- So all of these has been coordinated using
- the Ethereum Bounty systems, which is decentralized,
- where people were saying, I love this project
- and I’m happy to contribute maybe $1, maybe $5, $10,
- and people basically crowdfunded
- using the Ethereum blockchain rewards,
- an event of cleaning a beach.
- But you can think the same
- thing for giving some lessons
- or doing all kind of activities in our everyday life
- using decentralized technology.
- So the people were able to get rewarded,
- have a guarantee of reward to be paid to them,
- and being brought together just by a technology
- which is very optimized for this kind of coordination.
4.4.3 ConsensSys and the Ethereum Platform (Charles D’Haussy from ConSenSys)
- So ConsenSys is a group of
- technologies and entrepreneurs.
- We were founded by Joseph Lubin in 2015.
- Today we represent about 1,000 people,
- which are all working on mostly
- on the Ethereum blockchain.
- And we developed technologies
- which are low layer technologies.
- So we do a lot of research and tools for people
- to interact with the Ethereum blockchain,
- but we also built different companies
- and kind of organisations
- which are focusing on different use cases on the blockchain.
- So some people within ConsenSys are working
- and doing research for Ethereum.
- Some of the group of people are working
- on the use cases around finance.
- We have a group of people working on social impact
- of the blockchain, developing applications
- with different stakeholders
- to really create an impact,
- using the technology of blockchain.
- We are also an accelerator for
- all blockchain entrepreneurs
- to help them really get the idea together
- and kick off the projects.
- And we also do all kinds of activities related
- to the community engagement to make sure
- that the people will capture the potentials
- of the Ethereum technology
- and one more vertical we have within ConsenSys
- is what we call ConsenSys academy,
- where we help the executive, we help developers
- to really understand the potentials
- of the Ethereum blockchain and
- give them very practical
- and concrete trainings to get their hands on,
- starting to code, starting to build businesses,
- but starting to build projects
- on the Ethereum blockchain.
4.4.4 ConsesSys Use Case: Project i2i(Charles D’Haussy from ConSenSys)
- ConsenSys has here in Asia one project
- which is really I will say a milestone for us
- and a marquee project.
- It’s called a Project i2i.
- So i2i means individual to individual
- and infrastructure to infrastructure.
- So what i2i is about,
- it’s about connecting the rural banks in the Philippines,
- to the core banking system of
- the Philippines in the cities.
- So the Philippines is a country
- which is made of many different islands
- and you can imagine that
- building infrastructure over there
- is very costly and extremely complex.
- So what’s happening is there is some remote villages,
- which do not have access to the same banking services
- you will get in the traditional larger urban cities,
- in the Philippines.
- And what we’ve been building over there together
- with Union Bank, one of the
- main banks in the Philippines,
- is really extending the network of services
- and the infrastructure extending from the core cities
- to the rural banks using blockchain technologies.
- Why we choose blockchain technologies in this case
- is because it was the easiest way
- to connect all these different rural banks.
- There’re hundreds of them
- spread all over the Philippines
- and connect them back to the existing system.
- And if the existing system was to be built to reach them,
- it will be extremely costly
- and basically possibly never happen.
- So the way was really to kind of bridge the gap
- in a trustless manner, in a cost-efficient manner,
- to help all these rural banks to provide cash services,
- to provide loans, to provide all the services of a bank,
- but connecting them back to the main bank
- using the blockchain technologies.
4.5.1: Use Case: Trade Finance and Supply Chain (Anil Kudalkar, MD, MaGESpire Partners)
- I’m Anil Kudalkar, managing director
- and co-founder of MaGESpire Partners.
- Today I’m going to speak about some of blockchain’s
- most used cases and the best fits.
- The first one I want to speak about
- is trade finance and supply chain.
- Automated smart contracts and blockchains
- can transform how business
- processes of supply chain and trade finance works.
- Since supply chains are
- complex and distributed involving many parties
- across the globe, there’s a lack
- of trust between one another,
- leading towards the need for trusted third parties
- like banks or intermediaries.
- With blockchain, smart contracts can be
- executed automatically to transfer any
- goods and money without the need for
- middlemen such as a bank and their exorbitant fees.
- This will not only help in building a trusted network
- but also ensures authenticity and origin of
- product being supplied.
- Trade finance it has heavily been a paper-based
- industry as of 2017 it was like about
- 9 trillion transactions worth when done.
- Typically the steps involved are
- creating a purchase order then the
- exporter creates an invoice to the importer,
- the importer requests the LC, the bank then
- approves and publishes the LC,
- and exporter creates a packaging list.
- Then, the carrier creates and publishes the bill of lading
- and then it’s the exporter
- submitting the invoice.
- So there’s a lot of procedures involved, and lastly the
- issuing banks endorses the released documents.
- One good example which is from
- Hong Kong is about HSBC late in 2018
- successfully completed the first batch
- of a live pilot trade finance
- transaction on eTradeConnect.
- This is a newly launched blockchain platform
- co-founded by seven banks and
- facilitated by HKMA which is the
- regulating body. The platform enhances
- efficiency and transparency by digitizing
- trade documents and automated
- trade finance processing,
- leveraging the unique features of blockchain.
- The key benefits we saw in the pilot were
- digitized trade loan applications,
- application to approval times in the life of transactions
- reduced from one and a half days to just four hours
- and increased efficiency and transparency of
- trade finance transactions.
- Among the first batch, there was also a purchase of
- supplies by a furniture and household
- retailer from its supplier.
- The transaction involved a purchase order
- and invoice as well as a proof of delivery
- which has created exchange and
- confirmed on the eTradeConnect platform.
- The counterparty was able to
- submit a trade finance request directly to the bank
- based on the documents uploaded on the platform.
- eTradeConnect is yet another
- milestone in the evolution of commercializing
- blockchain globally.
- What are the most important benefits
- of the technology of blockchain in trade finance?
- One, is the traceability – tracking goods
- and trade assets where they are
- currently residing, then, related asset information
- can be relayed, again, real-time.
- Transparency – increased commercial transparency
- can reduce delays in financing trade and
- details of the transactions against commercial and
- agreements improve further trust.
- The other important point is auditability.
- Each trade finance transaction is
- recorded sequentially and indefinitely.
- So this provides an audit trail for the life of the
- trade asset between parties.
- And the next big aspect is security.
- Each trade transaction is verified within the network
- using independently verified complex cryptography.
- Authenticity of the trade-related information
- can be assured.
- Then, obviously there is collaboration
- which allows each party to share easily
- and securely trade finance-related data.
- Fragmented internal systems are
- centralized, allowing interoperability.
- Again, now coming to efficiency.
- Transactions are completed within
- a shorter amount of time.
- This ability to operate smart contracts
- which automatically trigger commercial transaction.
- The supply chain management is the next example
- I would highlight.
- I would like to take one
- example from the pharma industry.
- Product tracking refers to tracing of
- unit levels the drugs and medicine
- across end-to-end supply chain using blockchain.
- All stakeholders in the ecosystem can
- access the provenance,
- authenticate items and prove compliance.
- This is enabled by
- the real-time capability and distributed features
- associated with the platform.
- For example, tracking drugs on the blockchain
- throughout the life cycle from manufacturing
- to patients could facilitate counterfeit-free
- drug identification or assist drug recall management.
4.5.2 Use Case: Capital Markets (Anil Kudalkar, MD, Magespire Partners)
- Next example I would like to highlight is from
- capital markets and settlements.
- For example, the Swiss exchange SIX expects its
- traditional trading platform to be overtaken
- within a decade by an alternative
- platform using only blockchain technology.
- SIX digital exchange, which is the SDX,
- is due to launch in mid-2019, and initially there will be
- a parallel run to the existing
- platform of a purchase and sale of securities
- on a blockchain on a distributed ledger.
- The transactions can be
- completed in a fraction of a second.
- Another example is the Australian exchange.
- ASX has become the first major board to announce
- an adoption of blockchain technology to record
- shareholding and manage the clearing and
- settlements of equity transactions.
- Blockchain or DLT uses shared ledger to
- permanently record transactions in a way that is
- practically impossible to tamper with.
- The ASX said it will soon be scrapping its old
- clearinghouse system, which is Chess.
- In the 90s, that was the state of the art, right?
- But the new testing of the new DLT technology
- over the last two years has gone better.
- Now, coming on to the Hong Kong exchange.
- The Hong Kong exchange is entering an open-ended
- period of consulting where it wants to use
- DLT for the stock connect program.
- Once this is sort of done it will try to implement it
- into other areas within the exchange.
- So this will be real-time and transparent synchronization
- of communications to move away
- from sequence-driven,
- one step at a time processing.
- The stock connect is one area
- which they are doing a pilot and then they will be
- applying it to other areas of the exchange.
- Away from securities, some of the other compelling
- applications of DLT in the capital
- markets include payments.
- For payments, the DLT can streamline end-to-end value
- transfers, reducing cost,
- and operational risk settlement process.
- For example, Ripple’s XRP ledger provides real-time
- cross-border settlements using
- tokens that represent central bank currencies.
- In foreign exchange, HSBC’s FX Everywhere protocol
- processed more than three million
- intercompany FX transactions worth
- 250 billion in the first year.
- Syndicating, lending trade finance and other forms
- of bank finance still rely on paper documents
- and manual processes.
- DLT could transform this by providing a shared record of
- shipments, ownership, financing, and insurance.
- The we.trade platform built by 20 European banks
- including HSBC and hosted on the IBM’s blockchain
- conducted its first open account trades in July 2018.
- Then it will be fund administration as an application.
- A DLT ledger recording the creation, redemption and
- transfer of funds units would eliminate many of the
- current complexities of fund administration.
- It could unify cross-border sales processing
- and transfer agency.
- There are two large platforms,
- Fundsquare and Calastone,
- are both developing a new DLT
- infrastructure based on blockchain.
- The other important application is
- customer identification.
- An industry-wide distributed ledger could host
- a shared record of beneficial owners
- such as a utility that would give appropriate
- permissioned access to market participants
- allowing them immediate KYC and AML checks,
- assisting with client onboarding
- and enhancing tax reporting.
- DLT can deliver many potential transformative
- applications in the capital markets,
- especially the post trade arena
- offers the most compelling opportunities.
- DLT could also reshape the practice
- in other areas of the markets, especially
- as interoperability between ledger starts to take shape.
4.5.3 Use Cases on General Government Services & Sustainable Livelihood (Anil Kudalkar, MD, Magespire Partners)
- We’ve seen that blockchain technology has been hailed
- as a revolutionary means to secure
- and transparent record keeping and data sharing
- with seemingly endless potential uses
- in the wide variety of sectors.
- Today government agencies
- around the world are looking
- for blockchain to help their services be more efficient.
- First, I would like to highlight the identity
- as one of the biggest applications.
- Perhaps the most essential and enabling use case
- for a blockchain in government services
- is the realm of digital identity.
- Governments are not only the source
- of key identity information for citizens,
- but from official registration from our births to demise,
- issues of death certificates, they need to also enable
- this in a digital format.
- As this has proven difficult to achieve
- in the traditional centralised technologies,
- some governments are looking
- to use blockchain to realise this idea.
- The second is title and asset registrations.
- The same process can, of course,
- be used to secure information
- about almost any kind of registration,
- for example, businesses, automobiles.
- Some of these used cases could have
- significant social impact,
- such as registration of firearms
- and ammunition to track their usage or abuse.
- Blockchain has been long proposed
- for use in land registries, for instance,
- this was initially the case
- in all developing countries looking
- to fight corruption by local officials.
- The third would be healthcare.
- Another important use case
- for blockchain is in publicly provided healthcare.
- There are two main areas.
- First, the blockchain can potentially improve the
- securing and sharing of patient medical records.
- Today medical records are typically kept separately
- in doctors’ offices, hospital databases.
- They are still often shared manually and not always
- in a very secure way.
- This is a problem, considering the sensitive nature
- of the data.
- It can also get complicated in multi-provider system,
- where various people and institutions
- have to make input to a patients data.
- Blockchains are very good for such scenarios
- providing a clear audit trail of inputs
- by multiple sources and ensuring the data
- is not manipulated or corrupted once it is saved.
- Estonia, which has established
- a national electronic health record is contemplating
- using a blockchain based registry
- to ensure the correct handling of sensitive health data
- by securing the entry of new data into the record
- and providing an immutable audit trail
- of how the data has been used.
- In Sweden there is an initiative
- to develop a national blockchain for healthcare records
- to give citizens more control of their data.
- Blockchain technology offers a possibility
- to radically streamline such processes.
- In Sweden recently they’ve carried out
- a first successful test transaction
- of a fully blockchain-based transfer of title.
- In the UK HM Land Registry is testing blockchain
- in its bid to become the world’s leading land registry
- for speed, simplicity, and an open approach to data.
- Health data is not just important for patients.
- Anonymized, it can be a great source of information
- for researchers and authorities.
- In Europe, My Health My Data, which is being funded
- under the EU Horizon 2020 programme,
- aims to use blockchain to create
- the world’s first open biomedical information network.
- Among other things it would encourage hospitals
- to make anonymized data available to open research
- and make it easier for citizens
- to take control of their health records.
- In the above use cases what is proposed
- is generally not storage of data itself
- in a blockchain network, rather the blockchain
- is used to store proof that off-chain data is genuine
- or to store a record of who has access to what data.
- This allows data owners to store their personal
- and medical data in secure locations of their choice,
- rather than allowing large number of health providers
- to store the same data, sometimes in antique
- and poor IT systems.
- Education certification is another area
- where important personal data
- tends to be kept in silo databases.
- Typically the universities,
- or schools that issue the diplomas.
- Getting access to the information
- in order to prove credentials
- can be a laborious undertaking.
- Degrees can also be relatively easy to falsify,
- causing problems for those who are trying
- to verify these credentials.
- Blockchain-based systems can help here
- on both sides of the equation.
- As with the health records they can allow individuals
- to take control of the education credentials
- through possession of verified records,
- which they can use as needed.
- Because such credentials can be easily verified,
- employers, or others who rely on them,
- can have more trust in their veracity.
- The potential of such an approach
- has been widely recognised,
- and many projects have already started.
- The University of Nicosia, for instance,
- already issues academic certificates
- that have been verified online by a blockchain.
- In Malta the government is teaming up with a
- startup to build a prototype system to do the same.
- A consortium of Malaysian universities
- is building a blockchain-based platform
- to combat fake degrees, while a French startup
- is looking to use blockchain network for the issuance
- of sharing of university and other degrees.
- The European Blockchain Partnership
- has selected diploma sharing on blockchain
- as one of the promising use cases to be deployed
- over the European Blockchain Services Infrastructure,
- a use case that is backed by several member states.
- The last one is e-voting.
- Voting is another important use case dependent
- on transmission of private but verifiable data.
- And e-voting has long been
- a great prospect for e-government.
- If citizens could easily and securely vote
- from any location, for example, using smartphones
- or your personal computers, we could in theory develop
- more participatory democracies,
- voting more often on more issues.
- With verified data on the blockchain
- it may be possible to design e-voting systems
- that are much more transparent and trustworthy,
- while preserving confidentiality.
- In such systems election authorities
- would issue voting credentials to users directly
- that could be used to cast anonymous ballots.
- Through various techniques it could then be possible
- to automatically count those ballots,
- ensure that no votes were cast more than once,
- and prove the validity of the count
- without revealing the identity of those who voted.
- The example here is citizens of Zug, in Switzerland,
- used their blockchain IDs earlier this year
- to conduct the cities first blockchain-enabled e-vote.
- While only consultative in nature, it
- may be one harbinger of other things to come.
- Similar blockchain based e-voting projects are
- underway in areas far-flung
- as West Virginia and Moscow.
- E-voting is also mentioned as a possible use case
- in European Parliament’s blockchain resolution
- of October 2018.
4.6.1 Use of Hyperledger Blockchain Technology in Trade Finance, Supply Chain and Digital Identity (Brian Behlendorf from The Linux Foundation)
- You know, people talk about applications a lot
- in blockchain, Hyperledger.
- Can you share with us some interesting applications
- using Hyperledger?
- Well the most common ones tend to be in Fabric.
- And actually, this is true for Sawtooth as well,
- tend to be in trade finance and supply chain traceability.
- So in trade finance, we have examples now of networks
- that’ve been set up in Singapore
- by a company called DLT
- Ledgers working with DBS Bank
- and others who’ve done hundreds
- of millions of dollars worth
- of extensions of letters of credit.
- In China, a bunch of the banks there
- have formed a consortium as well.
- Here in Hong Kong, they’ve launched something called
- eTradeConnect, a partnership with HKMA
- and a number of the Hong Kong banks.
- And another one called we.trade.
- So all of these different networks are
- springing up around trade finance,
- and not all of them are in production yet,
- but they are certainly growing in traction and I,
- this is not just like an experiment
- that will be thrown away.
- This is actually like creating real value.
- ‘Cause trade finance has some of these
- unique characteristics that
- I think blockchain technology
- is particularly well-suited for in terms of being
- cross-jurisdictional, international by nature,
- that sort of thing.
- And then, supply chain traceability
- is obviously very related to that.
- And part of the value there is being able to know,
- “Hey, I bought this electric vehicle.
- The battery has a lot of cobalt in it.”
- Cobalt only comes from a few countries in the world.
- Some of those have mines that are well-regulated
- and they keep child labour out,
- others do not have such good regulation.
- And so being able to trace-ably know that your cobalt
- comes from a known good mine,
- or the diamond in that diamond ring?
- Comes from a diamond mine that actually has
- appropriate controls to prevent child labour.
- Or even rice.
- I mean, at the other end of the spectrum
- from diamonds, right?
- There’s a big problem out there
- with fraudulent rice, you know.
- Fake rice, actually, in the supply chain.
- And also different qualities of rice, different varietals.
- You want to know that you’re getting the right one.
- But I think the largest meta use case kind of group
- that I like is back to digital identity.
- Digital identity is so essential to every digital process
- we have now, and we’re really
- behind where we should be.
- Your ability to prove that you have
- a visa to travel somewhere,
- your ability to prove that you have a diploma,
- is bound up in systems that are locked in
- and different standards, different protocols,
- even when they’re digital.
- And for many people around the world,
- they’re still not digital, right?
- And you can sense this in populations
- that cross international borders quite a bit,
- or in particular in populations that are refugees,
- that are leaving behind kind of a failed country,
- failed system.
- And so, a lot of interesting applications out there
- for the use of digital identity systems,
- distributed digitalized identity systems
- in the developing world,
- to give people a greater sense of participation
- in the global economic system,
- financial inclusion, and greater dignity.
- So I’m really excited about that.
- And we’re seeing, with Hyperledger
- Indy deployments now,
- in the United States and Canada, in the Netherlands,
- but also a project to bring a national digital ID system
- to the country of Sierra Leone.
- And I think we’ll even see countries like India,
- that have invested a lot in a centralised digital ID model,
- move to a self-sovereign or a kind of
- distributed digital ID model, because that’s the only way
- you can support migrant populations
- and some of the greater
- resiliency that that model brings.
4.6.2 To Use Or Not To Use Blockchain
- We also know that not all the applications
- fit blockchain platform, right?
- Have you come across any failure cases
- in applying Hyperledger in some use cases?
- In 2019, we know better how to build agile systems,
- how to start small,
- how to do POCs,
- how to grow them.
- All this technology is about trust, all right.
- Some markets have a big trust gap
- especially if you’re crossing international borders,
- especially if you have weak institutions,
- that’s going to matter,
- but in a single country,
- if you have parties that regulations are solid,
- and the court systems are efficient and all that,
- you might not need a blockchain right,
- and so the relative value of that
- differs use case to use case,
- and that’s where I have seen
- some projects get launched and people realise
- it’s not worth the extra cost because
- no blockchain solution is going to be faster
- than a centralised database.
- A centralised database is going to be
- faster and cheaper,
- easier to upgrade
- almost better by every measure
- except you have to figure out
- somebody to run that who you trust,
- and that’s when you want to use a blockchain
- is when you don’t want to give
- somebody that much power.
4.7.1 Use Case: How Walmart Brought Unprecedented Transparency to the Food Supply Chain with Hyperledger Fabric (Julian Gordon from The Linux Foundation)
- Supply chain is one of the hottest areas
- for blockchain solutions,
- with many use cases in production today.
- Two great examples are from Walmart
- and a start up from the UK called Circulor.
- At Walmart, they face the challenge
- that when an outbreak of foodborne disease happens,
- it can take days, even weeks, to find it’s source.
- Better traceability could help save lives
- by allowing companies to act faster
- and protect the livelihoods of farmers
- by only discarding produce from affected farms.
- Walmart thought that blockchain technology
- might be a good fit for the
- decentralised food supply ecosystem.
- To test this idea,
- the company created a food traceability system
- based on Hyperledger Fabric.
- Walmart, with it’s technology partner, IBM,
- ran two proof-of-concept projects to test the system.
- One project was tracing mangoes
- sold in Walmart’s U.S. stores,
- and the other aimed to trace
- pork sold in it’s China stores.
- The food traceability system
- built for the two products worked.
- For pork in China,
- it allowed uploading certificates of authenticity
- to the blockchain,
- bringing more trust to system
- where trust used to be a serious issue.
- And for mangoes in the U.S.,
- the time needed to trace their provenance
- went from seven days to 2.2 seconds.
- Walmart can now trace the origin of over 25 products
- from five different suppliers,
- using a system powered by Hyperledger Fabric.
- The company plans to roll out the system to
- more products and categories in the near future.
- It has announced that it will start requiring
- all of it’s suppliers of fresh, leafy greens
- to trace their products using the system.
4.7.2 Use Case: How Circulor Achieves Traceability of Tantalem Using Hyperledger Fabric (Julian Gordon from The Linux Foundation)
- Another great supply chain case study
- comes from Hyperledger member, Circulor.
- Rwanda is the worlds biggest supplier of tantalum,
- a rare mineral used to make capacitors
- found in devices like smart phones and laptops.
- But tantalum is sometimes smuggled in
- from conflict-ridden Congo,
- where it is mined by children
- or workers enslaved by warlords.
- This led the OECD, US and the EU
- to name tantalum a conflict mineral
- and pass regulations to improve its traceability.
- Despite these rules, no one had a fool proof way
- to prove where tantalum came from, until now.
- The Rwandan government and mine operator,
- Power Resources Group,
- wanted to prove that every bag of tantalum ore
- from Rwanda was mined, transported, and processed
- under OECD approved conditions.
- UK based technology company,
- Circulor, created a system
- that ensures tantalum is mined, transported,
- and processed under approved conditions
- with an unbroken chain of custody.
- They engaged stakeholders across the supply chain,
- mapped the tantalum supply chain,
- and created fool proof new processes
- to build the blockchain.
- Powered by permissioned blockchain,
- built on Hyperledger Fabric,
- the system uses facial recognition and QR codes
- to deliver a real world first,
- mine to manufacturer traceability of this vital resource.
- And the results,
- the blockchain based system to trace tantalum
- went live in three mines
- and an ore sorting facility in Rwanda
- in the autumn of 2018.
- The system is designed to slash today’s
- high cost for compliance, satisfy regulators,
- reassure consumers, and build revenues for Rwanda.
Module 4 Reference Reading
References and Suggestions for Further Reading in Module 4
NOTE: There are many published information on blockchain applications and use cases, the following are some examples:
- 17 Blockchain Applications That Are Transforming Society (Industry news article)
- Top 10 Real-world Applications of Blockchain Technology (Industry news article)
- 5 Applications for Blockchain in Your Business (Industry news article)
Module 5 The Limitations, Opportunities and Challenges of Blockchain
Welcome to Module 5

Dear Learners, Welcome to Module 5 – The Limitations, Opportunities and Challenges of Blockchain. In the last Module, we looked at the key selection criteria for blockchain applications and some best fit use cases in public and enterprise blockchains from guest speakers from different industry sectors. In Module 5, we are happy to introduce six guest speakers to you, among others, Malcolm Wright (Chief Compliance Officer at Diginex) who will discuss the Privacy and Security risks of blockchain and Jon Rout (Head of Product for APAC, Digital Asset) will share his expertise on Applied Smart Contracts. Then we will hear from Alan Cheung (Director, Advanced Digital Systems of Astri) who will share the opportunities of blockchain for health insurance, and Johnny Cheung (General Counsel of B.C. Technology Group) will discuss the benefits of blockchain in banking. Also, our key instructor from Introduction to FinTech course, Henri Arslanian (FinTech & Crypto Leader for Asia, PwC) will talk about the institutional opportunities in the digital asset space. Furthermore, our other key FinTech instructor, Brian Tang will talk about Understanding Facebook’s Libra – in the Context of Wechat Pay, Bitcoin and Hedera in a series of short videos. This is a pretty exciting week. May you enjoy the great contents from our guest speakers. HKU Blockchain and FinTech Course Team |
Module 5 Learning Objectives
After completing Module 5, learners should be able to:
- understand the security and privacy concerns of a blockchain platform;
- have a brief understanding of possible risks in different components of a blockchain platform;
- learn more the benefits of using blockchain in various applications and industries.
5.1.1 Five Modules in Blockchain Systems
- I hope you still remember
- that we have three properties
- that we want to satisfy for the blockchain platform.
- The first one is decentralization,
- that is we do not want to
- have a centralized management
- to overlook the system.
- The second one, of course,
- we want to guarantee the
- security and privacy, as well.
- The third property is scalability.
- We want to make sure that the blockchain
- is still efficient, even if you have lots of users
- and lots of transactions.
- And we all know that no existing cryptocurrencies
- or blockchain platforms can
- satisfy all the three properties.
- So we have talked about the
- scalability issue before,
- so in this module, we mainly will focus
- on the security and privacy issues.
- Now, in fact, we have experienced two stages
- of blockchain already.
- People usually name it Blockchain 1.0
- and also Blockchain 2.0.
- Now, for Blockchain 1.0,
- the blockchain is mainly used for cryptocurrencies
- but then in about 2013,
- Ethereum started to introduce smart contracts.
- Simply speaking, it’s an embedded program
- inside a blockchain that can be executed automatically
- and this marked Blockchain 2.0.
- Now smart contracts basically can enable the developers
- to write new applications on blockchain
- and then at the moment,
- people started to expand blockchain
- into other areas
- such as health care, supply chain,
- charity, journalism, music industry, etc.
- but then on the other hand,
- these smart contracts also introduced a lot
- of security problems.
- In this module, we will try to look
- at the security and privacy issues.
- If we want to take a closer look
- at a real blockchain system,
- we can divide the blockchain system
- into the following modules.
- The first one is the lowest level.
- We usually call it system level.
- It’s about its overall system architecture
- and how you put the transactions into the system.
- It’s about data structures, etc.
- And of course, because we need
- to write the smart contract,
- we need programming languages,
- so the language design will be an issue,
- whether the language design is secure or not.
- So the second module is the programming.
- The third one is the crypto scheme.
- I hope you still remember that blockchain actually uses
- quite a number of cryptographic elements
- in order to make sure that the
- blockchain is secure and safe.
- For example, the public key, private key
- cryptography,
- digital signature as well as the hash functions.
- And on the other hand,
- we also need a trust model
- in order to get a consensus among of users
- because there’s no centralized management,
- so all the decisions will be made
- by all the users in the system,
- so we need a protocol
- or a consensus protocol
- to make the final decisions for the blockchain.
- And finally, of course,
- if the developers are going to
- write different applications,
- then we have an application layer
- which may also introduce security
- and privacy issues.
- Now, based on these five modules
- in a real blockchain system,
- actually the researchers have done a recent survey
- in 2017 – the conclusion is that blockchain
- is not 100% secure
- and is not 100% privacy-preserving.
- Now, they actually located at least nine risks
- inside these blockchain systems.
- We are not going to go over all of them.
- We will try to pick some of them
- so that you can understand the risks
- if you are going to use a blockchain system.
- And these nine risks
- can be mapped into the five modules we talk about.
- In other words, some of the security risks
- are introduced by the system design,
- some by the programming language
- to be used for the smart contracts,
- some are introduced in the applications,
- some are actually introduced
- by using inappropriate crypto schemes
- and some may be introduced in the consensus protocol.
- So we will try to take a closer look
- into some of these risks today.
5.1.2 Limitations of Blockchains (Part 1)
- Now, you probably have heard
- about this 51% vulnerability
- in the internet, but what does it mean?
- Now, before we talk about
- this 51% vulnerability,
- let’s do some review first.
- So I hope you still remember blockchain
- has no single centralized administration,
- so who is going to help to add
- new transactions into the chain
- and how to guarantee
- these chains are valid?
- In fact, if you still remember,
- in the public chain,
- everybody joining the scheme in the network
- is going to decide which new transaction
- is going to be added into the chain
- and how to guarantee the validity of these transactions.
- So, everybody will try to keep a copy of the chain
- and when A has a new transaction,
- he will try to broadcast this transaction to everybody
- and everybody can help to track it.
- In fact, this “everybody”,
- usually, people call them the miners.
- Okay, the miners will have to
- check whether this transaction
- is valid according to the history
- of the blockchain, the transactions,
- and then, try to append this into the chain.
- And of course, the first one who can complete this
- will broadcast the new chain.
- And I hope you still remember
- we do have some chaos, right?
- At the beginning, we assume that every miner
- has the same blockchain, but after a while,
- miner A may append a new block
- and broadcast, but B and C may not get it
- because they are in the network.
- Or for example, miner E, who
- may be an adversary, okay,
- a bad guy, may try to append
- a fake block and broadcast it,
- and D does not know it, may
- work on E’s blockchain.
- So even worse, F may try
- to double spend his money,
- send out two transactions
- giving the same amount of money
- to two different users and broadcast it.
- So in other words, even if we
- start with a correct blockchain
- and eventually, then we might
- have some fake blocks appended
- to the blockchain
- and also, there may be
- some double-spending cases
- in the blockchain.
- Then what we are going to do,
- if you still remember,
- all the miners will try to
- validate all the transactions.
- So a very simple rule that blockchain follows
- is everybody will try to follow the longest chain.
- Now, the rationale behind is
- very simple because we assume
- that the majority of the miners are honest.
- So what does it mean?
- It means that every miner will try to look
- at the transactions
- and they will try to pick the chain
- with the valid transactions there.
- So, therefore, more people will vote on the correct chain
- and the chain will get longer and longer.
- For example, the existing chain
- only has one transaction,
- Tr1, and then, we have a
- correct transaction, Tr2,
- and a fake transaction, Tr2′,
- and most miners will
- check both transactions,
- Tr2 and Tr2′,
- and they will agree that the
- correct chain should produce
- Tr1 to Tr2 instead of Tr1 to Tr2′.
- So in other words, more
- miners will keep the copy
- of the correct chain
- and further work on it, so it
- will become longer and longer.
- And I hope you still remember
- why the miners want to help.
- Because of the incentive.
- So in return, they have
- the blockchain system
- to validate the transactions
- and put the transactions into the blockchain,
- append it to the blockchain.
- Then, he can receive a new coin for himself
- and sometimes, also get the transaction fee
- depending on the owner.
- The validation process only involves
- checking the account balance
- and seeing whether the transaction is valid or not,
- so it can be done very quickly.
- So, in order to make it difficult,
- we are trying to use the Proof of Work concept.
- I hope you still remember this.
- We talked about it in the previous module.
- So what you do is they need
- to solve a difficult problem
- in order to append a new
- transaction to an existing chain.
- Let me summarise the scenario first.
- So if a new transaction is broadcast,
- the miners will try to work on
- the validity of the transactions
- and at the same time, they will spend
- their computational power to solve a problem.
- So, after they solve the problem, get the solution,
- and after the validation process,
- then they can broadcast a new chain with
- the new transaction appended
- to the original chain.
- Now, so in other words, who can control
- which new transactions to be appended to the chain
- actually depends on whether
- he can solve the problem quickly.
- Also it would depend on the majority of the miners
- because they are the ones who
- validate the transactions
- and decide which transaction
- to be appended to the new chain.
- Now, so I hope you now will understand
- what is the 51% vulnerability.
- In other words, the principle
- behind is to go for the majority.
- If you are powerful enough
- to control more than 50%
- of the computational power,
- you are able to control
- more than 50% of the miners,
- then you can control the miners
- to add which transactions to the new blockchain.
- Then you can ensure that your chain is the longest
- and then, you can control how the chains look like.
- And basically, you can append fake transactions,
- double spending transactions into the blockchain,
- and nobody can object this
- because you already control
- over 50% of the miners
- and have more than 50% of
- the computational power.
- So in other words, if you are going to use the blockchain
- with a pure PoW consensus algorithm,
- then you need to be very careful who are the miners
- and whether there’s somebody actually controlling
- more than 50% of the computational power
- and also control more than 50% of the miners.
- Now, I hope you also understand why the throughput
- is not high because we need
- to give the miners some time
- to solve the difficult problems
- and also, we need to wait a
- certain amount of time in order
- to distinguish which blockchain is longer
- in order to take the blockchain
- as the valid blockchain.
- So therefore, you can see that if you use
- a pure PoW consensus algorithm,
- the transaction throughput
- of the design of the blockchain system
- is only about seven or eight
- transactions per second.
- This is also one of the scalability issues
- we need to resolve.
5.1.3 Limitations of Blockchains (Part 2)
- Now I’m going to give you more examples
- why we say that the blockchain system platform
- is not 100% secure.
- Now, my next issue is about the private key security.
- I hope you still remember
- that we are not using our real names
- when we are trying to create an account
- or a wallet in a blockchain.
- So do you still remember what we used
- to create a account or blockchain wallet?
- Basically we are using public keys
- and private keys in order to access the account
- and usually the private key is the key
- in order to access the account.
- Now, if the private key is being stolen,
- your money will be gone
- and there’s no way to trace the money
- because we do not have a centralised management
- to look over all the wallets and the accounts.
- Now, some researchers actually
- discovered a vulnerability
- in a crypto scheme which is called ECDSA.
- They use it in blockchain
- and they find that the private key they generate
- is not random enough.
- So in other words, an attacker has a chance
- to recover a user’s private key.
- Now, once the private key is being recovered,
- the attacker can actually access to the wallet
- and transfer the money to his own account
- and there’s no way to trace
- where the money will be going.
- So this is another example showing that sometimes
- if the developer did not use a correct
- or an appropriate crypto scheme
- in the blockchain system,
- we may also have a security issue there.
- Now, let’s turn to look at the security
- of smart contracts.
- As I mentioned,
- from blockchain 2.0,
- the smart contracts actually enabled developers
- to write a lot of new applications.
- Now, according to a study
- by the Black Hat USA in 2018,
- there are already 1.5 million
- Ethereum smart contracts that
- have been created in the blockchain
- but unfortunately, based on another survey
- by IBM and IIT,
- based on the amount of smart contracts they studied,
- they have indicated that 94.6%
- of the contracts which contain
- cryptocurrencies worth more
- than $0.5 billion are vulnerable.
- In other words,
- these smart contracts are not safe.
- According to a survey,
- they also listed a lot of smart contract securities,
- for example, in particular,
- they have identified some security issues
- on the programming languages
- for smart contracts in Ethereum
- which is called Solidity.
- In other words, people use Solidity
- as a programming language
- to write smart contracts in Ethereum
- but then they find that they require a number
- of security issues there.
- Now, in this module, I’m going
- to tell to you some of them.
- There were also major incidents that happened before.
- Okay, let me just give you some idea
- about what had happened before.
- A DAO attack happened in June 2016.
- DAO actually is a smart contract
- written for crowd funding.
- So people tried to give funding to the projects based
- on this smart contract
- and in fact, it’s very successful.
- In 20 days, they raised about US $150 million.
- However, the attackers exploited the vulnerability
- of Solidity, they found a loophole
- in the programming language of Solidity,
- so they found a security hole in the smart contract
- and about US $16 million was stolen.
- And another major instance
- happened in a Bitcoin exchange
- in March 2014.
- Actually this Bitcoin exchange
- was one of the world’s largest Bitcoin exchanges.
- It handles over 70%
- of all the Bitcoin transactions
- and they also exploited a security hole
- in Bitcoin which is called the transaction mutability.
- And US $450 million Bitcoins were stolen.
- If I remember correctly,
- actually the company went bankrupt
- after this amount of Bitcoins had been stolen.
- Now let me just give you a very, very rough idea
- what the transaction mutability is about.
- It’s very easy to understand.
- I hope you still remember,
- every transaction, for example,
- the details about how much money from which owner
- to give which receiver
- will be digitally signed
- and then usually the transaction ID
- will be the hash of the transactions.
- Now, in earlier implementations
- because it was in 2014,
- there’s no standard for appending data.
- In other words, when they create a hash,
- what they do is they would try to put the content
- of the transaction together with a padding string
- at the end, a 01, a random 01 at the end
- in order to create a hash.
- Now, because this hash is the transaction ID,
- so if the attacker is able to change the padding string,
- then the ID will change
- and then what they are trying to do is they claim
- that the transaction is being lost.
- In fact, the transaction has been transferred
- into their account
- but they changed the padding string
- so the ID changes so the owner
- cannot trace the transaction
- where it has been gone.
- So basically the owner
- will try to issue another transaction again
- and transfer the money again,
- so they try to do this – retry, and retry
- and then transfer the money
- out from a single account.
- So this is basically how they
- could steal 450 million Bitcoins
- from the account.
- So the platform realized this security hole,
- so they fixed it already
- but then on the other hand,
- we still have a lot more security issues
- in smart contracts.
- I wanna give you some more examples,
- so that you can be aware that while using smart contracts,
- one needs to be very careful.
5.1.4 Limitations of Blockchains (Part 3)
- Now the famous one is called
- the under-priced DoS Attack.
- DoS is the Denial-of-Services attack.
- So what they are trying to do is the attacker tries
- to create some smart contract
- in order to slow down the performance
- of the blockchain system.
- Let me give you some basic idea first.
- Now, smart contracts, as we mentioned,
- will enable the developer
- to write programs to be executed
- in the blockchain
- but it doesn’t come for free,
- so in Ethereum, they have a charging scheme.
- So every user, if they want
- to execute a smart contract,
- they need to pay for it
- and then every operation in that smart contract
- will be assigned a certain amount of units
- to be charged.
- Usually they call this gas units in Ethereum
- so the user can specify the price per gas unit
- and the limit and the miner
- who helps to execute the code
- will get the execution fee,
- so that’s why the miner is willing to help
- because they can get the reward
- from helping to execute the smart contracts.
- So the attack idea is very simple.
- They will look for the operations
- that are under priced,
- in other words, you can just pay a little bit amount
- of money or gas units,
- then you can execute the operations
- and then what they do
- is they repeatedly execute these operations
- in order to slow down the operation
- of the whole blockchain.
- Now, there were two real attacks in 2016.
- One is called EXTCODESIZE,
- the other is called SUICIDE.
- Now let me talk about them one by one.
- Now, there’s an attacker,
- they deploy a smart contract
- involving many EXTCODESIZE operations
- and it’s about 50,000 per block
- and then you can imagine
- that because we still need to execute these operations,
- so the clients will spend
- a long time processing these transactions.
- Actually, he try to slow down the whole blockchain
- and the throughput drops quickly at that moment.
- So it becomes a DoS attack.
- The reason is when the designer
- tried to decide the gas cost for this operation,
- they set a very low cost, only 20 units
- but on the other hand,
- this operation involves expensive
- input/output operations.
- So in other words, every node in Ethereum
- will try to maintain the same copy of the blockchain.
- Now, in the old days, they only need
- to download all the transactions
- of the whole blockchain
- but because of a smart contract,
- so if they want to get a copy
- of the whole blockchain,
- what they need to do is they need
- to download all the transactions
- and also download all the smart contracts
- in the blockchain
- and also, execute all the historical transactions
- in order to synchronise the blockchain
- with the other one to which the same state.
- So in other words, for every smart contract
- inside the blockchain,
- the miner has to execute it, all of them
- in order to achieve the same state as the others.
- So if you think about it,
- if you have many of these operations to be executed,
- then you can see that every miner
- has to download a lot of smart contracts
- and try to spend a lot of time in
- executing all the smart contracts before they start to
- validate new transactions to append to the blockchain.
- So that’s why we call it’s a DoS attack.
- It means we try to make the service unavailable
- to the users.
- Now the solution at that moment
- is they’ve realised that this operation,
- the gas cost is too low,
- so what they do is they increase it
- from 20 to 700.
- It’s about like US $.0042
- in order to stop this kind of DoS attack.
- Now another one,
- we usually call it the SUICIDE attack.
- Now, this is very similar.
- The attacker tries to deploy a lot
- of smart contracts and these smart contracts,
- they execute a particular command
- and this command, this operation is called the SUICIDE
- and the SUICIDE command is very simple.
- What they do is they try
- to stop the executable smart contracts
- and try to send the remaining money,
- the Bitcoin or token into the designated account.
- So in other words, SUICIDE means
- that I realize that I need to stop this contract
- and put the remaining balance
- of the money into a designated account.
- Now, in the original design,
- if the SUICIDE cannot find the target account,
- it will create a new one
- and to create a new account is time-consuming
- and the consequence of this attack
- is they find that 19 million of new accounts
- were created for nothing.
- So you can see that it’s the time,
- the disc space also wasted
- and if you look at the reason for this,
- it’s because the original designer set the gas cost
- of this operation to be zero,
- so in other words,
- I can write a smart contract
- with lots of SUICIDE operations
- in it without paying anything
- but then the system has
- to execute this operation
- in order to create new accounts
- and execute the SUICIDE operations.
- Then right now the solution is they try
- to increase the gas cost
- of the operation from zero to 5,000
- and if you need to create a new account,
- you need to pay another 25,000 gas units
- in order to stop this kind of attack.
- Now you can see that there are solutions proposed
- like increasing the gas cost of under-priced operations,
- there are still a lot of possible attacks
- and actually the attacks have been stated
- in one or two survey papers already.
5.1.5 Limitations of Blockchains (Part 4)
- Now so you can see that security
- is an issue in the blockchain platform,
- it’s not a 100% secure system,
- so when we are using blockchain system,
- you need to pay attention to the security issues.
- Now, on the other hand,
- privacy is also an issue.
- Now, I hope you still remember
- that all the transactions in the original design
- of the blockchain are transparent
- meaning that everybody can
- look at all the transactions.
- Now, although we do not use real names
- but people can still look at the details
- of the transactions, for example,
- I can check from which wallet to which wallet,
- how much money has been transferred.
- In fact, people have done analysis
- on this wallet relationship
- and have identified some of the transactions
- and I will talk about this in the next lecture
- but on the other hand,
- then you can see that we cannot expect 100% privacy
- in a blockchain system.
- Now let me elaborate a little bit more.
- Usually we are talking about three types of privacy.
- One is the sender privacy,
- the identity of the sender
- and also the identity of the recipient.
- Of course, we want to hide these two identities.
- We do not want people to know
- who is going to pay money to the other person
- but on the other hand, the amount,
- the information inside a transaction
- should also be kept confidential.
- So we do have another privacy,
- the privacy of the details of the transactions.
- At this moment, none of the existing schemes
- can achieve all three types of privacy
- and at the same time can make the platform scalable.
- So in other words,
- we do not have a perfect system
- that can protect the privacy of the sender,
- the identity of the recipient
- as well as the information inside the transaction
- as well as making the blockchain system scalable.
- Many researchers and practitioners,
- they realized this problem,
- so they started to address this issue.
- Let me give you some examples.
- Zcash, they basically tried
- to leverage a cryptographic technique
- which is called zero knowledge proof
- in order to hide the identity of the sender, recipient,
- as well as the information
- inside a transaction.
- The other cryptocurrency, Monero,
- actually use a linkable ring signature.
- There are many, many others
- but at this moment,
- we will cannot see a blockchain platform
- that can actually achieve all these three types
- of privacy and they are scalable.
- So do not expect 100% privacy protection yet.
- Now I hope I have given you enough examples
- to show that there are security
- and privacy issues in blockchain systems.
- Now although blockchain is a great platform
- with lots of potential and implications,
- but on the other hand,
- I hope people could be aware the security,
- privacy, scalability issues.
- All these issues are not yet completely resolved.
- So in this module, we mainly talk about some
- of the security and privacy issues.
- In the next week,
- we will talk about some evil sides
- of blockchain and Bitcoins.
5.2.1 Risks and Limitations of Blockchain: Privacy (Malcolm Wright from Diginex)
- Today I’m going to discuss two topics
- around the risks and limitations of Blockchain.
- First, I’ll discuss privacy considerations that developers
- and firms that use Blockchain should be aware of.
- I’ll then discuss some key security risks
- and what can be done to mitigate them.
- In the context of privacy then.
- I will use the European Union’s General Data Protection
- regulation, or GDPR, as the baseline for this discussion.
- The GDPR came into effect on
- 25 May 2018 and is generally
- regarded as the benchmark data privacy standard.
- With Blockchain projects often
- spanning different countries,
- it is appropriate to take
- the highest benchmark
- as we consider privacy issues.
- So what do we mean by personal data?
- Personal data means any information relating directly
- or indirectly to a living natural person,
- where it identifies them or makes them identifiable.
- Processing personal data means any operation
- or set of operations performed
- upon the data, for example,
- collection, recording, organisation,
- structuring, storage,
- adaptation and alteration.
- The nature of blockchain
- means that every transaction
- taking place will be published and linked to a public key
- that represents a particular user.
- The public key is encrypted
- to prevent anyone who views
- the blockchain from being
- able to identify the user.
- However, the re-use of the
- public key enables individuals
- to be singled out by
- reference to their public key,
- even if they cannot be directly identified.
- The public key, when associated with an individual,
- will likely qualify as personal data
- for the purposes of the GDPR.
- However, there are some blockchain technologies
- that permit the public key not to be published,
- which may change how we view this.
- When the public key is visible,
- it could be possible to attain information
- that enables an individual to be identified,
- either because it is held by the service provider
- or because somebody is able to connect
- a public key to the individual.
- At that point, all transactions that the relevant
- individual has made are then publicly available.
- So you may ask, can we not just anonymize the data?
- The European Union Working Party on Data Protection
- provided guidance on the difference
- between pseudonymized and anonymized data.
- This distinction is important in relation to blockchain
- as data protection rules do
- not apply to anonymized data;
- as such data cannot be traced
- back to a living individual.
- However, the threshold for data
- to qualify as anonymized is very high.
- Encrypted personal data can often be traced back
- to a person if enough effort is put in by experts
- or someone who holds the key to decryption.
- Therefore, encrypted data will often qualify
- as personal data and not as anonymized data.
- This means that in most instances the privacy rules
- will be applicable to at least some of the data
- involved in blockchain systems.
- Blockchain technology relies on hashing,
- which consists of generating a code of a fixed length
- for a given piece of digital information,
- regardless of its length.
- Hashing is important because
- it permits somebody to verify,
- by recalculating the hash that a given piece
- of information is identical to the digital
- information that was originally hashed.
- A hash cannot be reverse-engineered
- to discover the original information.
- The process only works in one direction,
- from the original document to the hash.
- Yet in spite of this, the European Union Working Party
- on Data Protection stated that hashing
- is a technique of pseudonymisation, not anonymisation.
- According to the working party, it is sufficient
- for a hash to permit records to be linked for a piece
- of information to constitute personal data.
- Therefore, a hash that represents a person’s ID card
- would likely be considered personal data
- even though the hash itself is impossible to reverse
- engineer into the personal information.
- Finally on privacy, one of the design features
- of blockchain architecture is that transaction records
- cannot be changed or deleted.
- The GDPR recognises a right to deletion.
- The broad principle underpinning
- this is the right to enable
- an individual to request the deletion or removal
- of personal data where there is no compelling
- reason for its continued processing.
- Clearly this is at odds with Blockchain architecture
- and it is for this reason that it is advisable
- for personal data to be kept off-chain.
5.2.2 Risks and Limitations of Blockchain: Security (Malcolm Wright from Diginex)
- Moving on to our second topic then.
- Blockchain security.
- Here, I’m going to focus on three areas of risk.
- First, the 51% attack.
- This is where bad actors gain 51%
- of blockchain mining power
- on a particular blockchain network.
- 51% attacks are one of the most recognised
- blockchain security flaws.
- Once 51% of the mining power, or hashrate,
- has been achieved, bad actors
- can reverse transactions
- to perform double-spends
- and prevent other miners
- on the network from confirming blocks.
- A double spend is an attack where a given set
- of coins is spent more than once in a single transaction.
- In 2018, several notable
- cryptocurrencies such as ZenCash,
- Verge, and Ethereum Classic fell victim to 51% attacks.
- The attackers walked away with
- over 20 million US dollars
- due to the blockchain security issue.
- Where a blockchain utilises a Proof-of-Work
- consensus mechanism it will need mitigations in place
- to prevent this type of attack.
- Such mitigations might include being vigilant
- of mining pools on the network,
- implementing merged mining on a blockchain
- with a higher hashrate, or switching
- to a different consensus mechanism.
- The second security issue we’ll cover are software
- or smart contract flaws.
- Most of the larger blockchains such as Bitcoin
- and Ethereum have proven their resilience to attack.
- However, the apps built on top of them are still
- susceptible to bugs as well as malicious coding.
- Last year, software bugs alone in wallets
- and decentralised apps, or dApps,
- led to over 24 million US dollars in damages.
- It is important that any software using blockchain
- undergoes rigorous testing and review.
- This process should include
- independent code reviews,
- penetration testing, and smart contract audits.
- Additionally, any reputable application should have
- redundant security measures in place.
- And finally, private key security.
- If someone’s private key is accessed
- by an unauthorised individual, their transactions are
- no longer considered reliable
- as the encryption can be broken.
- To prevent this, controls should be in place
- to safeguard the private key used to protect
- an individual’s transactions.
- Where a user is holding self-custody of their private key,
- they should ensure that access to it is controlled
- and a strong private key is used to secure it.
- Early in 2019 researchers uncovered
- that a blockchain bandit had made off
- with over $50 million US dollars where they were able
- to guess simple private keys,
- find the associated public key,
- and then clear the address of funds.
- Where the private key is being held by a custodian
- or an exchange, the responsibility is
- then with the custodian or the exchange to ensure
- they have taken appropriate steps
- to secure the private keys.
- One of the weakness that has
- been noted in the past here is
- that the users themselves very often do not know
- what to ask of a third-party custodian or exchange
- to verify that their keys will be held safely.
- This then, is where the industry can help to educate
- and where courses such as this one are important.
5.2.3 The Five Security Risks of Blockchain (Alan Cheung from Hong Kong Applied Science and Technology Research Institute (Astri))
- I think many people have already explained
- the basic concepts of blockchain.
- But still, up to today, many still have concerns about
- the potential issues of blockchain.
- I will spend a little time to share our points of view.
- The first topic is about 51% vulnerability.
- This is caused by the mechanism
- of the block mining consensus operation.
- It happens in public blockchains,
- particularly cryptocurrency,
- when using proof of work consensus
- that requires computation by blockchain node.
- Hackers often stage concerted attack
- by using hardware-assisted miners
- to become the fastest winner in the mining process.
- Since the winning miner can
- build new transaction blocks,
- the hacker will essentially
- take over blockchain operations.
- However, it depends on how easy it is to own
- the majority mining power of
- such a blockchain network.
- The setup costs of miners could be very high
- to achieve this attack.
- For permissioned blockchain,
- the issue could be less of a concern
- because the consensus algorithm is different
- and the participating parties would agree
- on certain legal and governance terms
- and therefore will be better protected
- when operating such a network.
- About private key security.
- As of today, most blockchains
- employ public key cryptography
- for identification.
- It’s usually in a blockchain host private key.
- Ideally, the private key should
- be only known to the user.
- However many cryptocurrency exchanges
- store the private keys of the users in online wallets.
- There have been cases where users’ private keys
- in online wallets has been stolen by hackers.
- And as a result, lots of funds had been stolen.
- The keys in the online wallet must be protected
- with some kind of multifactor authentication
- to avoid being stolen.
- In a permissioned system, however,
- standard IT security guidelines needs to be followed
- to minimise identity fraud.
- Permissioned blockchains also
- use certificates of authority
- to manage certificates of private keys.
- Therefore, user access can be rerouted
- if the keys are stolen.
- About criminal activity.
- Bitcoin, because of its anonymous transaction nature,
- is often used for criminal activities
- such as money laundering,
- blackmailing, and ransomware.
- To deter money laundering,
- some governments require cryptocurrency exchanges
- to collect customer’s personal information
- and contact KYC procedures.
- Permissioned blockchains usually are subject
- to periodical audit to detect illegal activities
- and to comply with regulatory requirements.
- About double spending.
- Professional hackers can exploit
- the infrastructure of blockchain to make it possible
- to double spend the cryptocurrency.
- They can perform so called DDOS attack
- on the blockchains nodes
- and break the blockchain P2P network
- into multiple fragments,
- and then they can spend the cryptocurrency
- on each of the network fragments.
- They can also use hardware mining chips
- in the set of money nodes
- to dictate the transaction in the blockchain.
- There are efforts in the public blockchain platforms
- to make their mining algorithm hardware-resistant.
- While many permissioned blockchains
- do not issue cryptocurrency and
- the money nodes are trusted.
- However, they still need to ensure the network
- has sufficient redundancy to
- prevent network fragmentation.
- About the vulnerabilities in smart contracts.
- Smart contract is a string of blockchain.
- It allows blockchain to execute
- complicated business logic.
- However, a misconstructed smart contract
- can be used by hackers to
- perform destructive operations.
- An example is the Ethereum DAO,
- distributed autonomous organisations smart contract.
- It’s just originally used to allow people
- to fund blockchain projects with their own crypto coins.
- However, there’s a program flaw
- in the initial version of the smart contract.
- An attack on it was staged in June, 2016.
- The attacker managed to retrieve approximately
- 3.6 million Ether from the DAO fund.
- For the permissioned blockchain platform
- they should also take precaution
- to prevent the presence of vulnerabilities
- in the smart contract.
- They should conduct security code scanning
- on smart contracts to remove code susceptible
- to hacker attacks.
- They should also conduct thorough testing
- to avoid misuse of the smart contracts.
5.3.1 Applied Smart Contracts: Opportunities, Risks, and Applications for Enterprise (Jon Rout from Digital Asset)
- Good day, my name is Jon Rout.
- I work for Digital Asset, the creators of DAML,
- an intuitive open-source smart contract language
- that runs across a growing
- number of distributed ledgers.
- Enterprises use DAML to model
- programmable digital assets
- and to automate complex
- multi-party business workflows.
- You can get started programming
- your own smart contracts
- for free at DAML.com.
- By the end of our session today,
- you’ll understand a little bit
- about what smart contracts are,
- the opportunities they bring,
- and the risks that need to
- be considered and managed.
- We’ll review also how DAML smart
- contracts are being applied
- to create real business value around the world.
- Okay, let’s get started with some clear problems.
- Today enterprise infrastructure is siloed,
- as you can see in the graphic here.
- We’ve got a number of different cogs
- representing the different technology stacks
- at each institution,
- and a number of different database types.
- What this represents is that each institution today
- keeps independent and duplicated records
- of the same information.
- Usually they run asynchronous message-based systems
- with large teams of people
- performing manual reconciliation
- in order to keep the data in alignment
- across several different firms.
- This creates a number of challenges.
- Firstly, technology costs are unnecessarily duplicated,
- and upgrades become quite difficult
- when you need to get everybody on the same page
- at the same time.
- Secondly, because every firm
- is using different technologies,
- reflected by the different cogs in the graphic,
- there is inconsistent processing across different firms,
- which creates the need for operational cost
- or manual reconciliation in the first place.
- Thirdly, there’s no real-time shared state.
- There’s no guarantee that what I see is what you see,
- between these companies on the page,
- and this makes coordination quite tricky.
- Finally, a distributed ledger, or blockchain,
- that the smart contracts are running upon,
- guarantees that each firm sees the same information
- at the same time,
- provided, of course, that they’re entitled to do so.
- This solves for the shared state problem
- that we were talking about.
- DAML smart contracts are being used
- to upgrade the post-trade functionality
- offered to all 120 members of the Australian market,
- delivering for the first time
- real-time access to GoldenSource
- clearing and settlement data to members,
- and significant future potential benefits
- to all of the market such as, for example,
- through corporate actions automation,
- or by enabling market places for ASX
- and third-party DAML applications
- that can be leveraged by members of the network
- to rapidly add new functionality
- and create new value for their own customers.
- Okay, so what advantages can smart contracts bring
- to this problem statement?
- Smart contracts are small pieces of executable code
- designed to be shared between different participants
- in a distributed ledger network,
- as you can see in the picture here,
- and they can really help us address
- some of those problems at the very core.
- Firstly, smart contracts reduce
- duplicated technology costs
- by shifting common business logic into shared code
- that can be deployed to all of the firms
- in a distributed network.
- Upgrades also become easier
- as new products and workflows
- can be modelled as smart contracts too
- and deployed to each member’s distributed ledger node,
- much like installing a new app
- or upgrading an old one on your phone.
- Secondly, because we’re now
- leveraging smart shared code
- across all of those participants in the network,
- you can also guarantee consistent processing
- by each of the firms with the necessary implication
- that less manual reconciliation is required
- to keep everybody in sync.
- Third, and finally, our distributed ledger or blockchain
- that sits underneath it all,
- these smart contracts run upon it in such a way
- that you can guarantee that each of the firms
- sees the same information at the same time,
- provided of course that they’re entitled to do so.
- This solves for our shared state problem.
- Importantly, smart contracts don’t need to replace
- the paper contracts that enterprises
- rely so heavily on today to be valuable in the enterprise.
- Really, what they can do is augment
- those existing paper documents
- by creating automatable versions
- that can be shared between different counterparties
- and used to ensure that the downstream processing
- of the agreements that are being made
- is consistent and quick.
- Okay, so smart contracts make a lot of sense,
- but what should our requirements be
- as we choose our smart
- contract programming language,
- before we use it to create
- enterprise grade smart contracts?
- First, our key requirement is
- that we need to be able to model what it means
- to own different types of assets.
- Let’s think about a simple example.
- What does it mean to own a house?
- As an owner, for example, you have the right
- to exclude other people from your property,
- the right to charge a rent to your tenants
- when they occupy the place,
- but you also have the obligation
- to pay property taxes to the government.
- Your ownership then, when you think about it,
- can really be modelled as this bundle
- of rights and obligations that collectively represents
- what it means to own your house.
- This concept is extremely powerful
- and can really be extended to basically any asset class,
- from simple real property
- like the one we’re talking about now,
- to complex derivative products like interest rate swaps.
- Secondly, if we’re thinking about the requirements
- for our smart contract language,
- you need to think about how supply chains work,
- how business workflows work.
- Fundamentally, these are complex processes
- that require sequential
- communication and orchestration
- between multiple different firms
- as they perform different actions in sequence
- to create value for their end customers.
- Successful automation in this space
- means guaranteeing that all firms
- that are participating in a workflow
- are in sync on the order and status
- of the task to be completed by each firm.
- Our smart contract language needs to support this.
- Third, determining which participants,
- customers, or perhaps even regulators
- need to be able to act upon or have visibility
- over contracts, assets, or workflows
- is critically important.
- In the enterprise, it’s never okay
- to share all of the information with everybody,
- even when the network is permissioned,
- so we need to get intelligent here.
- Accordingly, a well-designed smart contract language
- needs to offer developers a simple means
- of defining the participants
- who may enter into agreements,
- the capacity to successfully express
- the bundles of rights and obligations
- like a home ownership that we talked about before
- that allows us to model clearly different asset classes,
- and also to offer built-in access control.
- Fortunately, DAML, the smart contract language
- that we’re learning about today,
- gives you all of these features out of the box.
- Okay, so let’s think about this
- more from a risk lens here.
- Some of you may be more familiar with major bugs
- in the Ethereum distributed ledger,
- such as those in the smart contracts
- that established the distributed
- autonomous organisation,
- or more recently the Parity wallet,
- which have led to tens of millions of dollars of losses
- for people that were affected by those contracts.
- Most importantly, these bugs have shown the world
- the potential cost of bad code in distributed systems.
- Although the impact of bugs
- can be much better mitigated
- in permissioned enterprise DLT networks
- than on public blockchains,
- the potential impact of bugs
- is still higher in distributed networks
- than in isolated infrastructure status quo.
- How can a smart contract language selection
- mitigate this risk, and what are our options?
- As you can see in the graphic,
- general purpose programming languages
- are generally our starting point.
- These are languages like C++, Kotlin, and even Solidity.
- These languages are fully featured
- and enable experienced developers
- to produce sophisticated functionality.
- However, the complexity and lack of safeguards
- inherent in those languages
- means that the risk of unintentionally creating
- high-impact buggy code is quite significant.
- Next in the order of risk
- is functional programming languages.
- This is the family of languages
- that include examples like Haskell and Clojure,
- and they offer the benefit that code
- always returns the same results given the same inputs.
- This makes testing them,
- or testing smart contracts that are written with them,
- easier and lowers risk.
- Lowest risk of all though
- for enterprise smart contract development
- are domain-specific languages that are purpose-built
- to model distributed workflows across firms, like DAML.
- Those languages leverage restriction
- to enhance developer usability
- and reduce the risk of errors,
- kind of like the reason why
- you choose to do maths problems
- on a calculator rather than a laptop.
- Sometimes, usability is enhanced
- by restricting the features that are available.
- It’s really about the right tool for the job.
- Okay, so now we’ve learned a bit about the theory,
- what are some real examples of this technology
- creating true value for the enterprise?
- First, Digital Asset was fortunate to be selected
- in January of 2016
- to partner with the Australian Securities Exchange
- to deliver a DAML-driven replacement
- for the cash equities clearing and settlements system
- known as CHESS.
- This system manages all of the post-trade operations
- for the $2 trillion Australian share market.
- DAML smart contracts are being used
- to upgrade the post-trade functionality
- offered to all of the 120
- members of the Australian market,
- delivering for the first time real-time access
- to GoldenSource clearing and settlement data
- direct from the CSD
- to members and significant future benefits
- through, for example, corporate actions automation
- and also by enabling a marketplace for ASX
- and third-party DAML applications
- that can be leveraged by members of the ASX network
- to rapidly add new functionality
- and create new value for their own customers.
- Second example, right here in Hong Kong in 2018,
- we successfully completed a prototype
- with the Hong Kong stock exchange
- to bring the power of DAML
- to its post-trade allocation and processing platform
- for northbound stock connect trading.
- The solution helps market participants cope
- with the very tight settlement timeframe
- for mainland China A-shares
- by delivering visibility of processing status
- across all of the parties in the network,
- significantly improving workflow
- and accelerating troubleshooting
- when breaks occur.
- We’re excited to continue working with HKX
- as we look to bring those benefits to production.
- A final example, in 2019,
- the International Swaps and Derivatives Association,
- or ISDA,
- announced that they are partnering together
- with Digital Asset
- to build an event specification module in DAML
- to compliment the ISDA common domain model,
- their industry-wide blueprint
- for how derivatives are traded and managed
- across the trade life cycle.
- This is designed to enhance consistency
- and facilitate interoperability
- across firms and platforms.
- In this case, a DAML-driven event specification module
- empowers front-office developers
- to unambiguously construct the life cycle events
- of complex derivative products
- with machine-executable DAML code,
- ensuring consistency across firms
- as the life cycle of a complex
- derivative asset progresses.
- So, what have we learned?
- Smart contracts can offer efficiencies to the enterprise
- as common workflows get mutualized,
- reducing the challenge of upgrades,
- guaranteeing consistent processing across firms,
- and minimising the ongoing operational cost
- of reconciliation.
- Second, because the potential impact of bugs
- in distributed systems can be high,
- it matters which language you choose
- to write your smart contracts in.
- Domain-specific languages like DAML
- use restriction to enhance usability for developers
- and minimise risk by giving
- them the right tool for the job.
- Last, we have explored some real-world applications
- of smart contracts creating real value for the enterprise
- around the world.
5.3.2 Applied Smart Contracts (DAML): Step-by-Step Example (Jon Rout from Digital Asset)
- Okay so enough theory,
- let’s look at a real example smart contract
- written in DAML.
- On the screen now, you can see the DAML code
- for a simple layer use Smart Contract template.
- In DAML, we create templates like this
- to describe the rights and obligations
- created by a particular type
- of digital asset, agreement or workflow.
- These templates can be shared
- by all parties in a network
- and instantiated as needed on
- a shared ledger as contracts.
- There are a couple of key parts to the code here
- and don’t worry it’s not scary.
- Firstly, signatories, these are the parties
- to an agreement who need to sign off
- in order for the contract to be created in the first place.
- This is important because it means
- that with DAML,
- a party can never be required to do something
- without having first agreed to it as a signatory.
- This is quite in keeping with
- common law around the world.
- Observers, the next thing, are the parties
- who receive the notification
- when a contract is changed or modified
- throughout its life-cycle.
- This is particularly useful
- if you need to give visibility to a regulator.
- Work is in done in our contract
- when a choice is exercised by a controller
- as you can see here.
- Our IOU contract has three
- simple choices modelled for us.
- Different controllers in each case.
- The Lender, for example, is the controller
- of the Split Choice which enables them
- to carve up their right to be paid back by a Borrower
- into two different parts.
- The Lender is also the controller of the Transfer Choice
- which give them the capacity to request
- to transfer their right to be repaid by the Borrower
- to a new Lender.
- One bank to another for example,
- who can then choose to accept or reject their request.
- Finally, the Borrower is the controller
- of the Payback Choice,
- which is their right to pay back a portion
- of the amount outstanding on the IOU
- and simultaneously reduce the Lender’s total claim
- to repayment by the amount they’ve just paid back.
- Choices are by default are what we call Consuming
- in our Distributed Ledger,
- after Choice Execution takes place,
- the old contract is archived
- and new contracts are created in its place
- to reflect the new state of the world,
- the new rights and obligations
- of each of our participants.
- Let’s look at how that works in practise
- when our DAML Smart Contract is deployed
- to a Distributed Ledger.
- Let’s assume for starters that
- a loan has been established
- and our Borrower needs to
- pay $100 back to Lender One.
- First, our Borrower exercises her right
- to pay back $30 of the $100 outstanding on her loan.
- In a single atomic transaction
- on our Distributed Ledger,
- the old IOU Smart Contract is archived,
- a new IOU Smart Contract
- with a balance outstanding of
- $70 is created in its place.
- The cash contract representing
- the borrowed $100 is archived
- and two new cash contracts are created
- to represent the remaining $70 holding,
- now owned by the Borrower,
- and the $30 holding now owned by Lender One,
- having been repaid.
- Next, Lender One exercised their right
- to request a transfer of the outstanding IOU contract
- to another lender.
- One bank transfers it to another.
- Let’s call them Lender Two.
- This results in the old IOU
- contract getting archived
- and a transfer request to Lender Two
- being created in its place
- to represent the latest state of the world.
- This is important, this proposed Accept Workflow
- cause it means you can’t force
- Lender Two to accept this.
- Lender Two can choose to accept this request
- and if they do, it results in the creation
- of a new IOU contract
- that represents the real-world obligation
- that the Borrower now has to pay back
- the remaining $70 to Lender Two
- instead of the original Lender One.
- Our Borrower can now exercise her right
- to repay the outstanding $70 loan
- to Lender Two in partial repayments
- of $30 and $40, respectively.
- Each of these repayments results
- in a transaction to the Ledger
- that includes the archival of the current IOU contract,
- the archival of the contract
- representing the Borrower’s current cash holdings
- before the repayment is made,
- the creation of a new contract
- representing the cash holding
- now owned by Lender Two
- after they’ve been repaid.
- At the end, you can see
- that there are no active IOU contracts
- on the Ledger anymore
- as our Borrower has fulfilled their obligations to pay.
- Lender One has an active cash contract
- representing the $30 that was repaid to them
- by the Borrower;
- while, Lender Two has two active cash contracts
- representing the 30 and $40
- repaid to them by the borrower.
- This is a simple example of a Smart Contract in practise
- and I hope you can see they’re not too scary
- and can be quite useful as
- we automate complex workflows
- amongst multiple different parties.
5.4.1 Use Case: Blockchain for Health Insurance (Alan Cheung from Hong Kong Applied Science and Technology Research Institute (Astri))
- Hello everyone, I’m Alan Cheung.
- I’m from the Hong Kong Applied Science Technology
- Research Institute,
- the largest government-owned
- R&D centre in Hong Kong.
- Today I’m honored to share with you
- our experiences in blockchain.
- ASTRI has been involved in research and development
- of blockchain technology for the past few years.
- We have developed innovative technology
- and commercial solutions for blockchain systems.
- Examples include, blockchain scalability
- and performance enhancement,
- cross system smart contracts,
- and also hardware accelerator for mining
- and processing transactions, etc.
- In the past we have also collaborated
- with the Hong Kong Monetary Authority
- to publish technology white papers
- and completed a few blockchain projects,
- related to financial industries.
- One of the mandates of ASTRI
- is to commercialise our technology,
- especially in Hong Kong.
- In the past few years,
- we have been developing blockchain applications
- with our clients from different industry areas.
- I would like to illustrate one use case today,
- the medical insurance claim blockchain,
- and talk about how to make use of the technology
- and help our clients to solve their problem.
- Traditionally, a patient submits a medical invoice
- which is issued by the clinic
- to the insurance company after a visit.
- The submission can be done in one of the two ways,
- one of them is patients can send hard copies
- of the invoice to the insurance company.
- Some insurance company also accept patient
- to scan copies of the invoice
- and submit through web services or apps.
- The insurance company processes the claim
- and reimburses the patients if approved.
- Usually the clinic and doctors
- are not involved in the claim process.
- So what are the problems and challenges?
- A lot of paperwork is involved
- in handling received hard copies
- or even soft copies of the invoices.
- There’s also a lot of human processing
- which is expensive and error prone.
- The claim process is susceptible
- to insurance fraud such as double claim.
- In the double claim,
- a patient sends soft copies of the same invoice
- to multiple insurance companies
- to get more reimbursements than he should.
- Since the insurance companies process
- the received claims independently,
- it is difficult for them
- to detect such a double claim fraud.
- So why does the customer want to use blockchain?
- Because it allows insurance companies
- to share in this trusted platform
- in processing claims on blockchain.
- It allows them to see if an
- invoice has already been claimed
- through other insurance companies,
- and therefore blockchain helps
- to prevent double claim fraud.
- It would also reduce paperwork.
- Clinics can save information
- of the invoices in blockchain
- and the invoice information can be seen
- by respective insurance companies
- who the provided patient has granted permission.
- It also streamlines the claim operation.
- Blockchain smart contract controls the process
- of filing and processing medical claims
- and the system can release invoice information
- to insurance companies
- as soon as the patient grants
- the permission to the company.
- Blockchain systems can also
- update the patients with the status
- of his claim, approval or rejection status
- as soon as the insurance company has issued them.
- So the scope of the system is as follows,
- the system connects all three user groups,
- including the medical service providers,
- such as doctors and clinics, patients,
- and insurance companies.
- And how it works?
- After providing the medical service to the patient,
- the clinic will submit the invoice’s information
- to the blockchain.
- The patient will file the claim
- to the respective insurance company
- through blockchain as well.
- The patient then grants permission to the company
- to view the clinic invoice.
- The target insurance company will examine
- the patient claim information
- and the clinic invoice information in the system.
- It will also examine the records
- to see if the patient has already filed a claim
- to another insurance company
- to avoid double claim.
- After the insurance company has decided to accept
- or reject the claim,
- it will store its decision to blockchain,
- and the decision will also be
- seen by the patient as well.
- So what are the technical
- and business challenges?
- Nowadays, some clinics
- are still operating without computers,
- not to mention some advanced clinic software,
- and also the connection
- to legacy payment system,
- may not be as straightforward as we think.
- It also takes time to understand
- the data privacy protection requirements
- and also the business logic
- in order to develop a workable
- system for this industry.
- So what have we learned?
- It takes time for users to
- adopt to new technologies,
- therefore, working with a client
- that already has a group of clinics
- and also willing to try blockchain in mind
- would be very beneficial.
- Also, interoperability between
- blockchain and legacy systems
- is an important part of the
- widespread use of blockchain
- in corporate settings.
5.4.2 Use Case: Blockchain & PropTech (Alan Cheung from Hong Kong Applied Science and Technology Research Institute (Astri))
- We are going to illustrate another interesting use case
- in the so-called proptech industry:
- the property sales blockchain.
- The sales of new residential flats or properties
- is a process that involves not only the purchaser
- and property developer,
- but also the solicitor who processes the legal matters
- and purchase payments.
- Also, it may include the mortgage lenders
- who process the purchaser’s application for mortgage.
- Traditionally, the purchaser signs a so-called PASP,
- preliminary agreement for sale and purchase,
- with the property developer
- when they want to buy a flat.
- The agreement specifies the property information,
- purchaser’s personal information, the price,
- the payment terms, and also available rebates.
- The developer sends piles of legal papers and
- agreements to the solicitor through courier services.
- After receiving the materials,
- the solicitor handles and
- processes the paper documents
- and keeps track of the purchaser’s required payments
- prior to signing the official contract.
- Within a fixed number of days,
- the purchaser must fully pay the preliminary payments
- and sign the formal agreement,
- otherwise the sale may be deemed as forfeited.
- The solicitor sends the process
- status to the real estate developer
- periodically about the purchaser payment status
- and also the purchaser’s signing
- of the formal agreements.
- The purchaser may apply for mortgage
- applications independently
- to different banks.
- Individual banks advise the purchaser
- that the application has been approved,
- and the purchaser will inform the solicitor
- of his mortgage application status as well.
- The solicitor will contact the bank
- to release the fund to pay the developer.
- The solicitor and the developer will complete the sales
- once all the payments and legal
- matters have been settled.
- So what are the problems and challenges?
- There are a lot of paper forms that
- need to be sent to the solicitor.
- Also, the developer gets updated on
- the purchaser’s payment status
- only periodically, but not in real time.
- Sometimes, it needs human processing of data
- before synchronisation can be done.
- The solicitor needs to spend quite a lot of effort
- in processing mortgage matter as well.
- The buyer, on the other hand,
- often spends a lot of time
- checking with the developer, the solicitor,
- about the status.
- He may also try to shop for the best mortgage offer
- from different banks,
- either by making a lot of trips to different banks
- or making a lot of phone calls.
- Not to mention, he also needs to bring
- a lot of personal and purchase documents
- to all of the banks.
- To summarize: it is very tedious for all of the parties,
- and this process has been lasting for a long time.
- So why do the customers want to use this blockchain?
- First of all, the developer wants to remove the delay
- caused by physical transfer of paper forms
- to the solicitor through courier service.
- Also, the sale and purchase information can
- be safely stored in blockchain and read by the solicitor.
- Standard copies of legal documents
- can be stored in a system as well,
- by the means of the fingerprints
- of these legal documents
- would be stored in the blockchain
- to certify the authenticity of these documents.
- The developer wants to gain up-to-the-minute status
- of the purchase information.
- Instead of receiving a status from the solicitor
- in a less-frequent basis,
- the developer now will be able to see the status
- once the solicitor has added the status to the system.
- A blockchain system enables purchasers, solicitors,
- and mortgage lenders to work closely
- in processing the application and release of mortgage
- in a trusted platform.
- The solicitor can also see
- all the outstanding mortgage
- applications of the purchaser.
- Once the mortgage lender approves the application,
- it will be immediately seen by the solicitor,
- who can then proceed to arrange for a fund release.
- So the scope of the blockchain system includes
- all of the parties, including the property developer,
- solicitor, mortgage lender, purchasers,
- are all connected in blockchain.
- Information updated to the blockchain
- is immediately seen by relevant parties.
- Some of the relevant documents,
- whether digital or scanned,
- may be stored in the accompanied off-chain storage,
- while their digital fingerprints
- can be stored in blockchain for proof.
- The system enforces strict access control
- such that each purchase is
- assigned to one solicitor only.
- Only this solicitor can access
- the information of the purchase.
- Also, no mortgage lender can access
- the information of the sales
- until the purchaser has granted them permission.
- What are the technical and business challenges
- in this system?
- Since the system involves different user groups
- who have different business practices
- and operation preferences,
- it takes significant amounts of effort
- to design such a system
- to meet the needs of each user group.
- The storage of certain personal information
- has to conform to legal requirements,
- that those information has to be erased
- after a certain length of time.
- So what have we learned in this system?
- We need to work the overall system
- to comply with the legal requirements,
- such as data privacy protection
- and personal information storage.
- Smart contracts need to be
- designed in a very flexible way,
- such that it could adapt to the future changes
- in the purchase flow and different
- access control scenarios.
- We hope in the future that all parties will enjoy
- to use the new blockchain system
- and have much better user experiences.
5.4.3 What Are the Benefits of Blockchain in Banking? (Johnny Cheung, General Counsel, B.C. Technology Group)
- Hello, my name is Johnny Cheung
- and I’m the Group General Counsel
- of BC Technology Group.
- Today I’ll be sharing with you
- various applications of blockchain.
- Blockchain technology is still in its infancy
- but it has already disrupted different industries
- and sectors.
- This technology revolution can be compared
- with the evolution of the use of the internet,
- which has altered the way we live
- in the past couple of decades.
- There are actually numerous examples
- or applications of use of blockchain.
- To name a few in finance, healthcare, media,
- government, and real estate.
- But let’s spend more time to discuss
- the use of it in the banking and finance sector
- as well as the healthcare sectors,
- to illustrate our points.
- In the banking sector, blockchain holds the potential
- to transform the industry
- by reducing potential costs
- and labour savings.
- Talking specifically about the
- banking and finance sectors,
- hundreds and thousands of funds are being
- regularly transferred from one part of the world
- to another every day.
- Traditionally, it operates on the basis
- of highly dependent manual networks.
- As a result, the banking and finance sector
- is prone to errors and frauds that could lead
- to a crippled money-managed system.
- Blockchain provides a very high level
- of safety and security when
- it comes to exchanging data,
- information, and money.
- It allows users to take advantage
- of the transparent network infrastructure,
- along with the low operation costs
- with the help of decentralization.
- A centralized database for
- operations and money management
- traditionally is vulnerable and highly prone
- to cyber attacks as the single point of failure.
- And such a system can be exploited by hackers.
- For example, in early 2017, there was a series
- of attacks on card processing in Eastern Europe.
- The criminals penetrated the banks’ infrastructure,
- obtained access to the card processing systems,
- and increased overdraft limits.
- They also disabled anti-fraud systems
- that would notify the bank of fraudulent transactions.
- In each case, the average theft amount
- was about five million and in total
- about 100 million was lost in these series of attacks.
- In another case,
- while banks in Nepal were closed for holidays,
- criminals used SWIFT to withdraw money.
- The bank were able to track transactions
- and recover significant portion
- of the stolen money funds only due to timely response.
- With the use of the blockchain platform
- is secure, non corruptible technology
- can be operated on a distributed database system.
- Since the blockchain is distributed,
- there is no chance of a single point of failure.
- Each transaction is store in the form of a block,
- either with a cryptographic mechanism
- which is extremely difficult to corrupt.
- With a good and secure blockchain platform
- we can easily eliminate cyber crimes
- in attacks of banking and financial sectors
- taking place now.
5.4.4 How Can Blockchain Technology Benefit the Healthcare Industry? (Johnny Cheung, General Counsel, B.C. Technology Group)
- In addition to the banking
- and finance sector, blockchain technology has also
- impacted the healthcare sector.
- Critical patients’ data
- and information remains scattered across
- different departments and systems.
- Due to this inefficiency, crucial data is sometimes
- not accessible in times of need.
- The current healthcare ecosystem cannot
- be considered complete,
- as multiple players in the system
- do not have a system in place
- for smooth process management.
- Many healthcare facilities today are still dependent
- on outdated system for keeping records for patients.
- These systems hold the functionality
- of keeping local records of the patients’ data.
- This can sometimes make it
- difficult for doctors to diagnose,
- which is time consuming for the doctor
- and hard for the patient as well.
- Another time consuming
- and tedious process that results in high costs
- in the industry is health information exchange.
- Since patients do not have any
- control over their health data,
- the chances of identity thefts, financial data crimes,
- and spamming are increasing every day.
- Because of the problem we just discuss,
- the healthcare system is crying out for a system
- that is smooth, transparent, economically efficient,
- and easily operable.
- Blockchain has the power to bring out
- a great breakthrough in the ecosystem
- and it can easily bring changes
- in the healthcare management of the patients.
- With the aid of this technology,
- patients will now be responsible
- for handling their own records,
- therefore, getting the overall control of their own data.
- Blockchain holds the ability to successfully improve
- patient care quality, while maintaining
- the funds at a very reasonable rate.
- For example, in the 1970s, a system called
- electronic health records, or EHRs,
- were implemented for billing purposes
- and have not been updated since that time.
- While being an important tool for doctors
- to track patients’ medical records, past prescriptions,
- and test results, the lack of standard
- health record parameters
- and security threats can make the EHR management
- a difficult process.
- Blockchain platforms can be used to consolidate
- patients’ information from various sources.
- These newly integrated patient
- records can be visualised
- through easy-to-follow, informative,
- and standardised portals or apps
- for better treatment, improved traceability and security,
- and higher quality of health outcomes.
- MIT has developed a decentralised record network,
- called MedRec, for managing
- electronic medical records.
- Google’s DeepMind initiative is collaborating
- with the UK’s National Health Service to build
- a private platform for secure tracking
- of patients’ health data.
- All the previous challenges
- and hindrance that occur in layers
- of authentication can now be eliminated.
- The vision for blockchain to disrupt
- the healthcare sector is there.
- Just imagine a healthcare
- system where all the information
- is easily accessible by doctors,
- patients, and pharmacists, at any time.
- Blockchain allows the creation
- and sharing of a single common database
- of health information at a much lower cost.
- This database would be easily
- accessible by all the parties
- involved in the ecosystem,
- no matter which electronic medical system they use.
- It offers higher security
- and transparency while allowing
- doctors to find more time
- to spend on patient care and their treatment.
- It also allows better sharing of statistics
- of research on medical data.
- That would have the effect to facilitate clinical trials
- and treatments, therapies, and improve our health.
- Indeed, this is so powerful
- and have great positive impact
- to the whole healthcare system.
- End of transcript. Skip to the start.
5.4.5 Institutional Investment Opportunities in the Digital Asset Space (Henri Arslanian from PwC)
- Hi there.
- Very excited to be here.
- As most of you know, my name is Henri Arslanian.
- My passion and my focus in life
- is the future of the financial service industry.
- I’m very excited to share with you all
- over the next couple minutes some of the trends
- that we’re seeing with institutional investors
- and digital assets.
- I want you to take home
- six big trends that we’re seeing.
- One is the entry of institutional players, stable coins,
- large technology firms coming into digital assets,
- central banks, crypto funds, security tokens,
- and I’ll finish with blockchain,
- so a lot of space to cover.
- Hang on tight, and let’s kick it off.
- First of all is the entry of institutional players.
- Make no mistake, a couple of years ago,
- Bitcoin and blockchain
- developments were happening a lot
- by real, two guys and a T-shirt in San Francisco
- or in a basement in Moscow
- or in a café in Sydney.
- But now, over the last one or two years,
- we’re seeing a lot of the developments take place
- in the broader digital asset space
- being driven by institutional players.
- That has been very, very interesting
- because many of you have been saying
- that as banks and large financial institutions
- are getting into the digital assets space,
- it could be a game changer.
- But that’s not easy.
- Trust me, for someone who’s worked with banks
- and with fintech for many years, it’s very difficult
- to plug in fintech inside a bank.
- Imagine trying to plug in crypto or digital assets.
- It’s even more complicated.
- There’s a lot of issue, like a lack of expertise,
- the reputational risk, the uncertainty.
- I always tell everybody that if you want to get involved,
- if you want to go on Friday
- afternoon and enjoy your weekend
- and have a good time, you should not get involved
- in digital assets because
- the space moves so fast,
- it’s 24/7, and crypto markets never, never sleep.
- But really, we’ve been seeing
- globally three big approaches
- when it comes to traditional financial institutions
- approaching digital assets.
- The first one has been firms
- purely investing in companies.
- Firms like Goldman Sachs, for example,
- have invested in firms like Circle or BitGo,
- investing as a way to learn about the ecosystem.
- Another type of company have been those
- who have been trying to do partnership
- with digital assets companies.
- One example is Nomura
- that has done a partnership with Ledger.
- Again, Nomura has traditional clients.
- Ledger is a French digital crypto custody solution,
- a security company.
- Actually they partnered towards a service to market.
- So that’s second category.
- Third category are companies
- that are setting up new entities
- purely focused on digital assets.
- A great example of that is Fidelity in the U.S.
- where they set up a complete new entity
- to entirely deal with digital assets.
- And it’s been very interesting what’s been happening
- right now when it comes to traditional
- financial institutions, but watch this space
- it’s increasingly likely that we’re going to see
- even more financial institutions enter the space.
- Second big development are stable coins.
- I mean think about this: if today I send you a Bitcoin,
- first you’ll be very happy, but the problem
- is you actually don’t know what the value
- is gonna be one day, one week, one month from now.
- It’s not a very stable store of value so far.
- This is why we’ve been seeing a lot of interest
- increasingly on stable coins.
- What is a stable coin?
- It’s a crypto asset that is backed one to one
- by U.S. dollar or other fiat currencies.
- This ensures that if I send you a stable coin equivalent
- of $1 you’re going to have $1 one week, one month,
- or one year from now as well.
- This has been very interesting for institutional players
- because for let’s say who people are trading crypto
- at the institutional level,
- whenever the markets are choppy
- or it becomes very volatile instead of selling
- all their Bitcoin and moving
- to cash, they can simply
- go and keep it into a stable
- coins which they remain
- in the digital assets space,
- but they can have something
- that is stable until they want to come back
- and actually trade actively.
- But also, the other big development
- has been financial institutions
- looking at using stable coins.
- For example think about all the different
- inter-bank transfers that we have.
- From transfers the bank is doing with the central bank,
- or actually all the different transactions
- that happen between banks on daily basis.
- This is actually quite not only cumbersome,
- but they also operate in the
- same way for many decades.
- And this is the interesting thing is now
- enough financial institutions are looking how they can
- potentially leverage this technology themselves.
- For example JP Morgan recently
- announced the JPM coin,
- which says basically that if a customer
- gives them a dollar they can issue them one JPM coin.
- And then between clients of JP Morgan
- they can transfer those JPM coins,
- basically completely bypassing this existing
- traditional rails that exist that are cumbersome
- and a bit slow and costly in many regards.
- But the other big development,
- the third big development,
- you need to know about is what’s happening
- with large technology firms.
- Because while a lot of startups
- in the last couple months have been pushing innovation,
- have been bringing forward new innovation
- to the broader blockchain space,
- the big game changer could be large technology firms.
- Companies that people trust, people are familiar with,
- and also companies that people generally believe
- that will be here for next couple years.
- Think about a firm like Amazon, that has over dozens
- of millions of Amazon Prime members in the U.S.
- You know if you buy all your
- daily necessities on Amazon,
- wouldn’t you maybe use them
- as a digital currency as well?
- What if Amazon gave you Amazon coin
- that gets you for example
- discount on your next purchase?
- But also if everybody trusted that
- Amazon will be here in couple
- years, maybe we can use an
- Amazon coin on a daily basis.
- Well, the best example of this
- happened literally recently
- last week in early June when
- Facebook announced the creation
- of something called Libra, their
- own global crypto currency.
- Which is very very interesting.
- Just think about it.
- Facebook has over two billion users.
- Think about how many times
- you use your WhatsApp,
- your Facebook messenger,
- or your Facebook app on a daily basis.
- You trust Facebook.
- I mean often you put pictures of your kids
- or your parties on Facebook or on Instagram.
- Now imagine now if Facebook brings together
- a lot of these organisations and there’s a currency,
- in their case Libra, which is backed by a basket
- of different global assets held at tier one custodians.
- And if people can send each
- other these Facebook Libra coins
- think about your domestic helper in Hong Kong
- that wants to send money back to the Philippines
- who can do it now instantaneously at no cost
- and the person receiving it will get it on its app,
- on a WhatsApp instantaneously.
- Or think about the Bangladeshi worker working in Dubai
- who wants to send money
- back home who now can do it
- without avoiding those intermediaries who previously
- have been in business a long time and can do it directly.
- And this opens a whole new
- world of opportunities as well.
- From micro payments to actually getting other
- more peer to peer emergent solutions
- very very exciting development to watch out.
- This is very relevant to central bank crypto currencies.
- Because the big question is,
- while for a lot of central banks
- what is happening with Bitcoin is still quite marginal.
- There may be a hundred million
- or so Bitcoin trading a day,
- but that’s peanuts compared
- to the volume of transactions
- happening in existing financial systems today.
- But actually, also a lot of startups
- do not challenge the authority of a central bank today.
- But what if, with Facebook for
- example, and their new coin?
- Technically with two billion users
- Facebook could be the biggest
- central bank in the world.
- And this is why it is gonna be very interesting
- how central banks are going to
- react over the coming months,
- so watch out for some potential developments
- from that perspective.
- For example one big debate is whether a central bank
- is going to issue its own central bank digital currency.
- Well, there’s been some tries on that.
- Many countries from the
- Marshall Islands to others
- have been trying to promote this idea.
- Why don’t they issue their own digital currency?
- But actually there’s a bit of reticence as well
- from many of the central banks as well.
- For example the European Central Bank recently said
- that while that could be a good idea, it may not be ideal
- because the risk for population is that people
- take their money away from banks and actually come
- and buy digital currencies issued by the central bank.
- And this may create financial stability,
- a rise of interest rates, and potentially
- some issues with the traditional banks.
- This is definitely an area to watch,
- especially with some of the recent developments
- happening with large technology firms.
- Another big development is the rise of crypto funds.
- This is really interesting when you look at how
- institutional players are entering the crypto space.
- If you go back in time to the 1990s, in the early 1990s
- venture capital firms, hedge funds, private equity firms
- were really becoming more mainstream.
- What has happened though, at a time,
- a lot of the institutional investors they start investing
- in these VC funds, hedge funds, P funds,
- and they started to learn about the sector.
- And then over the next 10, 15, 20 years
- they started bringing these skills in house.
- For example today, some of the big pension funds they
- operate like their own private equity funds internally.
- And the same may happen with crypto hedge funds.
- Today the industry is really at its early days
- when it comes to crypto hedge funds, but really expect
- that a lot of the first moves that institutional investors
- may do in digital assets may happen via crypto funds
- where they could put some money, watch,
- learn how the industry operates,
- and gradually, gradually, gradually they can actually
- learn it and be more active in the space.
- Another big development going
- on has been security tokens
- and this is very exciting.
- Because imagine today maybe if I live in a big building
- I can not afford to buy the big building myself.
- In many cities these big buildings
- cost couple hundred millions or a couple billion dollars.
- But now, imagine, if I could buy
- a little tranche of this building.
- I could buy lets say for a thousand dollars
- or even a hundred dollars of this big building.
- What that enables me is that
- I’m able to get some liquidity,
- because today a big building
- only couple people can buy it.
- But if I’m able to separate into little, little pieces
- that enables actually more people
- to actually be able to afford this asset.
- But what’s even more interesting now we’re able
- with security tokens to completely streamline
- what we call corporate actions.
- Today the way we pay a dividend for example
- it happens every quarter or
- every six months or every year,
- and it’s a very cumbersome process.
- And also it’s hard to even
- know who your shareholders are.
- It’s still a challenge for many public large companies.
- With security tokens I can know at all times
- who my shareholders are, and if I want to make
- a corporate action, a dividend payment for example,
- I can make it instantaneously in a matter of seconds.
- So this is an area where a lot of institutional players
- are also taking a look at.
- A lot of them are exploring the space
- and thinking and wondering can this generally change
- financial services as we know today?
- We’re still at the very early days and there’s still a lot
- of work to be done but we’ve seen in the recent months
- people actually tokenize buildings in New York,
- some projects in Latin America, so really a lot
- of interesting things coming ahead in this space as well.
5.5.1 Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 1) (Brian Tang from Asia Capital Markets Institute (ACMI))
- When Facebook announced its Libra initiative
- in June 18, 2019, it reflected a dramatic new stage
- in the evolution of the use of blockchain
- and distributed ledger, or DLT, its governance,
- and potential regulation.
- My name is Brian Tang.
- I’m the founder and managing director of ACMI,
- which fosters capital markets professionalism,
- including with respect to online capital marketplaces.
- I’m also the founding executive director
- of LITE Lab@HKU, that promotes
- law, innovation, technology,
- and entrepreneurship at Hong Kong University’s
- Faculty of Law in conjunction
- with the Department of Computer Science.
- To better understand Libra, one would benefit
- from a greater appreciation of three influences
- that appear significant to its creation
- and design, namely Tencent’s WeChat, Bitcoin,
- and Hedera’s Hashgraph.
- Most of the Silicon Valley internet companies that arose
- in the aftermath of the dot-com
- boom were primarily driven
- by advertising or eyeballs business models.
- With venture capitalist funding often forcing focus
- on rapid growth over short-term revenue or profit,
- many of these business models that were built around
- personal data being mined, used,
- and sold have led to the privacy issues witnessed today.
- In China, unlike the West, credit
- and debit card penetration remains relatively low,
- and pioneering internet companies often incorporated
- transactions, even small ones,
- into their business models
- that led them to become fintechs much earlier.
- For example, online payment
- and escrow system, Alipay, was launched
- by e-commerce platform Alibaba in 2004
- and started with providing prepaid payment services
- by Alibaba’s consumer-to-consumer,
- or C2C, platform, Taobao,
- and business-to-consumer, or B2C, platform, Tmall,
- and then, to more than 460,000 online
- and local Chinese businesses.
- In 2013, Alipay overtook PayPal,
- then owned by C2C platform,
- eBay, as the world’s largest mobile payment platform.
- To incentivize customers
- and suppliers to keep or add more renminbi
- into its mobile ecosystem,
- Alipay offered to pay them
- interest through Yuebao, or leftover treasures,
- that same year, which within a few years,
- became the world’s largest money market fund.
- In January 2011, messaging service, WeChat, or Weixin,
- was launched by Hong Kong-listed
- and Shenzhen-based company, Tencent.
- In what Alibaba’s founder Jack Ma called
- a Pearl Harbour attack, WeChat introduced
- its Red Packets, or Hongbao feature,
- during the 2014 CCTV Spring Festival Gala,
- the most watched television event show in the country,
- with a promotion where users were incentivized
- to shake their phones to receive prizes
- of digitally transmitted traditional gift money.
- Wall Street Journal reported that 16 million transfers
- were made in 24 hours
- and within a month, WeChat Pay’s user base
- expanded from 30 million to 100 million.
- WeChat was also prescient in popularising the use
- of phone-scannable QR codes that allowed offline
- transactions to be made without
- physical wallets or cash.
- According to Statistica, WeChat has 1.112 billion
- monthly active users in Q1 2019.
- This user base is more than
- the population of Europe and Russia combined
- and is only behind Facebook, WhatsApp,
- Facebook Messenger, and Google’s YouTube.
- According to CAICT WeChat
- Economic and Impact Report 2018,
- WeChat drove 333.9 billion renminbi
- or approximately 48.5 billion
- U.S. dollars in home services,
- entertainment, and travel services in 2017.
- TechNode reports that WeChat
- can now handle transactions
- in 13 different currencies in 25 countries and regions.
- And in 2018, 688 million people
- used WeChat Red Packet during Chinese New Year Eve.
- Unlike at banks, all of these transfers
- are free to customers, other
- than a 0.1% withdrawal fee
- when funds are transferred from
- the customer’s WeChat wallet
- to his or her bank account.
- At Berkshire Hathaway’s celebrated
- annual shareholders meeting in 2018,
- Charlie Munger specifically called out WeChat
- as a competitor to watch for against
- credit card company giants
- American Express, Visa, and Mastercard.
5.5.2 Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 2) (Brian Tang from Asia Capital Markets Institute (ACMI))
- In 2009, the famous white paper on bitcoin,
- A Peer-to-Peer Electronic Cash System
- by Satoshi Nakamoto, was released.
- To solve the double-spending problem
- to create a digital currency, the white paper proposed
- an open-source blockchain of distributed ledgers
- where transactions are verified
- by proof of work or mining by peer-to-peer nodes.
- The Ethereum protocol that went live in 2015
- added smart contract elements to the blockchain
- that enabled fundraising for
- projects through token sales
- and the launch of initial coin offerings, or ICOs.
- In addition to anti-money laundering, or AML,
- and counter-terrorist financing, or CFT, concerns
- about illicit transfer of funds,
- ICOs have resulted in fraud, misselling and
- and unauthorised offerings of securities
- and currency outflows.
- Globally, regulators worldwide
- have had a mixed reception
- regarding cryptocurrencies, with some countries,
- such as China and India, effectively banning them.
- However, global convergence of views
- of some regulatory aspects are emerging.
- In June 2019, the Financial Action Task Force, or FATF,
- adopted and released an interpretative note
- and guidance for the regulation
- of virtual asset service providers, or VASPs,
- for AML and CFT purposes, and these apply worldwide.
- In the meantime, many public blockchain
- and DLT use cases are being piloted,
- ranging from sovereign self-identity, or SSI frameworks,
- to the creation of non-fungible tokens, or NFTs,
- as well as security tokens to represent
- different traditional illiquid asset classes,
- such as real estate and art.
- However, to date, adoption of blockchain-distributed
- applications, or dapps, has not fully lived up
- to expectations, with the most used dapps
- relating to gambling.
- At the same time, non-public or permissioned
- blockchain projects for enterprises,
- which do not involve cryptocurrencies,
- such as from R3’s Corda
- and IBM’s Hyperledger consortiums,
- are being piloted across multiple jurisdictions.
- These include at least five
- trade finance blockchain consortia.
- To address concerns regarding trading volatility
- and the lack of asset-backing of cryptocurrencies,
- stable coins have recently
- been developed that are backed
- by a collateral of certain main currencies,
- such as the U.S. dollar.
- However, the adequacy of
- and custody arrangements regarding
- many of the stable coins have been the subject
- to inquiry and in some cases, litigation.
- In October 2018, the Financial Stability Board, or FSB,
- concluded, “Based on the available information,
- crypto-assets do not pose a material risk
- to global financial stability at this time.
- However, vigilant monitoring is needed
- in light of the speed of market developments.”
5.5.3 Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 3) (Brian Tang from Asia Capital Markets Institute (ACMI))
- As previously mentioned, many other DLTs
- have also emerged, with an
- increasing number seeking
- to provide enterprise-grade solutions.
- Announced in March 2018,
- Hedera’s Hashgraph is a proof-of-stake directed
- acrylic graph, or DAG, based on gossip protocol
- and a virtual voting mechanism,
- with impressive claims
- that is able to be thousands of times faster
- than existing blockchain protocols
- and has high security based
- on Asynchronous Byzantine Fault Tolerance or ABFT.
- Users who own HBAR tokens
- but do not run a node proxystake their account
- to a node and share the HBAR transaction fees.
- In community testing on the mainnet at the time
- of this recording, Hashgraph’s high speed
- and low cost promises fascinating
- peer-to-peer micropayment
- and Internet of Things applications.
- To prevent the contentious forking
- that has occurred for open-source protocols
- like Bitcoin and Ethereum that divided the community
- of developers and token holders,
- the Hashgraph consensus
- algorithm is patented by Swirlds,
- which is controlled by
- Hedera’s founders Leemon Baird
- and Mance Harmon, and then licenced to Hedera.
- Most relevantly, to enable
- and demonstrate a world-class enterprise ecosystem,
- Hedera created a global governing council
- and announced on February 2019
- that its initial members comprised
- telecommunications companies
- Deutsche Telekon and Swisscom,
- financial institution Nomura Holdings,
- media company Magazine Luiza, law firm DLA Piper,
- together with Swirlds as initial network nodes.
- Hedera is seeking 39 global blue chip organisations
- in 18 sectors to form its council.
5.5.4 Facebook’s Libra – Development in Blockchain, DLT and Cryptocurrency (Part 4) (Brian Tang from Asia Capital Markets Institute (ACMI))
- In February 2014, Facebook acquired WhatsApp
- for 19.3 billion U.S. dollars
- in its largest acquisition to date,
- and in the same year, it hired David Marcus,
- PayPal’s president who oversaw
- that company’s acquisition
- of digital wallet, Venmo, parent company, Braintree,
- to run Messenger.
- In 2017, Marcus was also appointed
- to the board of directors
- of cryptocurrency exchange, Coinbase,
- and resigned after five months
- to become Facebook’s new blockchain research head.
- In 1Q 2019, Facebook reported an incredible
- 2.38 billion monthly active users,
- with the largest user base being in India.
- In the same period,
- WhatsApp has 500 million daily active users worldwide.
- In March 2019, its Mandarin-speaking founder,
- Mark Zuckerberg, posted a blog
- on a privacy-focused vision
- for social networking, describing Facebook’s new focus
- on private messaging for interaction,
- including businesses, payment, commerce,
- and ultimately, a platform for many other
- kinds of private services.
- Although not specifically named,
- this has been widely interpreted as his intent
- for Facebook to emulate the
- approach and success of WeChat.
- With the announcement of Libra in June,
- The Economist declared that,
- “Facebook wants to create
- “a global currency” with the stated aim
- of financial inclusion to provide free transactions
- to serve the 1.7 billion unbanked across world.
- Libra will be an opensource
- and at least initially, permissioned stablecoin
- backed by a basket of different
- currencies that will enable
- free payment transactions, where the transaction costs
- will be covered by the up to 100 members
- of the Libra Foundation,
- of which Facebook is but one member.
- And each of whom will invest 10 million U.S. dollars
- in Libra Investment Tokens, or LITs,
- and benefit from the interest earned
- from the fiat funds in the Libra Reserve.
- The founding council members of the Libra Foundation
- consist of 28 world-class leaders
- from across different industries, including,
- in payments, Mastercard, PayPal, and Visa,
- in technology and marketplaces, eBay,
- Facebook, Lyft, Spotify, and Uber,
- in telecommunications, Vodafone,
- in blockchain, Coinbase,
- in venture capital, Andreessen Horowitz,
- and finally, for nonprofits
- and multilateral organisations who do not need to pay
- the $10 million, Kiva and Women’s World Banking.
- Facebook plans to create its own digital wallet, Calibra,
- that will need to comply with AML requirements
- for users on-ramping and off-ramping fiat currency.
- While an incredibly innovative initiative
- that has brought together many major global players,
- Libra’s sheer potential size
- and ambition has already caused some concerns.
- Legislators in the U.S.
- and EU have called for greater scrutiny
- before Libra proceeds further.
- Bank of England Governor
- and former FSB chairman, Mark Carney, has said
- “We will look at it very closely
- and in coordinated fashion at the level of the G7,
- the BIS, the FSB and the IMF.
- So open mind, but not open door.”
- Given Facebook’s 2.38 billion monthly active users,
- plus the user base of the other
- significant council members,
- this attitude is not surprising.
- If it were a country,
- Facebook alone would be the
- largest country in the world.
- And its proposed introduction of a global currency,
- not only makes it a potential systemic risk,
- but also purports to allow mainly for-profit
- private sector multinational companies to impact
- monetary policy, especially over smaller nation states.
- It also should be recalled that cryptocurrency is banned
- in India, which is Facebook’s largest user base.
- Many proponents aim for blockchain
- and DLT to be the new decentralised Web 3.0 payment
- and identity layer in the internet technology stack.
- Accordingly, public blockchain proponents,
- such as Consensys’ Joe Lubin, have called Libra,
- “a centralised wolf in a decentralised sheep’s clothing.”
- Currently, global banking
- and finance relies on the financial messaging network
- created by the cooperative
- Society for Worldwide Interbank
- Financial Telecommunications
- or SWIFT, in 1974, which enables its 11,000-member
- institutions in 200 countries to quickly, accurately,
- and securely send money transfer messages
- to confirm transactions
- and handles U.S. $5 trillion worth of transactions a day.
- Yet, settlement and payment
- of those transactions can take days.
- With DLT technologies for enterprises,
- like Ripple, seeking to compete in this space,
- and JP Morgan’s recently
- announced USD-backed stablecoin,
- JPM Coin, to enable instant settlement
- and payment between the bank’s
- global institutional clients,
- SWIFT introduced Global Payments
- Innovation, or GPI, in 2017
- to speed up the processing
- time of cross-border payments.
- The week after Facebook’s Libra announcement,
- SWIFT announced that pending the success
- of its current proof of concept trial with R3,
- it would soon be enabling payments on DLT-based
- trade platforms on SWIFT gpi,
- thereby automatically passing them
- onto the banking system.
- It’ll be fascinating to see how the Libra saga,
- together with the overall interaction
- and tension between distributed
- and centralised approaches to global finance
- and payments, unfolds.
Module 5 Reference Reading
References and Suggestions for Further Reading in Module 5
- Nicola Atzei, Massimo Bartoletti, Tiziana Cimoli, “A survey of attacks on Ethereum smart contracts”, 2016.
- Xiaoqi Li, Peng Jiang, Ting Chen, Xiapu Luo, Qiaoyan Wen, “A survey on the security of blockchain systems”, 2017.
- Hai Wang, Yong Wang, Zigang Cao, Zhen Li, Gang Xiong, “An overview of blockchain security analysis”, 2018.
Module 6 The “Evil Sides” of Blockchain and Legal Regulations for Blockchain
Welcome to Module 6

Dear Learners,
Welcome to Module 6 – The “Evil” Sides of Blockchain and Legal Regulations for Blockchain. In the last Module, we looked at security and privacy concerns of a blockchain platform and learnt about some of the risks with blockchain solutions, as well as, the benefits and opportunities in using blockchain for different industrial applications.
In Module 6, we are happy to introduce five guest speakers to you, among others, Bowie Lau (Founder & MD of MaGESpire) will talk about the “dark” side of blockchain. Then, Malcolm Wright (Chief Compliance Officer at Diginex) will speak about criminal use of payment blockchains. Furthermore, we will hear from Charles d’Haussy (Director of Strategic Initiatives at ConsenSys) who will share his views on whether blockchains need regulations.
Professor Douglas Arner of HKU Law Faculty (Course director of Introduction to FinTech) will discuss the global practice and the role of financial regulations for blockchain. And we will also learn about global digital assets regulatory trends from Henri Arslanian (FinTech & Crypto Leader for Asia, PwC).
This is an exciting week. May you enjoy the great contents from our guest speakers.
HKU Blockchain and FinTech Course Team
Module 6 Learning Objectives
After completing Module 6, learners should be able to:
- understand there is an “evil” (negative) side of blockchain, in particular, relating to cryptocurrency;
- understand why bitcoins (or cryptocurrency) provide a means for criminals to collect ransom for the ransomware attacks, and doing money laundering;
- understand the risks of investing on cryptocurrency and the security concerns of using cryptocurrency exchanges;
- understand the necessity of regulation for cryptocurrency and the exchanges.
6.1.1 The Evil Sides of Blockchains Part 1 Ransomware
- Welcome to the last module of our blockchain course.
- In the first four modules,
- we talked about the basics
- about blockchain technologies,
- and also the properties of blockchain,
- what are the good points and the positive sides
- of blockchain technologies.
- From the last module, we started
- to look at the negative sides
- of blockchain technology.
- For example, we talked about the scalability
- of blockchain technology.
- And also, we talked about the security
- and privacy issues saying
- that it may not be 100% secure if you try
- to use blockchain technologies.
- In this module, we want to take this further.
- We want to focus on the evil sides of blockchain.
- In particular, we want to talk about cryptocurrency,
- for example, Bitcoin.
- In this module, we want to talk about four topics.
- The first one is the ransomware, the second one
- is money laundering, and the third one is because a lot
- of people are trying to use cryptocurrency
- for investment, so we want to investigate
- whether investing in cryptocurrency is risky or not.
- And finally, we also want to talk about the issues
- in using the cryptocurrency exchanges.
- The first topic we want to talk about is ransomware.
- So, what is ransomware?
- Ransomware in fact is a one type of the malware.
- Malware, refers to malicious software.
- It’s a generic term referring
- to those harmful programs
- that hackers usually use to cause damages
- to people’s computers,
- servers, or computer networks.
- Let me give you some examples.
- Virus is a type of malware, worms,
- Trojans, even spyware,
- they are classified as one type of malware.
- Then what is ransomware?
- Ransomware is kind of like a kidnapping software.
- Of course, they’re there not trying to kidnap your files,
- but instead what they do is they try to encrypt your files
- in your hard disc so that you can’t access
- to it without a private key,
- and then they will try to ask for a payment
- which is the ransom before
- giving you the encryption key.
- Probably, everybody heard about the Wannacry
- which is a very famous ransomware that encrypt a lot
- of people’s files and ask for the ransoms.
- The point is that the attack
- is not only for private enterprise or private companies,
- they also aim at hospitals,
- public transportation department,
- and also include the police department.
- Now, if you think about it, in a hospital,
- if the ransomware can attack
- into all the patients’ records
- and encrypt all the patients records,
- and the hospital has no way to decrypt the records,
- then how can they treat the patients?
- So what they have to do is to pay the payments.
- Similar to the kidnapping, for the criminals,
- the most difficult part for a kidnapping case
- is to get the ransom because it’s easily tracked
- by the police.
- Now, then we will see how
- Bitcoin can help these criminals.
- Let me remind you one
- of the advantage of Bitcoin is anonymous.
- It means that it’s very difficult to trace
- where the Bitcoin goes and who is the owner
- of the account the Bitcoin that received the payment.
- For ransomware, what they usually do is they will ask
- for payment in terms of Bitcoin.
- Now, let me give you a concrete example.
- This is an email received by a victim
- that has been attacked by a ransomware.
- Now, if you look at it carefully,
- then you can see that they ask you to do the following
- in order to get the private key to decrypt the files,
- otherwise you’re not able to access all the files
- that they encrypted.
- Step one, you can send us .7 Bitcoin
- for each affected PC,
- or if you want to retrieve all the private keys
- for all the affected PCs, they give you a discount.
- They ask you for three Bitcoins.
- Of course, they also will give you the accounts
- of the Bitcoins where you can deposit the Bitcoins.
- Once you deposit the Bitcoins,
- you send them an email,
- they check it, and if it’s okay,
- then they will release you a software
- that contain the encryption key
- so that you can decrypt all your files
- and get back the access to all the files.
- So this is how they try to obtain the ransom
- from the victims.
- In fact, they’re organised crime.
- They even have customer service to talk to you online
- if you say that “Oh, I don’t know how to buy the Bitcoin…
- I don’t know how to deposit the Bitcoin
- into your accounts.”
- They have customer service that
- you can talk to them online
- to teach you how to buy the Bitcoins
- and how to do deposit in order to get the decryption key.
- To conclude, you can see
- the criminal actually take advantage
- of Bitcoin’s anonymous property to avoid being traced
- to get the ransom.
- It’s very, very difficult if you still remember
- what we talked about to trace who is the owner
- of the Bitcoin account.
- This is the first example of how the bad people,
- the criminals make use of Bitcoin to do evil things.
- Let me give you another example.
- Have you heard about dark web?
- In fact, dark web is just like what you have seen
- in the movie.
- This is the part of the internet
- that will not be indexed
- by common search engines like Google.
- If you use Google to search it,
- you might not be able to get access
- into these dark web websites.
- What they do is they use solely the special software
- in order to access to this dark web,
- and based on this software,
- your identity will be kept anonymous
- and you are not traceable.
- You can imagine that this becomes a hotbed
- for criminal activities.
- Of course, I want to emphasise that not all parts
- of the dark web are related to criminal activities,
- but a significant part of it is actually related
- to criminal activities.
- In fact, if you can get into the dark web
- using the software,
- you can actually buy the credit card numbers
- people stole already, some credential
- to the bank account so that you can get the money
- from the bank accounts, and you can buy drugs,
- guns, counterfeit money, or even you can hire hackers
- to hack some of the websites,
- and also you can buy the hacking tools
- from these dark web websites.
- You know how they get the money back?
- They use Bitcoin.
- Bitcoin become the defacto currency of the dark web.
- Also, because of the non-traceable
- property of the Bitcoin,
- it’s very difficult for the law enforcement
- to keep track where the money goes
- and how they can get the money.
6.1.2 The Evil Sides of Blockchains Part 2: Money Laundering
- The second example is money laundering.
- What is money laundering?
- To make it very simple, it’s basically the art
- of making money that comes from source A,
- usually source A is illegal, look like it comes
- from source B, and source B usually is a legal channel.
- Now, if you look at money laundering
- in a high level manner, usually it involves three steps.
- The first step is called placement.
- Placement is trying to insert the dirty money
- into a legal system.
- For example, you can deposit the money
- that you gained from the transactions into a bank,
- and the second part is
- so once the dirty money gets into the legal system,
- the second part is, we want
- to confuse law enforcement using multiple transactions
- to make it very difficult to trace where the money goes.
- For example, you can have multiple transactions
- across different countries.
- For example, you can use the
- money to buy Forex in overseas,
- buy stocks, etc.
- After this layering, because
- of the cross-country manner,
- the law enforcement, it’s very difficult
- to trace where the money goes
- and where the money comes from.
- Finally, the last step is called integration.
- In this integration step, the money
- that’s being laundered will go back to the owner.
- Now, if you look at these three steps,
- you can see that placement
- is one of the most dangerous steps.
- Without cryptocurrency, people usually do it this way:
- They will try to deposit the money in small amounts
- using many multiple accounts,
- or they buy fake accounts from real people
- and they try to insert the dirty money
- into the legal system bit by bit.
- Layering is also another important step
- because for layering if you do not do a good job,
- the law enforcement may be able to trace
- where the money goes and
- where the money comes from.
- Let’s try to take a look at how Bitcoin
- can help this kind of criminal activities.
- If you think about it carefully, if you try to go
- to your bank account to open a new account,
- what do you need to do?
- You need to provide proof
- of your identities, and also
- you need to give the proof
- of your address.
- In fact, this is known as the KYC requirement.
- KYC refers to know your customer requirement.
- This is a common requirement for all countries
- if you try to go to a bank to open an account,
- it’s the requirement from the law.
- On the other hand, we know that for Bitcoin
- or many other cryptocurrencies,
- there’s no universal regulation governing people on
- how to open an account.
- In fact, I do not need to give you my identity
- nor my address in order to open an account
- to trade Bitcoins.
- Now, the consequence or the implication is very simple.
- Then you can see the dirty money can easily get
- into the cryptocurrency market
- without people knowing your identity.
- In other words, you can easily
- open a cryptocurrency account
- in one of the exchanges in the world
- and try to use your real money
- to buy the cryptocurrency
- without showing who you are
- and where you live, then your money will be converted
- into the cryptocurrency, the crypto coins easily.
- The second part,
- I hope you still remember the transactions
- on cryptocurrencies also can be anonymous
- or password anonymous
- and can cross country boundaries as well.
- You can see that this actually facilitates
- the layering step in money laundering
- because it’s very difficult to trace where the money goes
- if it’s cross-country boundaries.
- Let me give you an example.
- This is a very well-known marketplace
- in the dark web called Silk Road.
- They open a marketplace of people to buy illegal things
- in the dark web.
- If you look at the flow of the payment system
- in Silk Road, so what the buyer will do
- is they try to exchange real currency for Bitcoin.
- In fact, they can easily find the exchanger
- for them to do it.
- What they do is, after they get the Bitcoin,
- they can transfer the Bitcoin to the Silk Road accounts
- and the buyer can easily make purchases,
- and the Bitcoin will be held in the Silk Road account
- until the order is finalised.
- And of course, Silk Road tries to make profit
- by taking the commission on the transactions.
- And after the vendor is paid,
- the vendor can move the Bitcoin
- from the Silk Road account to their own account,
- and through another exchange,
- they can actually convert the Bitcoin
- into real currency as well.
- Now then in this way, you can see that it’s not easy
- to trace where the money comes from
- and where the money goes because many
- of the Bitcoin exchanges,
- they may not require the buyers or the sellers
- to identify themselves or provide the proof
- of their address.
- Of course, the real situation for money laundering
- is even more complicated.
- I just want to show you some simple examples saying
- that it’s very easy to use Bitcoin to do money laundering.
- Now, I hope you understand
- the second point of it now.
6.1.3 The Evil Sides of Blockchains Part 3: Cyber Currencies
- Now let us proceed to the third example.
- Right now, people try to buy cryptocurrencies,
- for example Bitcoin, as an investment, and of course,
- a lot of people make a lot of money,
- and maybe some of the people
- lose a lot of money as well.
- If you look at the chart I provided here,
- you can see that the price of Bitcoin
- as well as other cryptocurrencies
- actually fluctuated a lot
- in the recent years.
- Let me give you some example.
- The highest price that Bitcoin
- achieved was in December 2017.
- It’s about US $20,000.
- Compare to Bitcoin at the beginning at 2009,
- it’s only US $.009 per Bitcoin, and then you can see
- that it’s already increased a lot.
- If you look at right now, 2019, the current price
- is about 8,000.
- You can see that actually the Bitcoin price
- fluctuates a lot.
- Now let me give you some more figures
- then you can see that actually the price
- of the cryptocurrency fluctuates only in a few hours
- or even in a few days.
- From its peak in December 2017, the Bitcoin drops
- by already 65% in February, 2018.
- You can see that it’s only like two months.
- The price can drop by 65%.
- Another example, in the same day, May 30th of 2019,
- the price of Bitcoin drops from 9,000 to 8,000.
- It’s actually about an 11% drop on some exchange
- only within a few hours.
- So you can see that we should try
- to answer a more important question,
- can we treat cryptocurrency as an investment tool?
- Is it risky?
- I want to tell you the truth.
- In fact, it’s very risky.
- First of all, we do not have,
- or only have limited regulation governing people
- how to trade cryptocurrencies.
- In other words, the investment is not protected
- by the law unlike those at stock markets.
- And it’s also very unclear what are the factors
- that will affect the price of the cryptocurrency,
- even worse than buying stocks.
- Of course buying stocks we also do not know completely
- what factors will affect the price of the stock,
- but for cryptocurrency it’s even more difficult
- to make an estimation for when the price will go up
- and when the price will go down.
- Because we do not have a lot
- of regulations governing
- how we trade the cryptocurrencies,
- so in fact it might be possible
- that the price can be manipulated by some big players.
- Although we do not have an affirmative answer,
- but some evidence already show
- that the so-called whales,
- the big whales means that they’re having a lot
- of cryptocurrency on hand, who can try to buy
- and sell a large amount of Bitcoin in a very short time,
- will actually affect the price immediately.
- Let me give you one example.
- On April 3rd, 2019
- at about midnight, the price
- of Bitcoin is around 4,190,
- but then just one hour later,
- the price actually increase to 4,900.
- If you think about it, it’s about already 20% increase
- in an hour, and people look at the history again,
- and then people suspect that
- there had been a single order
- of about 20,000 Bitcoins that
- triggered the price change.
- If you look at the 2017 Bitcoin price bubble,
- you remember the highest
- price was at December 2017, right?
- You know why people think that
- the price went up so quickly?
- They believe that it was created by the rumour saying
- that the mainstream finance people
- were about to invest in cryptocurrencies.
- So that’s why everybody tried to get the Bitcoin
- so up goes the price.
- Now, to conclude, you take your own risk
- if you try to invest in cryptocurrencies.
- The main reason is, right now, not all the countries
- have very complete regulations
- that can govern the trading of cryptocurrencies.
- In other words, the regulation is not in order yet.
6.1.4 The Evil Sides of Blockchains Part 4 Cyber Security Exchanges
- Now finally, I want to talk
- about cryptocurrency exchanges.
- Now, a cryptocurrency exchange
- is just like a stock exchange.
- Now, whenever you want
- to trade cryptocurrency,
- you need to go into one of
- these cryptocurrency exchanges.
- Unfortunately, again, there
- are no common regulations
- for these exchanges in the world.
- But on the other hand,
- there are more than 500
- cryptocurrency exchanges
- in the world right now.
- And if you look at the figures,
- the combined daily trade
- volume of the top 10 exchanges
- is more than U.S. $6.5 billion,
- so it’s a lot of transactions,
- a lot of money involved in
- these cryptocurrency exchanges.
- My question is, which exchange is more reliable?
- Or are they actually reliable?
- I’ll give you a very recent incidence
- so that you know what happened to these exchanges.
- There’s an exchange in Canada
- which is Canada’s largest cryptocurrency exchange.
- Recently, the CEO, the
- founder died in December, 2018
- at a very young age, 30 only.
- But the problem is, the company claimed that
- only the CEO has the encryption key
- to a lot of wallets that contained the cryptocurrencies.
- Because he died and his laptop was encrypted
- and everything was encrypted,
- so they’re not able to access this kind of money.
- The amount of money is about U.S. $190 million.
- All the investors’ money was
- not able to be accessed from then on.
- If you look at the incidences,
- you’ll find something interesting or strange.
- So about U.S. $190 million
- that cannot be accessed
- because the founder died in December, 2018,
- and he is the only one who has the access key.
- So Ernst and Young was appointed by the court
- to take a look at this case.
- And according to a report, what they found out is,
- it’s so strange that even after the founder die,
- the company, they claim that they made a mistake
- transferring another 103 bitcoins to a wallet
- that only the founder has the access key to open it.
- In other words, the transfer
- was done in February, 2019,
- but actually the CEO died in 2018, December
- and only he has the access key.
- These 103 bitcoins were gone and
- nobody can access it anymore.
- This case actually aroused a lot of interest
- in most of the investigators in the world.
- And some of the investigators actually found that
- based on the public data,
- they claimed that in fact in those wallets,
- the money was gone already,
- was empty eight months before the CEO died.
- There’s a rumor whether the CEO actually died
- or he faked his death and stole all the money.
- From this simple incident,
- you can see that it’s not completely safe
- to put your money into this kind of exchange,
- and because of the lack of regulations,
- we are not sure which exchange
- is more reliable than the other.
6.2 The “Dark” Side of Blockchain (Bowie Lau from MaGESPire)
- Hello, I’m Bowie Lau, founder of MaGESpire
- which is a Blockchain Venture Development
- and Education group in Hong Kong.
- For all of the good things
- blockchain can bring to the world
- including helping organisations
- drive technological transformation,
- disruption, and growth,
- there is also a dark side of blockchain.
- In this short video, I’m going to take you over
- the evil sides of blockchain.
- Greed is the hardest thing to shake out
- in the blockchain crypto space.
- Some of you may remember,
- Gordon Gekko in the movie
- “Wall Street” immortalised the words “Greed is good.”
- But, we all know how that ends
- if it is unrestrained greed.
- It devastated the dot-com boom in the late 90s
- and it has the potential to do the same again.
- As of December 2018, over a billion dollars
- have been stolen through ICO scams.
- And as the number of start-ups
- looking for ICO funding increased,
- so did the number of scams and vanishing acts.
- In a recent report,
- The Wall Street Journal indicated that
- out of 1,450 start-ups analysed,
- more than 270 were literally what we could call trash,
- or tokens created uniquely to rip off investors.
- There are also manipulative
- and predatory market practises
- that seem prevalent in cryptocurrency exchanges.
- Most notorious is the “Pump and Dump” schemes
- that give false temporary impression
- of great growth story,
- and immense liquidity in certain cryptocurrencies
- and often these are accompanied by fake news.
- Beware, if something sounds too good to be true,
- then it probably is too good to be true.
- Hacking is another problem the crypto world faces
- in security, both physical and cyber of exchanges,
- platforms and smart contracts.
- 2018 turned out to be a record-breaking year
- for crypto exchange hacks,
- but there have been other kind of hacks as well
- like the DAO hack in July 2016,
- that split the Ethereum blockchain world into two,
- and more recently KICKICO who experienced a breach
- where tokens estimated to be worth around
- eight million US dollars were stolen
- due to a compromised private key of a main wallet.
- Sources of such hacks fall into two categories,
- internal or external.
- Same as bank robbery,
- this can be executed as an internal job
- or by an external actor.
- Sometimes bad coding habits
- and unforeseen logic cases
- can be harmful when deploying immutable
- or unchangeable smart contracts.
- Sometimes, intentional back doors
- with not so honourable intent that go undetected
- can also compromise smart contracts.
- This is not to say smart contracts are to blame,
- but the practitioners programming these
- smart contracts just like any other software
- development need to be mindful of vulnerabilities and
- edge cases, and should have adequate
- contingency plans.
- Just follow the famous quote
- from Andreas Antonopoulos,
- a Bitcoin and blockchain expert,
- “Your keys, your bitcoin.
- Not your keys, not your bitcoin.”
- On the other hand, more recently came up the case
- Quadriga exchange.
- The unexpected death of Gerald Cotten,
- the CEO of popular Canadian exchange QuadrigaCX,
- had left more than $140 million
- of users’ funds inaccessible,
- since he was the only one in the company
- able to access the money.
- According to Gerald’s wife,
- Gerald accidentally died in his trip in India
- back in December 2018.
- They claim that Cotten held
- sole responsibility for handling the funds and coins,
- and the remaining team members have had no luck
- accessing the exchange’s cold wallets
- ever since he passed away.
- This is an extreme example of key man risk.
- Since 2009, estimates suggest criminals have used
- the hyper-connected cryptocurrency ecosystem
- to launder well over $2.5 billion USD
- worth of dirty Bitcoin.
- Bitcoin is easily laundered
- through unregulated exchanges.
- Unregulated cryptocurrency exchanges,
- those without proper Know Your Customer
- and anti-money-laundering procedures
- can also be used to clean Bitcoin, even without using
- a cryptocurrency mixing service beforehand.
- Just like a Virtual Private Network, VPN
- scrambles your IP address
- which by the way,
- is an unique address identifying
- your computer and location.
- IP stands for Internet Protocol
- and makes it difficult to track your browsing activity.
- Mixing is a concept in cryptocurrencies
- where a single transaction is merged,
- and mixed with multiple other such transactions,
- either real or fake with an intention
- of making it difficult to trace,
- or establish a clear audit trail of transactions
- from source to destination.
- One of the significant risks associated
- with digital currencies is the ability
- of criminals and terrorists,
- to use these new technologies
- for their own benefit.
- While information on each transaction is recorded
- on the blockchain,
- this data is not directly linked to names,
- physical addresses or other identifying information.
- This makes ownership of digital currencies anonymous
- to a certain degree,
- and complicates efforts by law enforcement agencies
- to identify individual transactions
- and link them to users.
- Terrorists using cryptocurrency to evade detection
- and to fundraise.
- Terrorists, like other criminals use cryptocurrency
- because it provides the same form of anonymity
- in the financial setting,
- as encryption does for communication systems.
- By fundraising and making financial transactions
- online with Bitcoin,
- terrorists and other criminals can avoid interference
- from financial regulators,
- or other third-parties who might otherwise
- take steps to prevent their operations.
- Studies show that Bitcoin featured
- in high-profile investigations
- involving payments between criminals,
- and has been used in more
- than 40% of these transactions
- in the European Union.
- People are using darknet
- to conduct lots of illegal activities.
- Darknet is basically a clunky version of the Internet
- which uses special programme to hide your IP address.
- The programme is called the Onion Router,
- and it sends your IP address through multiple places
- around the world juch like the rings of an onion layers.
- The infamous pioneer of the dark web’s large-scale
- illegal trade platform was Ross Ulbricht.
- He was the person behind Silk Road,
- the biggest online marketplace that started out
- as an experiment,
- and turned into the go-to resource
- for buying and selling drugs and fake documents,
- as well as money laundering,
- running things with Bitcoin as the main currency.
- The dealers were then sending the drugs
- via post or left them in PO boxes.
- Other options may also include providing buyers
- with detailed instructions
- of where they can pick up their sensitive purchase.
- And closer to home, family lawyers are worried that
- couples who are getting divorced
- might end up buying cryptocurrency
- to hide their money from the court.
- Similarly, bankrupt companies could stash their funds
- in cryptocurrency so they
- don’t have to pay out creditors.
- Therefore, when the company is liquidated,
- they won’t be able to sell anything
- because there won’t be anything to be found.
- Take ownership of your own destiny
- in an increasingly cyber world
- with complex technologies like
- Blockchain, AI on the rise.
- Equip yourself with basic cybersecurity knowledge
- and question anything that sounds too good to be true.
- If you are dealing in large value digital assets
- or cryptocurrencies,
- please follow clean wallet habits
- like cold wallets and multi-signature wallets
- with trusted parties.
- And more importantly don’t be evil.
- That’s all from me.
- Thanks for watching.
6.3 Criminal Use of Payment Blockchains (Malcolm Wright from Diginex)
- Today we will look at criminal use
- of payment blockchains,
- and what is being done to mitigate
- cryptocurrency financial crime.
- It is useful to start with some headline figures.
- According to a 2018 Europol report,
- three to four billion US dollars is laundered
- through the cryptocurrency ecosystem.
- That number is still small compared
- to the one to two trillion US dollar estimate
- for the traditional financial sector,
- but is recognised to be growing
- and the international community has moved
- rapidly to take mitigating actions.
- In October 2018, the global anti money laundering,
- or AML, standards-setting body, the FATF,
- issued a statement that it would seek
- to issue regulatory standards
- for firms that provide cryptocurrency services.
- It was noted that this work was considered urgent,
- and so by June 2019 the FATF
- had issued recommendations on cryptocurrency
- that countries should adopt.
- Countries follow FATF recommendations
- or risk facing actions that would be detrimental
- to their economic growth.
- The FATF introduced five activities
- that countries should regulate for.
- First, exchange between virtual assets
- and fiat currencies.
- Second, the exchange between one or more forms
- of virtual assets.
- Third, transfer of virtual assets
- from one party to another.
- Fourth, safekeeping and/or administration
- of virtual assets.
- Lastly, participation in
- and provision of financial services
- related to an issuer’s offer
- and/or the sale of a virtual asset.
- The FATF then produced a guide for countries
- and virtual asset service providers,
- or VASPs for short.
- VASPs are considered any firm offering
- the previously mentioned activities.
- This means that if you are considering building
- or operating a VASP,
- you will likely require a licence in every country
- where you will have customers.
- From the regulatory perspective,
- VASPs will now operate in the same way
- as financial institutions,
- with the same compliance controls.
- This means that if you sign up with a VASP
- you will need to conduct full Know Your Customer,
- or KYC, procedures such as a selfie identification
- and providing proof of address,
- or confirming that the source of funds
- that are added to your account.
- Further requirements also mean
- that if you are sending funds
- to another person’s cryptocurrency address
- you will need to provide details
- on who that person is.
- Moreover, if you are receiving cryptocurrency
- from a third party
- then you will need to give accurate details
- on yourself to the sender.
- All this means that the perceived anonymity
- of cryptocurrency is drastically reduced,
- and with it the opportunity
- to use the ecosystem for financial crime.
- Cryptocurrency also benefits from another measure
- to prevent financial crime that is not available
- to the traditional financial sector.
- Blockchain analytics enables
- transparency and traceability
- on the history of coins and wallets.
- Thus, VASPs can check whether an address
- or a wallet has a suspicious past,
- such as having received funds
- from an online drugs marketplace on the dark web.
- Such tools can also check the history to see
- if there has been any attempt
- to hide the tracks of the coin’s history,
- which again could be a sign of suspicion.
- One area that is causing concern
- amongst law enforcement and regulators alike
- is the use of cryptocurrencies
- with privacy-preserving features.
- Otherwise known as privacy coins.
- These are coins where the history,
- and even the details of the transaction itself,
- can be hidden.
- It is worth noting here
- that not all privacy coins are created equal,
- and that a desire to use a privacy coin
- does not make one a criminal.
- But Europol did report in 2018
- that there had been a shift by criminals
- towards using one particular privacy coin
- called Monero.
- So what are the major financial crimes
- we see in cryptocurrency right now?
- The most widely spoken about
- is cryptoexchange hacking.
- In 2018, Ciphertrace reported
- that approximately one billion US dollars
- had been stolen from cryptocurrency exchanges.
- After the theft, hackers will use various techniques
- to split the coins up into smaller amounts
- and spread over multiple accounts before cashing out.
- This is known as money muling.
- Dark web sales are then also still highly prevalent
- and also widely reported.
- The dark web, an area of the Internet
- that runs anonymously and cannot be indexed
- by search engines like Google,
- offers goods and services for sale
- including drugs, guns,
- stolen debit and credit cards,
- and Crime as a Service
- where criminals provide their services
- to assist with cashing out
- illegally obtained cryptocurrency
- back into real money.
- The instant, cross-border nature of cryptocurrency
- also makes it an attractive means
- of funds transfer for criminals.
- In the traditional world, cash would have been used
- and transported across borders
- to pay a drug cartel for the manufacturer
- where distribution was in a different country.
- With cryptocurrency, it can be instant and online.
- But as regulators tighten their approach towards VASPs,
- and in particular crypto exchanges,
- it will be much harder
- to conduct this activity through an exchange.
- Finally, money mules form a key strategic part
- of any money launderer’s toolkit.
- Cryptocurrency is no different.
- Money mules are individuals offered a commission
- in return for their assistance.
- They may be unaware of the illegality
- of what they are doing.
- For example, in the UK, schoolchildren
- have been recruited by organised crime gangs
- to use their bank accounts.
- The criminal sends 500 pounds
- to the money mule’s account,
- the money mule might keep 10%
- and then send the remainder
- on to an account the criminal instructs.
- This has been transferred into the cryptocurrency world,
- making easier where exchanges have low
- or no KYC to open an account
- or they have KYC-free transaction thresholds.
- With all this said, cryptocurrency has legitimate uses
- and it is not just for criminals.
- In fact, according to the blockchain analytics firm,
- Elliptic, the percentage of criminally derived funds
- is decreasing against the overall traded volume.
- With the advent of regulation for VASPs
- we would expect that number to drop further
- as the legitimate cryptocurrency exchanges
- understand their customers
- and their trading partners better.
- Ultimately, cryptocurrency’s future
- will look more like banking
- than a fringe activity of its early days
- and with it, a greater safety and protection
- will be assured, not only for customers,
- but also for the victims
- of financial and social crimes.
6.4 The Role of Financial Regulations for Blockchain (Professor Douglas Arner, Faculty of Law at the University of Hong Kong)
- Hello, my name is Douglas Arner.
- I’m a professor at the University of Hong Kong.
- Today, we’re going to talk a little bit
- around the role of financial regulation
- when we talk about blockchain and FinTech.
- And I know for some of you
- working in technology areas,
- that this whole idea of regulation seems strange
- that basically there are many in the technology area
- who feel that when we’re thinking
- about new technologies, innovation,
- that we should take a hands-off approach,
- leave them alone for a while.
- And that is very often the case though, even in tech,
- there are rising new questions about that
- when we look at Facebook, or Amazon,
- or even Alibaba and Tencent
- in China about what can happen
- when you leave an industry unregulated
- perhaps for too long.
- But we’re talking about finance.
- And finance is perhaps the most regulated
- industry in the world.
- And that means that if we are talking about blockchain
- in finance, we’re talking about FinTech and blockchain.
- By nature, we are talking about involvement
- in a regulated industry.
- And so we have to think about
- how does regulation apply to blockchain
- when you take it into the financial services context.
- And I think when we think about regulation,
- and particularly financial regulation,
- there are really a series of traditional approaches
- when faced with a financial innovation.
- And many uses of blockchain in finance
- are very much innovations.
- The first of those is really to do nothing.
- In other words, we say, right, we’re not going to step in,
- we’re not going to do anything,
- we’re going to see how this develops.
- And then later on, maybe we’ll decide
- whether we need to do anything or not.
- And this is an approach
- that a number of countries have taken.
- But as the role of blockchain,
- particularly some of its leading applications,
- like cryptocurrencies and Initial Coin Offerings
- have grown larger and larger,
- an increasing number of regulators around the world,
- at the global level, at the regional level,
- at the domestic level, at the industry level,
- are taking a look at what sort of approaches.
- At the other end of the spectrum is prohibition.
- And there are often questions about
- with a new financial innovation, is this a good idea?
- Is it something that we should allow at all?
- And actually, we have a range of countries
- which have prohibited certain aspects
- of the use of blockchain in financial services.
- Certainly, China is probably
- the most high profile example,
- with prohibitions on ICOs,
- prohibitions around a range
- of cryptocurrency exchanges, cryptocurrency uses.
- But at the same time, a very positive approach
- to blockchain more generally,
- but a very prohibitive approach to certain aspects,
- particularly certain financial transactions.
- Between those spectrums,
- most jurisdictions are working with a range of options.
- Some are beginning to use the existing legal
- and regulatory frameworks to try to take it in.
- Others are putting in place new legislation,
- places like Switzerland
- or New York State in the United States
- have put in place new legislation
- to deal with specific aspects of blockchain
- in financial services such as payments,
- or in the context of Switzerland, more generally.
- So what are we saying?
- I think, generally speaking, we can say
- that the trend in regulation of blockchain
- in the area of finance is
- towards a functional approach.
- What do I mean by that?
- I mean, that instead of
- having a system, a law,
- a framework that deals
- with blockchain generally,
- we look at its uses.
- What is the technology being used for?
- And what sorts of regulatory concerns
- does the technology raise in that specific context?
- And so, we’re seeing a range
- of different functional ways
- that blockchain is being used
- in the financial services sector.
- Some of these are largely outside of regulated areas,
- things where you are using blockchain
- for certain forms of contracts.
- This is likely to be outside
- of the regulatory framework,
- but it is likely to be under the general legal framework
- for contracts.
- Others are around private ordering.
- How do you set up industry standards,
- for instance, from the international
- standards organization,
- so that you know whether or not
- this is a proper blockchain,
- a good blockchain, a
- functional blockchain.
- Likewise, we’re seeing an increasing use in most places
- of general consumer protection legislation,
- the idea that consumers should be able to rely
- on what is stated in an online context.
- But where we’re seeing most of the activity
- is in the highest profile case uses,
- the first, cryptocurrencies,
- the second in the context of financing,
- and the third in the context of exchanges.
- If we look at currency and payments,
- every country in the world has a framework
- for regulating payments.
- Payments are something
- that have a very important role in society
- and hence, a clear regulatory need.
- And as a result, in most jurisdictions,
- if you are building a blockchain
- based payment framework,
- you are going to be dealing
- with the same payment regulatory framework
- as a non-blockchain based payment framework
- and certainly that is the trend that we’re seeing.
- Lots of questions about certain blockchain systems,
- creating new currencies, new forms of money.
- And in every country in the world,
- there is legislation about what constitutes a currency.
- And countries have taken very different approaches.
- Japan is taking an open approach
- to allowing it to be a currency,
- China is taking a very restrictive approach.
- The end result is that the decision
- of whether or not something is legally a currency or not
- depends upon the individual countries
- and the users within those.
- Where we’re seeing perhaps the most activity
- is around financing.
- This started out in the context of ICOs,
- it is expanded in the context
- of things like Security Token Offerings, STOs,
- and now Exchange Token Offerings.
- So we see different frameworks
- depending on the type of financing
- that is being undertaken.
- Is it actually a donation?
- If it’s actually a donation to support research,
- then very limited regulation.
- Is it a pure utility function?
- Is it something where you have a token
- which can be used for a licence or some product
- that will be produced in future?
- That is what we would think of as utility
- or reward-based systems.
- And these generally fall into areas
- of consumer protection and contract law.
- Or is it a financial instrument?
- And if it’s a financial instrument,
- the trend increasingly in major jurisdictions
- from the United States, to the UK, to Hong Kong,
- to Singapore, is to treat that
- under the traditional financial regulatory framework.
- And what we’re seeing in the market
- is an increasing decision by participants raising funds
- to support blockchain-based activities
- to structure those accordingly,
- but still large amounts of money being raised.
- And finally, the real focus of most global
- as well as domestic regulators today is on exchanges.
- Exchanges where digital assets can be bought,
- sold, listed and traded, why?
- Because these bring together
- large amounts of digital assets.
- They bring together a range of different participants.
- And they also bring with them risks, the risks of hacking,
- the risk of fraud, the risk of manipulation,
- and as a result, we see a very strong trend
- to bring digital asset exchanges of all forms
- into a regulated environment.
- To the extent that digital asset exchanges
- in many jurisdictions have applied for formal licences
- to be treated as with other exchanges.
- At a global level, the G20, the Financial Stability Board,
- the International Organisation
- of Securities Commissions,
- and others are all focused heavily
- on how to develop appropriate frameworks
- to regulate digital asset exchanges
- so that participants and investors can feel safe
- in the products which they are buying
- and have the confidence to see the industry grow.
6.5 [Does Blockchain Need Legal Regulations? (Charles d’Haussy)
- There’re a lot of activities for the blockchain industry
- which do not need regulation.
- So the blockchain industry is making progress
- on many topics which are not regulated
- because they are just simple
- or they are just technology regulated.
- The thing is blockchain offers a lot
- of financial services use cases
- which people have a very strong appetite for
- but when you start to deal with money,
- you come into the world of financial services
- where there is regulation.
- Not everyone is allowed to transact the money,
- to build services on top of the money.
- So that’s where the regulations comes in.
- The regulations take some time.
- In some places of the world
- or in some topics before they give full regulation.
- Some jurisdictions decide to basically regulate
- from day one,
- some of the regulation gives space
- to technology to go before starting to regulate.
- So there is mainly different approaches
- in terms of regulations.
- We see every month different regulators
- around the world starting
- to get their head around the concept of blockchain,
- the concept of digital assets.
- So concept of digital currencies
- and deciding to give licences
- to different operators to either start
- to operate an exchange, for example,
- or start to accept that the identity of people
- can be distributed or identity of people
- can be owned by themselves
- through some kind of blockchain application
- and digital wallets.
- So the regulations in some
- ways sometimes are slowing down
- the industry a little bit
- but the regulators are also doing their job.
- The regulators have a big
- mandate to protect the investors,
- to protect the consumers
- and in a way, sometimes it takes some time
- to regulate but it’s a good thing
- because at the end of the day,
- they want to make sure that the best experience
- or the technology would be available
- when the technology is ready.
- I think there are two types of regulation
- which are around the blockchain technology.
- The first regulations are about privacy and data privacy.
- Some jurisdictions are very sensible about data privacy,
- they are very sensible about encryptions
- and it sometimes touches the world
- of blockchain technologies.
- Another family of regulations
- which impact the blockchain technology
- or involve the blockchain technology
- are the regulations around the financial services,
- when it comes to money services operations,
- when it comes to securitization of assets.
- Nowadays people can tokenize a full building
- and they can sell a building
- in different kind
- of digital shares representing this building, for example.
- So there are regulations around that
- and some regulators take the time
- to make sure that this is done properly,
- that there are no money laundering activities happening,
- that the people investing in these kind of products
- are authorised to invest, understand the product as well.
- So I think everyone is doing their job here
- and the technologies are bringing innovations
- and the regulators are understanding these innovations
- and trying to basically give a framework around them
- so these innovations bring good to the users.
6.6. Global Digital Assets Regulatory Trends (Henri Arslanian from PwC)
- Hi, there.
- Very excited to be here with all of you today.
- As many of you know, my name is Henri Arslanian,
- and really, my passion
- and my focus in life is the future
- of the financial service industry.
- And I’m very excited to have the opportunity
- to share with you all today
- some of the global digit assets regulatory trends
- that are taking place in our exciting world today.
- But before I start, let me give you a warning.
- Whoever tells you they’re an
- expert when it comes to crypto
- or digital assets, you gotta run away.
- I can tell you, I spend 24/7 of my time in this space.
- I spend my time on digital assets
- and the future of finance on weekends, evenings,
- and I have absolutely no idea where
- the industry will be one month from now
- because things are changing so fast.
- But at least, today, I want to share with you five trends,
- really, very relevant trends that I think could be relevant;
- the importance of regulatory clarity on crypto,
- best practises we are seeing
- when it comes to regulatory trends, U.S. requirements,
- some developments we’re
- seeing with FATF and KYC AML,
- and finally, some tax developments as well.
- And hopefully, with these, you will be able to make
- your own decision on where you believe the industry,
- when it comes to digital assets, is heading
- when it comes to regulatory trends.
- Excited?
- Let’s kick it off.
- First of all, regulatory clarity.
- One thing that’s very important to understand
- is that, compared to two or three years ago,
- there is increasing level of regulatory clarity
- around the world.
- I would personally argue that
- even some of the regulators
- that I deal with are way more knowledgeable
- on digital assets than the average
- financial services professional.
- But just to give an idea,
- my team recently did a study at PWC,
- and we found that about 60%
- of regulators have released
- some type of crypto guidance or regulations
- in the last couple of months,
- and this represents almost 90% of global GDP.
- Another study, recently, by Cambridge University
- said that something around only 5% of regulators
- don’t have somebody looking at crypto internally.
- But really, what’s been remarkable,
- if you saw the number
- of countries that have issued clarity on this topic.
- For example, many countries in Asia,
- countries like Thailand, for example,
- or Hong Kong or Japan, have come up
- with very interesting regulations
- when it come to digital asset space.
- But also, in the Middle East, countries like Bahrain,
- for example, that have, now, some of the most complete
- and comprehensive of crypto
- regulatory fabrics out there.
- But also, some of the countries
- would surprise many of you.
- For example, France is positioning itself
- as one of the leading centers when it comes to ICOs
- and the broader digital asset space.
- With some of the new proposals in France,
- you’ll even be able to file your documents in English,
- which is a pretty good thing for France.
- When you look at, globally,
- some of the trends happening
- on the regulatory perspective,
- there are really three big approaches.
- And I think this is important because
- as you think about regulatory clarity for digital assets,
- it’s really important to think about how
- certain countries are addressing it.
- For example, some countries have taken
- a very principal-based approach,
- which is the first category.
- Countries like Liechtenstein or countries like Gibraltar,
- for example, when you look at Liechtenstein,
- the regulations don’t even talk about
- blockchain or crypto or digital assets.
- They talk about trusted technologies.
- They try to stay completely agnostic
- of the underlined technology that underpins
- whatever is taking place.
- The second category are countries that are putting
- digital assets inside their existing framework.
- A good example of that is actually where I am right now,
- in Hong Kong, where since last November,
- the Hong Kong regulators came up with some guidance
- that says that any licenced fund manager,
- there’s about 2,500 or so in Hong Kong,
- can have up to 10% of their portfolio in crypto
- with no additional licencing conditions.
- Again, taking digital assets,
- putting it inside the existing framework,
- and actually try to put some guidelines around.
- The third category are countries coming up
- with really bespoke regulatory frameworks.
- Great example of this is Bermuda,
- Malta, Bahamas, and so on
- and so forth, were really trying to craft legislation
- specifically for the digital asset space.
- For example, if we look at the legislation of Malta
- or Bermuda, the rules really specify what does a player
- in the digital asset space need to do
- to be regulated in their jurisdiction.
- And this is really interesting what’s happening because,
- frankly, regulators are increasingly have done their job
- and have provided the level of clarity at the industry,
- not only needs, but also, deserves.
- However, doesn’t mean there’s regulatory clarity
- that everything is easy.
- There’s still a lot of challenges.
- For example, there’s number of
- challenges for policymakers.
- One of them is, while despite coming out
- with all the regulatory clarity that you want,
- maybe some of the members of your ecosystem
- are not as active, for example, banks.
- Despite a lot of regulatory clarity globally,
- opening a bank account still remains
- one of the biggest challenge
- for digital assets companies.
- But the other challenge is,
- for example, is ongoing monitoring.
- For example, as a regulator, you could enact
- the best regulations you want, but then,
- you actually need people to be able to enforce it,
- people who understand digital assets.
- And that’s quite tricky because as you would expect,
- a lot of traditional regulators
- or those who have been a regulator for a long time
- may not be as familiar with digital aspects
- as you would expect.
- And they often need to hire people externally to come
- and join the regulator to provide
- in that level of expertise.
- So very interesting what’s
- happening from that perspective.
- Second thing that have been going on
- is really the rise of best practises
- and this is very exciting because what has happened
- over the last couple of months,
- as a lot of the industry players realise
- that the regulations were not coming fast enough,
- they decided, by themself, to come together
- and abide by some series of best practises
- that can bring the industry forward.
- A great example for this is KYC
- and AML; know your customer
- and anti-money laundering regulations.
- The beauty of a lot of these
- crypto exchanges, for example,
- is that they were able to leverage
- the latest regtech technology using tools,
- like biometric face identification,
- using series of selfies to able
- to actually do your onboarding.
- And this is, trust me, is way better than
- going to your old school bank,
- showing them a copy of your passport,
- them making a photo copy, and putting a stamp
- and saying that it’s a certified true copy.
- And this is why a lot of that, the exchanges,
- arguably may even have better KYC
- and AML then some of the traditional banks.
- But also, what’s been really happening,
- a lot of them are increasingly putting in place
- internal governance, internal controls as well,
- to make sure that they have in place the best practises.
- However, there’s still challenges.
- For example, despite all these best practises
- being developed, regulatory clarity as well,
- unfortunately, sometimes there are bad apples.
- For example, recently, in Canada,
- there was an exchange called Quadriga
- where the CEO unfortunately died suddenly in India
- and now there’s about more than $150 million of assets
- belonging to over 115,000 clients
- that are completely not accessible anymore.
- Again, so over the next couple of months
- and years, there will be more
- regulations covering exchanges
- or other industry participants, but at least for now,
- there’s a bit more best practises
- that are being developed.
- Another third, big development going on you have
- to keep an eye on is what’s
- happening in the United States.
- What’s been really interesting is a lot of the big
- U.S. regulations, in many cases, have a global remit.
- For example, when it comes to regulation
- from the Department of Justice
- or Department of Treasury in the U.S.,
- they often apply to any U.S. person
- and what is a U.S. person?
- It applies to American citizens or permanent residents
- that are located anywhere in the world,
- or from a business perspective,
- it also includes are corporation or company
- that is also physically located in the United States.
- So this actually is a pretty good remit
- when you think about it.
- For example, most recently in the United States,
- they very clearly said that
- any U.S. persons are prohibited
- from entering into transactions with people
- who are on these specially designated nationals,
- what we call SDNs.
- These are individuals that the U.S. government
- puts on a list, that is, on a sanctions list,
- and with whom U.S. persons
- are not allowed to transact.
- And this also applies to the crypto space
- because it’s been very clear, for example, OFAC,
- which is the Office of Foreign Assets Control,
- made it very, very clear, saying that actually
- crypto assets are within the remit of OFAC.
- And it’s been very, very interesting to see how
- these U.S. regulations may
- apply their companies globally.
- For example, more recently, two bitcoin addresses
- were put on this specially designated national list
- that is put together by the U.S. Treasury.
- This means that any person who actually transacts
- with these bitcoin addresses
- can actually be come into trouble by the U.S. authorities.
- And there’s many cases of enforcements
- have taken place in the U.S.
- and also, outside of the U.S.
- by American government bodies.
- The big development you need to follow
- is what’s happening with FATF.
- The FATF is a very interesting government body.
- It’s called a Financial Action Task Force, that
- actually tries to bring together issue recommendations
- on a lot of these topics that are popping up.
- What’s been really interesting is, since last February,
- some guidance was being issued on digital assets
- and in Orlando, in June of 2019,
- some guidance was finally
- approved in an FATF meeting.
- It says that, basically, any crypto exchange that sends
- a transaction to another, basically,
- whenever there’s a beneficiary
- and there’s a sender, now, the
- parties from this transaction
- need to know who the originator is,
- basically who’s the sender, what’s their account number,
- what’s their physical address,
- what’s the beneficiary’s name,
- what’s their account number,
- so on and so forth, basically,
- putting a lot of the requirements that exist
- in the traditional banking financial services world
- into the digital assets world.
- And that is not very easy
- because, frankly, in many cases,
- it’s like taking a horse
- and trying to fit it into a car and to make the engine run.
- It doesn’t work very well, but this is why there’s a lot of,
- actually, industry now talks on how best
- the digital assets space can satisfy these requirements,
- but at the same time, do it in a way that
- leverages the latest technology
- and frankly, is more appropriate for new developments,
- like blockchain and digital assets.
- One other big development, as
- well, that is worth to watch,
- is what’s happening on a tax and accounting side.
- While you may thing we’re getting there
- when it comes to regulatory developments,
- but I can tell you, when it comes to regulations,
- when it comes to accounting and
- tax, we’re still way behind.
- And that’s also quite important
- because in order for people
- to use digital assets, regulators have to make it clear
- whether any tax are due on some of these transactions,
- but also, what are the accounting standards
- and how, actually, from an accounting perspective,
- you need to look at digital assets.
- ‘Cause if you think about it, double-entry accounting,
- that was created a couple hundred years ago,
- was not necessary forecasting things like bitcoin
- that were going to pop up couple hundred years later.
- This is why it’s going be very interesting to see
- what’s going to happen when it
- comes to accounting standards,
- standard setters, especially when it comes to topics
- like audits, for example,
- that is still a requirement legally in many countries.
- And these are some of the big developments going on
- right now in the broader digital assets ecosystem.
- That’s all I had in time with you guys all today,
- but hopefully, this is exciting and insightful,
- and it was a pleasure sharing with you all
- some of the trends happening on the regulatory front.
6.7 Virtual Asset Custodian Regulation (Urszula McCormack, King & Wood Mallesons Partner)
- Hi, my name is Urszula McCormack
- and I’m a partner of King & Wood Mellesons
- here in Hong Kong.
- I have two particular focus areas.
- I have focus on financial technology
- and financial crime
- and I’ve had a particular interest
- in virtual assets and blockchain for quite some time.
- I also sit on the FSC’s FinTech advisory board
- and a very happy participant
- of many associations here and abroad.
- Today I am going be speaking to you
- about the regulation of virtual asset custody.
- And there are three things that are relevant to this.
- What custody means for virtual assets.
- What the custodian actually does.
- And where this all happens.
- So what does custody mean for virtual assets?
- It means controlling the private key.
- That is, the string of letters and numbers
- that binds with the public key
- and allow a transaction to occur.
- Now, this private key could be in a few different forms.
- It could be electronic, on a laptop,
- on a mobile phone,
- on a physical hardware wallet,
- or even on a piece of paper
- or etched into a gold bar.
- So custody can also involve controlling something
- that holds the private key.
- For example, I might only be a custodian
- for the safe deposit box
- that contains your piece of paper
- that contains the private key.
- Increasingly, there are also self-custody software
- and hardware solutions
- that assist with key management.
- They can be quite simple
- or they might help you split a private key
- into multiple pieces,
- so that different people hold different parts
- and have to come together
- to direct the transaction.
- Self-custody solutions tend not to be regulated
- as a custody service,
- because technology itself is generally not regulated
- but you have to carefully examine
- the precise technology,
- contracts and laws involved
- to make sure that’s the case.
- The next point we consider
- is what the custodian actually does.
- And this is generally governed by
- what the custodian agrees to do in a contract,
- but sometimes this could be implied
- by law or even imposed by regulators.
- And there are six typical things that a custodian does.
- The three core functions are: (1) to hold the asset,
- (2) is to protect the asset,
- usually through segregation from other assets,
- cybersecurity and operational controls,
- and now increasingly through insurance.
- (3) And the third function
- is to move the asset on instruction,
- this could be a transaction-by-transaction instruction
- or under a standing authority
- But many custodians go beyond that role,
- they may, for example,
- (4) analyse the asset and certain patterns that occur.
- (5) They might manage the asset
- and even invest it for you
- or (6), they could use the asset themselves,
- and potentially even profit from it,
- if that’s the agreement that you have struck,
- for example, instead of paying fees.
- Now, depending on where this is all happening,
- where it is being marketed,
- different regimes apply
- to these custody services.
- And yes, the regulations are different.
- However, there’re some general themes.
- First of all, direct regulation
- of virtual asset custodians is increasing.
- The core obligations that are typically imposed
- on custodians directly include
- licensing, being fit and proper,
- conducting AML/KYC controls
- and complying with ongoing prudential standards.
- If the custodian also invests the virtual asset
- and manages it for you,
- then it’s very common for a different regulatory regime
- to apply as well.
- For example, in Hong Kong,
- the Companies Registry TCSP licensing regime applies
- to trust and company service providers,
- serves custodians,
- but the Securities and Futures Ordinance
- could also kick in if the custodian
- is managing virtual assets that include securities.
- A similar approach applies in the UK and Singapore,
- but things are rapidly developing.
- There is also indirect regulation
- of virtual asset custodians.
- What this means is that regulated entities
- that use custodians as part of their business
- are subject to strict rules
- about how the virtual assets are held.
- This could include things like
- making sure the custodian
- is regulated in a certain way,
- that the assets are appropriately
- segregated and protected,
- and potentially also insured,
- that specific technology standards are applied
- and that there are specific rules applied
- to hot versus cold storage and other things.
- Again, taking Hong Kong as an example,
- the Securities and Futures Commission
- has issued guidance for fund managers
- that use virtual assets
- as part of their business
- and those standards include custody rules.
- The SFC’s conceptual framework
- for exchanges also has rules regarding custody.
- In both cases,
- each party’s also subject to the general law.
- This includes not laundering money
- or financing terrorism,
- complying with privacy law,
- thinking through bankruptcy and insolvency rules,
- complying with consumer protection laws
- and considering how trust law might inform
- the obligations that the custodian has.
- So what is happening globally?
- There are two key developments.
- First of all, the Financial Action Task Force,
- the international standards setter
- for anti-money laundering, counter-terrorist financing,
- has formally recommended
- that all virtual asset service providers,
- including custodians, be regulated and subject
- to the world of FATF AML/KYC requirements,
- including customer due diligence,
- screening and monitoring, and so on.
- Secondly, there are many virtual asset-specific laws
- and regulations emerging.
- Malta, Japan and Bermuda are three examples of this,
- and Bermuda also provides one of the most detailed
- Codes of Practise issued so far.
- Now, I also recommend keeping an eye out
- for industry developments.
- Associations such as
- the Hong Kong FinTech Association,
- ASIFMA and Global Digital Finance
- are producing excellent practise guides.
Module 6 Reference Reading
References and Suggestions for Further Reading in Module 6
- Masarch Paquet-Clouston et al., “Ransomware payments in the Bitcoin ecosystem”, Journal of Cybersecurity, 5(1), 2019.
- Rolf van Wegberg et al., “Bitcoin money laundering: mixed results? An explorative study on money laundering of cybercrime proceeds using bitcoin”, Journal of Financial Crime, 25(1), 2018.
- David Lee Kuo Chuen et al., “Cryptocurrency: A new investment opportunity?”, Journal of Alternative Investments, 20(3), 16-40, 2018.
- K. Krombbolz et al., “The other side of the coin: User experiences with bitcoin security and privacy”, In Proceedings of Financial Cryptography and Data Security, 20th International Conference (FC 2016), p.555-580, 2017.
- A.F. Neil Gandal et al., “The impact of DDOS and other security shocks on Bitcoin currency exchanges: Evidence from Mt. Gox”, Proceedings of the 15th Annual Workshop on the Economics of Information Security, abs/1411.7099, 2016.
- Andres Guadamuz and Christopher Marsden, “Blockchains and Bitcoin: Regulatory responses to cryptocurrencies”, First Monday, 20, 2015.
